Gcore Radar Q1–Q2 2025: three insights into evolving attack trends
- September 23, 2025
- 2 min read

Cyberattacks are becoming more frequent, larger in scale, and more sophisticated in execution. For businesses across industries, this means protecting digital resources is more important than ever. Staying ahead of attackers requires not only robust defense solutions but also a clear understanding of how attack patterns are changing.
The latest edition of the Gcore Radar report, covering the first half of 2025, highlights important shifts in attack volumes, industry targets, and attacker strategies. Together, these findings show how the DDoS landscape is evolving, and why adaptive defense has never been more important.
Here are three key insights from the report, which you can download in full here.
#1. DDoS attack volumes continue to rise
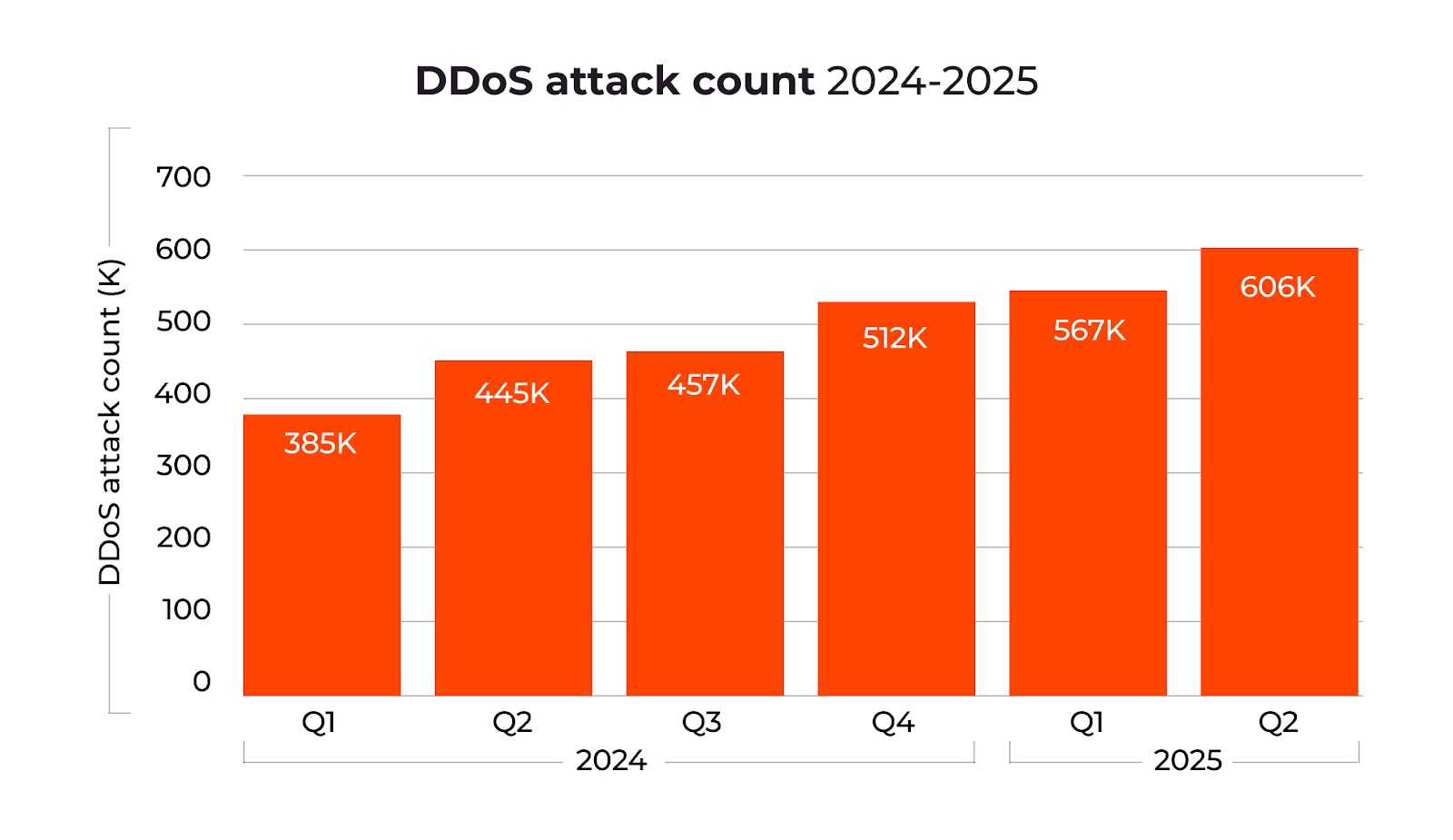
In Q1–Q2 2025, the total number of DDoS attacks grew by 21% compared to H2 2024 and 41% year-on-year.
The largest single attack peaked at 2.2 Tbps, surpassing the previous record of 2 Tbps in late 2024.
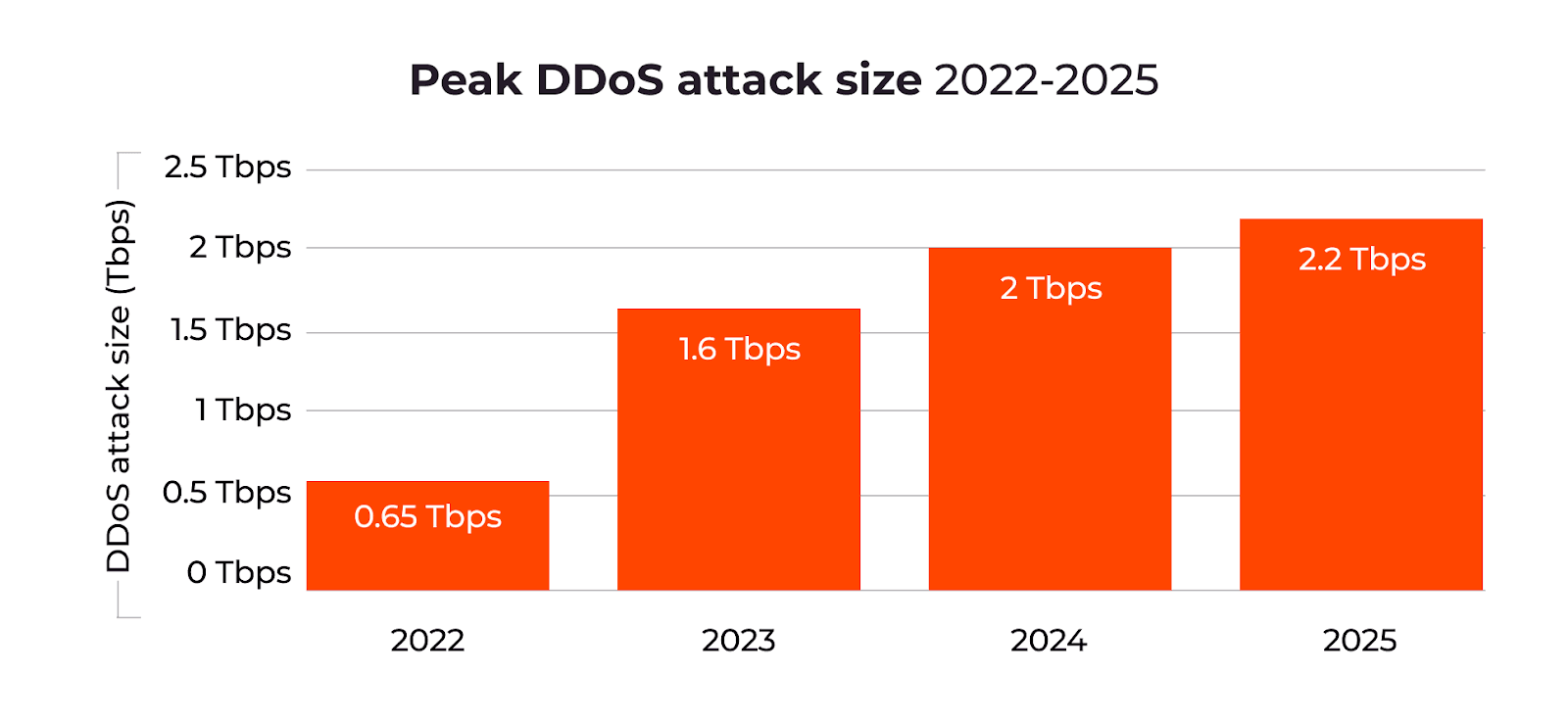
The growth is driven by several factors, including the increasing availability of DDoS-for-hire services, the rise of insecure IoT devices feeding into botnets, and heightened geopolitical and economic tensions worldwide. Together, these factors make attacks not only more common but also harder to mitigate.
#2. Technology overtakes gaming as the top target
The distribution of attacks by industry has shifted significantly. Technology now represents 30% of all attacks, overtaking gaming, which dropped from 34% in H2 2024 to 19% in H1 2025. Financial services remain a prime target, accounting for 21% of attacks.
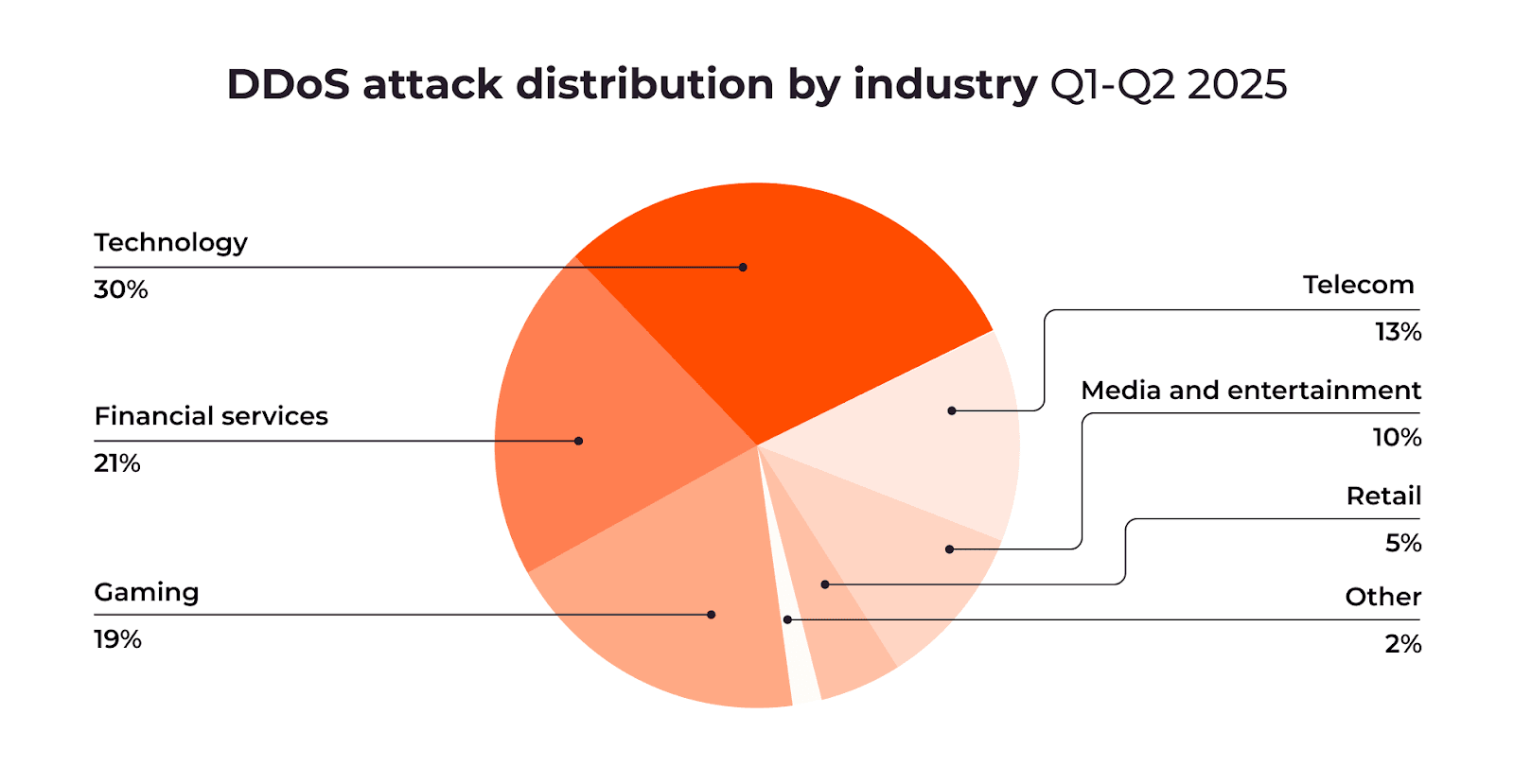
This trend reflects attackers’ growing focus on industries with broader downstream impact. Hosting providers, SaaS platforms, and payment systems are attractive targets because a single disruption can affect entire ecosystems of dependent businesses.
#3. Attacks are getting smarter and more complex
Attackers are increasingly blending high-volume assaults with application-layer exploits aimed at web apps and APIs. These multi-layered tactics target customer-facing systems such as inventory platforms, payment flows, and authentication processes.
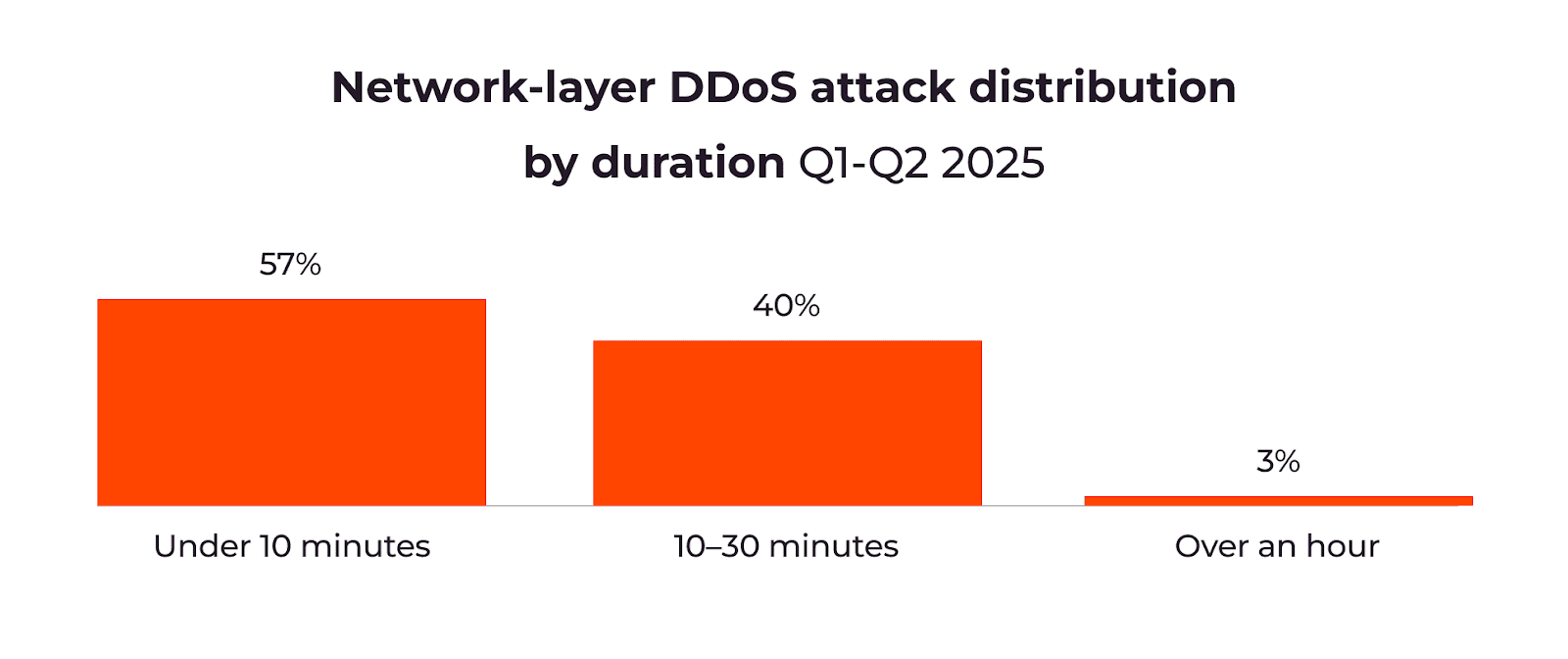
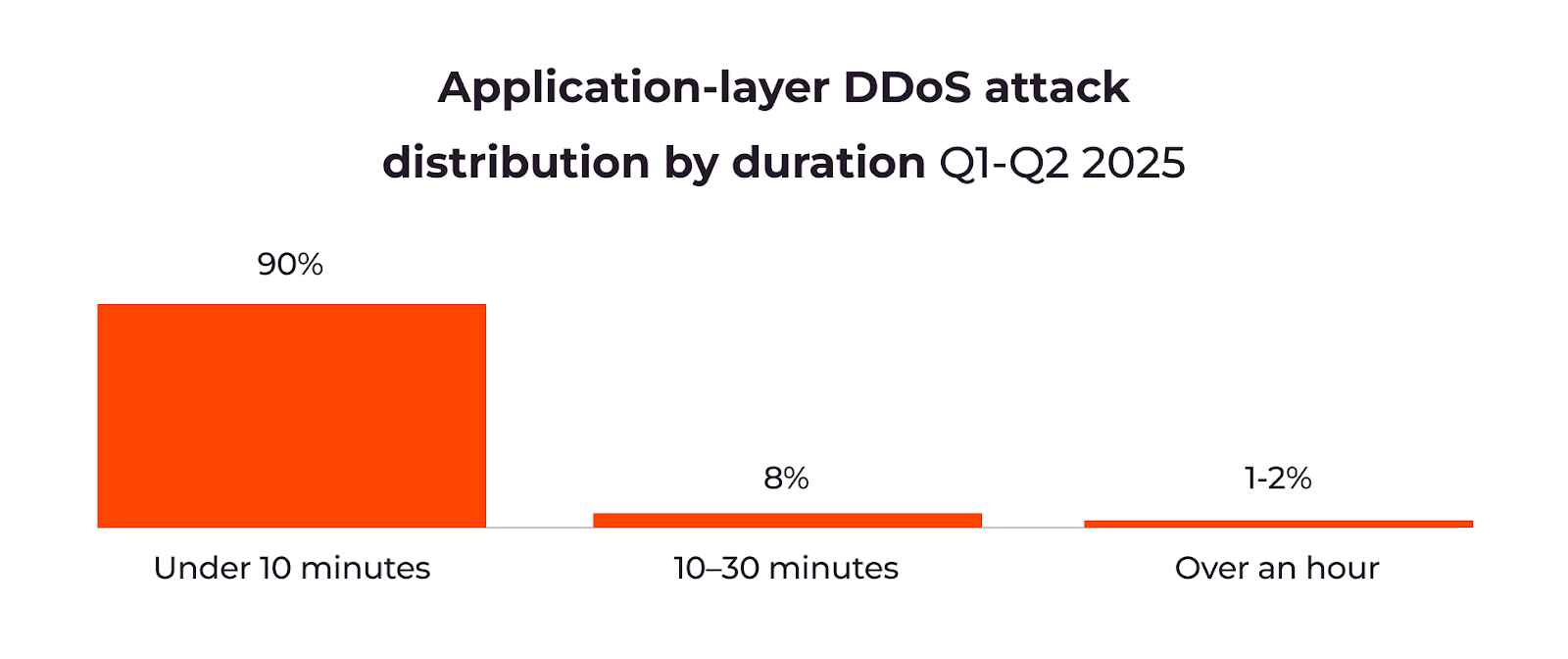
At the same time, attack durations are shifting. While maximum duration has shortened from five hours to three, mid-range attacks lasting 10–30 minutes have nearly quadrupled. This suggests attackers are testing new strategies designed to bypass automated defenses and maximize disruption.
How Gcore helps businesses stay protected
As attack methods evolve, businesses need equally advanced protection. Gcore DDoS Protection offers over 200 Tbps filtering capacity across 210+ points of presence worldwide, neutralizing threats in real time. Integrated Web Application and API Protection (WAAP) extends defense beyond network perimeters, protecting against sophisticated application-layer and business-logic attacks. To explore the report’s full findings, download the complete Gcore Radar report here.
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.






