Security
News
Mitigate DDoS attacks with geography-based Rate Limiter
- November 24, 2022
- 1 min read

Rate Limiter is a Gcore Web Application DDoS Protection feature that allows you to block traffic by IP addresses from specific countries.
To determine the geographical location of IP addresses, we use a database that matches countries with IP addresses allocated for them. That way, if you’re subjected to DDoS attacks from particular countries, you can block traffic from them with Rate Limiter.
How to use our geography-based Rate Limiter
Configure this countermeasure against traffic from one or several specific locations. Rate Limiter can perform two actions based on your choice:
- Allow traffic
- Block traffic
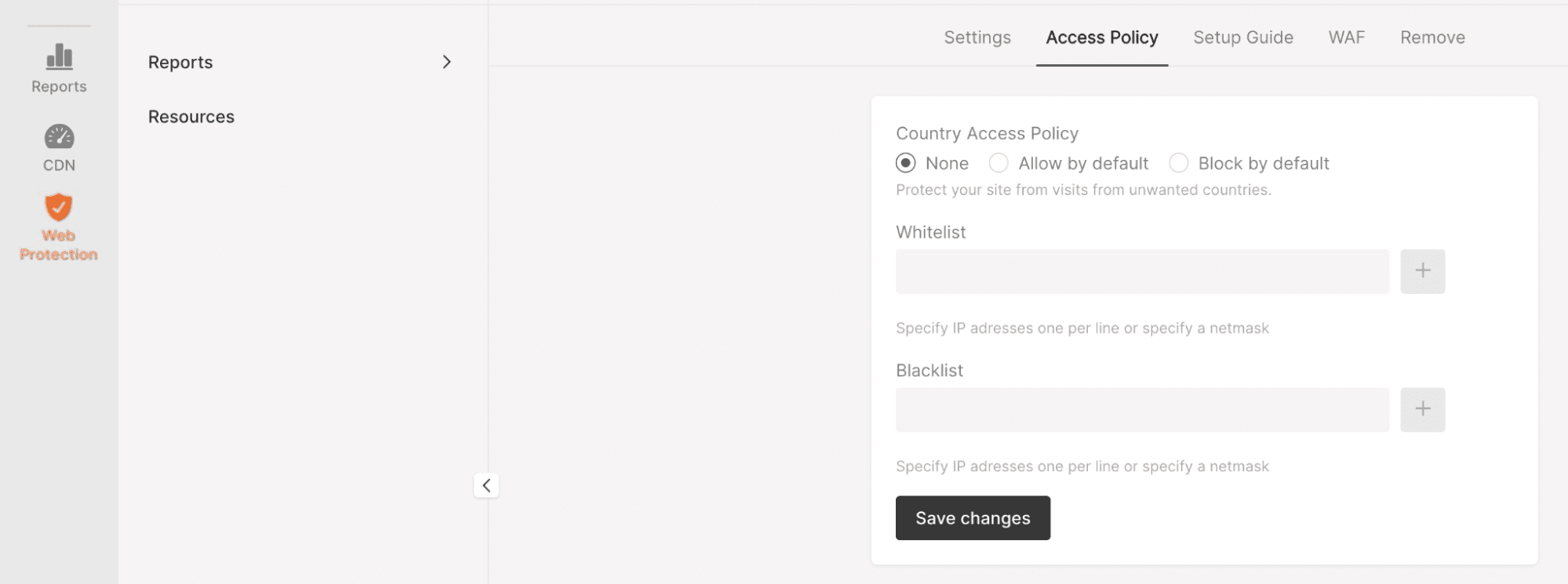
That means you can use one of two strategies:
- List the source countries from where traffic should be allowed and block traffic from other countries.
- List the source countries from where traffic should be blocked and allow traffic from other countries.
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.






