Global CDN service: fast, flexible content delivery.
Make your app fast and responsive for a global audience with Gcore CDN. 210+ PoPs, 200+ Tbps capacity, 30 ms average latency worldwide.
Speed up your websites, applications and downloads
Your content delivery, before and after Gcore CDN:
110 ms
Before - High latency
20 ms
After - Ultra-low latency

Why businesses choose Gcore as their CDN provider
Low latency worldwide
Your users reach your app as if the hosting is always in the same location as they are. 210+ PoPs across six continents bring your content closer to every visitor.
Dynamic content acceleration
Web applications become smoother and more responsive. Gcore speeds up delivery of dynamically generated content, not just static assets.
Outstanding availability
Your servers stay protected from overloading during unexpected traffic surges or DDoS attacks. Built-in protection keeps your app online when it matters most.
Global network built for performance
We invest in our global network so you don't have to buy expensive infrastructure.
210+
Points of presence worldwide
200+
Tbps network capacity
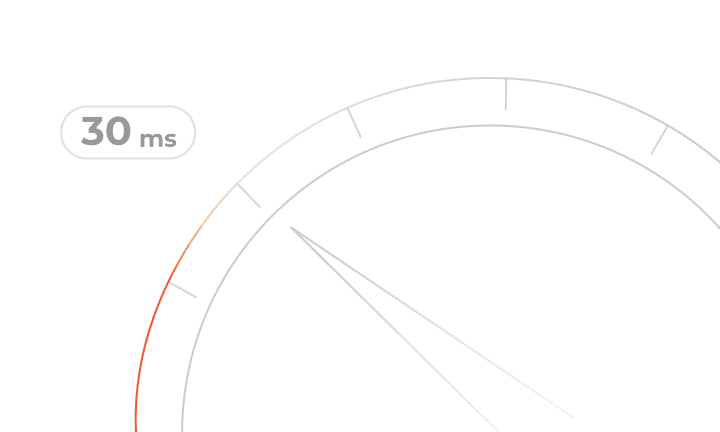
30 ms
Average latency worldwide
85%
Average cache hit ratio
2M
Requests handled per second
Built-in web security
SSL/TLS Encryption
Secure connections for all your traffic with automatic certificate management
Advanced access policies
Fine-grained control over who can reach your content with customizable rules
L3, L4, L7 DDoS mitigation
Multi-layer protection against volumetric and application attacks
Next-gen WAF
Intelligent firewall to block threats before they reach your app
Built for your workload
Web Applications & E-commerce
Deliver fast, secure shopping experiences to customers everywhere with improved website speed and dynamic asset acceleration.
Games & Software Assets
Distribute patches, updates, and game assets across the globe without bottlenecks using our 200 Tbps network capacity.
Video Streaming CDN
Deliver stutter-free video experiences from live broadcasts to VOD libraries with 0.5-4s latency for real-time broadcasting.

Optimized for video streaming
Gcore CDN is an optimized solution for video-on-demand (VOD) and live streaming that delivers professional-grade performance.
- 4K ready - Deliver stutter-free playback, even for 4K video
- 0.5-4s latency - Near real-time broadcasting for live events
- 10M viewers - Protect your server during peak user activity
Image optimization as a service
Image Stack by Gcore is a cloud-based image optimization tool. Cut bandwidth costs and improve user experience by applying small changes in URL query strings and your website settings.
- Convert to WebP, AVIF - Up to 85% file size savings at given quality
- Control image quality - Balance webpage load speed and CDN traffic
- Resize and crop images - Optimize images dynamically via query strings
CDN features and technical specifications
Performance & Protocols
Modern protocols for faster delivery
- HTTP/3 (beta) and HTTP/2 support
- TLS 1.3 with 0-RTT for faster handshakes
- Anycast and GeoDNS routing
- Dynamic content acceleration
- WebSockets support
- Brotli and Gzip compression
- Custom IP & ASN (BYOIP)
Intelligent Caching
Smart caching for optimal performance
- Purge by URL, file, or directory
- Content prefetching
- Cache sharding for lower latency
- Always online (Serve stale) on origin failure
- Customizable TTL
- Large file delivery optimization
Origin Protection
Comprehensive security and access control
- Origin shielding and origin groups
- Origin validation using SSL
- Secure token authentication
- Access control lists
- CORS headers support
- Forced redirect to HTTPS
- SNI support and TLS version control
Monitoring & SSL
Full observability and security
- Detailed statistics and usage reports
- Raw logs export
- Built-in log viewer
- Traffic consumption control
- Free Let's Encrypt SSL
- Custom SSL certificate support
- Custom domain mapping
CDN API and DevOps integrations
Gcore CDN is ready to complement and enhance your infrastructure's automation. Extended API allows you to benefit from CDN without impacting your regular operations.
- Terraform integration - Infrastructure as code support
- Grafana monitoring - Real-time performance dashboards
- Programmatic management - Configure rules and monitor performance via API
Trusted by experts
























For security and scalability reasons, we decided right away that we wanted to entrust the delivery of our customers’ videos to a reputable CDN provider. We settled on the infrastructure of Gcore and don’t regret our choice.
Nathan Ihlenfeldt, Technical Director at Stage Audio Works

We managed to transfer all our resources without any problems. Our users did not notice any changes. Thanks to Gcore, we achieved the results we expected and saved over 40% on CDN infrastructure in a year.
David Salz, exCo-founder and exCTO of Sandbox Interactive

I want to be able to quickly deliver content to my visitors, and Gcore does a great job of this.
Ethan Cheong, Managing Director at Shopcada