Tunneling helps your private data travel securely on the internet. Understanding tunneling can help you understand how internet data security works, enabling you to better safeguard your data and privacy.
What Is Tunneling?
Tunneling—also referred to as port forwarding or network tunneling—is the process of transmitting private network data through a public network securely and efficiently. Imagine a protected tunnel, stretching from your house (private network) to your favorite store (destination/local network) amidst a bustling city (public network.) Your train (data) carries valuable cargo (your information) that needs to be protected from prying eyes.

With tunneling, this train enters the protected tunnel from your home, travels securely across the city via a tunnel, and finally arrives at the store, escaping the notice of city residents other than yourself. Tunneling keeps your data safe and protected from prying eyes as it travels to its destination.
Why Tunneling Matters: Tunneling as Part of Networking
A network is a system of two or more connected devices, and networking is the practice of connecting these devices together so they can share resources and information. Tunneling is the part of networking that facilitates secure and efficient data transmission. It allows connected systems to communicate and collaborate safely and securely over public networks.
One major benefit of tunneling is that it allows remote workers and field teams to safely work offsite without compromising personal or organizational security. A remote worker can safely access a private corporate network via the internet. For example, they can safely connect to HQ and then access, submit, and download sensitive files by using secure tunnel connections provided by the company.

Network Tunneling Use Cases
Tunneling has a wide range of applications including:
| Use Case | Description |
| Multi-site collaboration | Collaborate in real time and securely share data across remote physical locations—important for geographically distributed companies and remote workforces. |
| Remote support | Safely provide technical support and troubleshooting assistance to remote users, customers, and systems. |
| Network monitoring | Monitor and enforce network segmentation compliance for safe and secure transmission of sensitive business data. |
| Disaster recovery | Easily regain access to and control of your IT infrastructure after an incident by establishing backup channels between data centers. |
| Responsible healthcare record handling | Safely share healthcare records between and among providers. Healthcare records are among the most targeted records in data breaches. |
| Safe supply chain management | Securely manage your supply chain interactions and communications with vendors, suppliers, and partners. |
| Secure ecommerce transactions | Establish secure channels for processing ecommerce payments, gaining customer trust and loyalty. |
| Bypass geo-restrictions and censorship | Easily bypass unfavorable geo-restrictions and censorship to safely access business-critical services. (By encapsulating your internet traffic within another layer of data that is encrypted, it’s difficult for ISPs or government agencies to determine the actual content or destination of your data. Your original IP is masked, making it appear as if you are accessing the internet from a location without restrictions.) |
| Improved VoIP call quality and safety | Overcome poor voice quality, dropped calls, and security breaches when using Voice over Internet Protocol (VoIP) to make calls over the internet. (Tunneling reduces the risk of packet loss, latency, and jitter, as the encapsulated data can be prioritized for efficient transmission. Encryption provided by the tunnel ensures that the call is secure from eavesdropping.) |
| Enhanced gaming security | Improve security, especially for peer-to-peer (P2P) games such as Fortnite, where one player sets up the server and others connect remotely. |
How Does Tunneling Work?
Tunneling involves six key processes: encryption, encapsulation, header addition, transmission, decapsulation, and decryption. These processes occur for both outgoing and incoming traffic.
- Encryption: Bits of data known as “packets” are encrypted to ensure security and privacy during transmission.
- Encapsulation: Encrypted data packets are encapsulated within a public network protocol, a set of rules that govern communication and data transmission on a network, and become the “payload”—the data being securely transmitted.
- Header addition: A header specifies one end of the secure tunnel as the originating point and the other as the destination. During encapsulation, a packet of encrypted data is enveloped by a wrapping protocol which adds a header. In simple terms, this step means that the header tells the data where to go.
- Transmission: The encapsulated (disguised) packet traverses the public network unnoticed.
- Decapsulation: On reaching the local network, the data undergoes decapsulation. Decapsulation is the process where the added header is removed, and the original encrypted data packet is extracted.
- Decryption: The extracted data packet is decrypted and then delivered to its intended destination IP address.

What Is Packet Encapsulation?
In step two of the tunneling process, above, we encountered packet encapsulation. This is a key aspect of tunneling, so let’s explore it in depth.
Packet encapsulation involves adding supplementary header (and sometimes also trailer) information to the original packet. This is referred to as “wrapping” one data packet within another data packet.
Encapsulation ensures proper routing and protocol compatibility and interoperability. When data is transmitted through a network, it is broken into smaller units referred to as packets, datagrams, segments, blocks, cells, or frames.
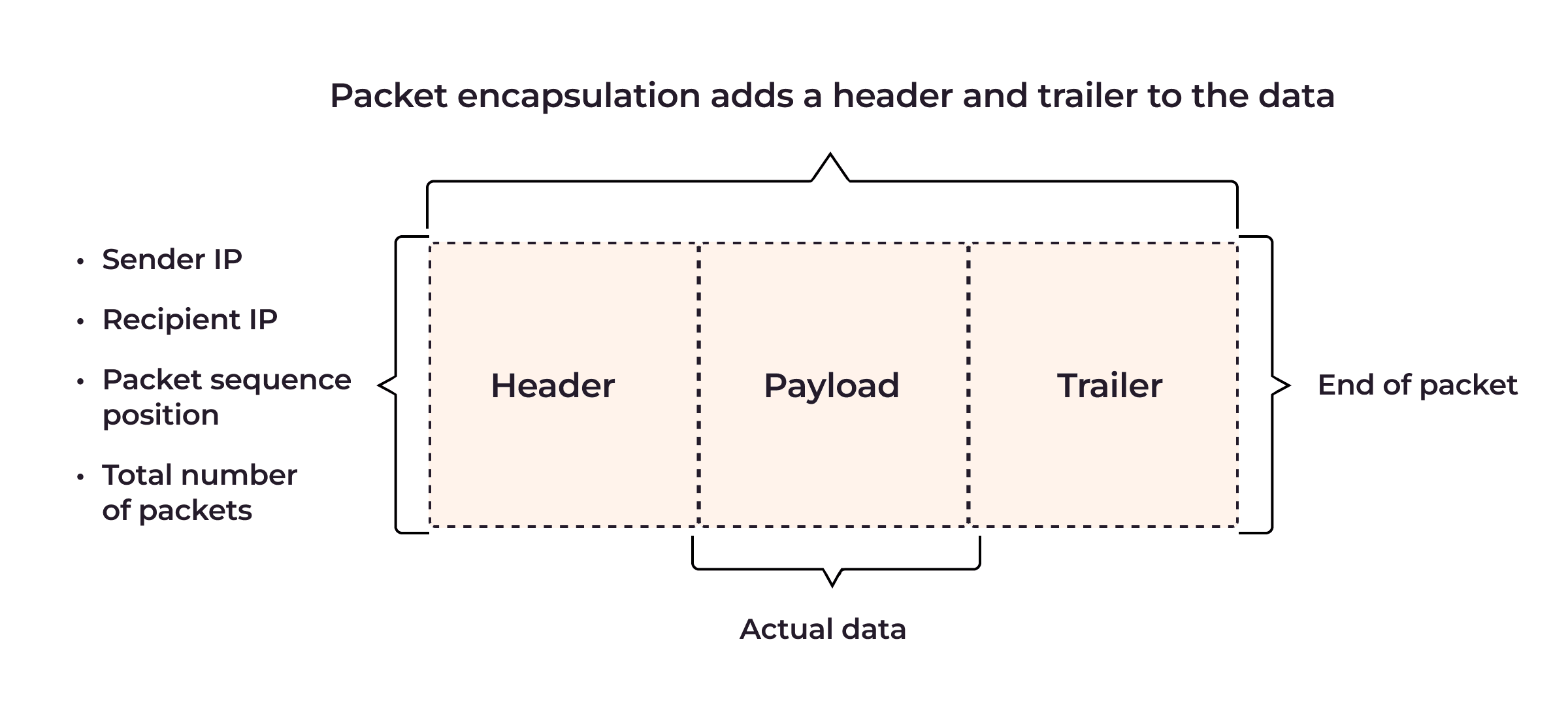
Each data packet comprises a header and a payload. The header contains essential information such as the source address, destination address, protocol type, and packet number, allowing routers and switches to route the packet efficiently to its intended destination. The payload contains the actual content or original data. The trailer provides additional data integrity and error-checking information.
How Does Packet Encapsulation Work?
Packet encapsulation in tunneling can be explained using the Open Systems Interconnections (OSI) model, a seven-layer conceptual framework that describes how data moves through a network.



Here’s how packet encapsulation works in tunneling based on the OSI model:
- Application data (Layer 7) gains a TCP header at the transport layer (Layer 4,) turning it into a TCP segment.
- This TCP segment receives an IP header at the network layer (Layer 3,) becoming an IP packet with source and destination addresses.
- The IP packet is wrapped in an Ethernet frame at the data link layer (Layer 2,) adding MAC addresses and other transmission details.
- Finally, this Ethernet frame is converted to bits at the physical layer (Layer 1) for network transmission.

During decapsulation, these layers are peeled off in reverse as the data ascends the OSI layers, restoring the original application data.
Benefits of Packet Encapsulation
Packet encapsulation serves purposes such as:
- Promoting network compatibility: By encapsulating data packets at different layers, packet encapsulation facilitates network/protocol coexistence.
- Enhancing data security and privacy: Encapsulation protects private network data from unauthorized access and potential threats, enhancing data security and privacy.
- Bypassing network restrictions: Encapsulation allows data to evade network nodes and bypass firewalls, effectively overcoming known network restrictions.
- Logical separation and network performance optimization: Encapsulation aids logical separation and segmentation within a network, leading to improved network performance, and simplified network monitoring and analysis.
- Simplifying network monitoring and analysis: Encapsulation provides structured headers and metadata, facilitating network monitoring and analysis for efficient troubleshooting and maintenance.
However, adding additional headers and metadata increases data packet size, leading to higher bandwidth consumption and transmission times, which may cause latency or lags.
Types of Tunneling
Tunneling refers to the entire process of encryption, encapsulation, and transmission. There are three main types of tunneling: GRE tunneling, split tunneling, and VPN tunneling.
GRE Tunneling
Generic Routing Encapsulation (GRE) tunnels enable secure, virtual point-to-point connections across diverse networks using two endpoint routers. Compatible with various network layer protocols in the OSI model, they easily integrate with existing networks and public clouds. They support multicast, broadcast, and dynamic routing protocols like OSPF and EIGRP, making them versatile for different network configurations.
How GRE Tunneling Works
Here’s how GRE tunneling works; you’ll notice it follows the basic network tunneling process described above.
- Establishment of GRE tunnel: Two endpoints, typically routers, establish a GRE tunnel while maintaining a physical or logical connection to the host network.
- Packet encapsulation: Data packets for transmission from point A to point B are encapsulated, or wrapped, within GRE packets. The original packet becomes the payload of the GRE packet.
- Header addition: The GRE packet adds a new header containing essential metadata such as the protocol type and routing information.
- Routing: The encapsulated packet is routed through the intermediate network (such as the internet) to reach the other endpoint of the tunnel.
- Decapsulation: At the other endpoint of the tunnel, the GRE packet header is removed (decapsulated) and the original packet extracted.
- Delivery: The original data packet is sent to the local network, where a destination device can read the original data.
What are the pros and cons of GRE Tunneling?
The advantages of GRE lie in its versatility and adaptability.
- Protocol agnostic: Carry packets from multiple different network layer protocols, making them highly versatile.
- Easy Integration: Seamlessly integrate with existing network setups, including legacy systems, private networks, and public clouds.
- Routing support: Compatible with dynamic routing protocols like OSPF and EIGRP, allowing for more intelligent and efficient routing decisions.
- Multicast and broadcast support: Handle multicast and broadcast traffic, facilitating efficient data transmission to multiple network nodes.
- Simple setup: Typically requires less configuration and administrative overhead compared to other tunneling protocols.
- Flexibility: Can be combined with other protocols for added security and functionality.
However, GRE tunneling lacks built-in encryption, making it vulnerable to potential threats such as eavesdropping, tampering and modification, and replaying attacks. To address such security concerns, GRE tunneling can be integrated with additional security protocols. GRE packets that exceed Maximum Transmission Unit (MTU) and Maximum Segment Size (MSS) may require fragmentation before transmission. These processes require extra compute power, which can result in increased latency and slower packet delivery times.
Split tunneling
Split Tunneling, or Split VPN Tunneling, is another network routing technique that allows the division of network traffic between a secure connection and the open internet, via a VPN. Split tunneling helps to optimize security, performance, and resource allocation.
Typically, a VPN routes all its traffic through its encrypted connection, ensuring higher level security but potentially increased latency due to the additional encryption process. Split tunneling addresses this by offering businesses a secure VPN connection and direct access to the open internet.
How Split Tunneling Works
Here is how split tunneling works:
- VPN setup: A secure connection to a private network is established using a VPN client.
- Traffic split: Some network traffic is directed through the encrypted VPN tunnel, while other traffic accesses the internet directly.
-
- Encryption: The traffic going through the VPN tunnel is encrypted for security.
- Direct access: Non-sensitive activities like internet browsing bypass the encrypted tunnel for faster speeds.

Pros and Cons of Split Tunneling
Split tunneling offers both benefits and security risks. It enhances network efficiency by allowing users to access both secure and non-secure resources simultaneously, reducing the load on the VPN server. By doing so, it improves connection speeds for non-sensitive tasks, as this traffic bypasses the encrypted VPN tunnel, leading to faster internet browsing and lower latency.
However, it can potentially create backdoors for threats by allowing users to bypass network controls. Proxy tampering and VPN bypass also weaken corporate traffic monitoring. To mitigate risks, organizations should enforce strict traffic filtering, encryption, and robust access controls. Proper security measures strike a balance between performance and security, safeguarding both the network and user activities.
VPN Tunneling
A VPN tunnel provides a secure, encrypted connection over a public network, enabling users to access private network content safely through the Internet. VPN tunneling is widely used by companies to connect with remote teams or branch offices securely.
How VPN Tunneling Works
Here is how VPN tunneling works:
- Connection request: A VPN client software or device sends a connection request to a VPN server, which is usually part of a distributed private network.
- Tunnel creation: After successful authentication, a secure virtual tunnel is established between the client and server, allowing them to communicate and transmit data securely.
- Encryption: The VPN client encrypts the user’s network traffic.
- Encapsulation: The encrypted network traffic is encapsulated within another packet/protocol, which includes a header and payload.
- Tunneling: The encapsulated packet is then tunneled through the public network, such as the Internet, to reach the VPN server.
- Decapsulation and decryption: Upon reaching the VPN server, the encapsulated packet is decapsulated and decrypted, revealing the original data.
Pros and Cons of VPN Tunneling
VPN tunneling is beneficial for security, privacy, remote access, bypassing geographical restrictions, and network segmentation. Nevertheless, it has limitations. Resource intensive tasks like encryption/decryption and encapsulation/decapsulation can result in latency, leading to reduced speed and performance, especially when VPN servers are located afar.
While VPNs offer a high level of privacy and anonymity, they do not guarantee 100% tracking protection. Browsing behavior and social media activity can still be monitored, and some VPN may keep access logs, potentially compromising user data if pressured by authorities. Trusted VPN services with a zero-logs policy may come at a cost, and VPN usage is restricted or banned in some countries and by certain essential services like banking.
Comparing GRE, Split, and VPN Tunneling
This table compares GRE tunneling, split tunneling, and VPN tunneling.
| Criteria | GRE tunneling | Split tunneling | VPN tunneling |
| Setup | Straightforward | Varying complexity | May involve more complex setup and management |
| Security | Lacks built-in security features but can integrate with security protocol like IPsec, SSL, TLS | Secure tunnel-only encryption | Secure with full encryption |
| Protocol | GRE protocol for encapsulation | Based on routing configuration | Can use IPsec, SSL, or TLS for encryption and encapsulation |
| Traffic handling | All network traffic sent through tunnel | Traffic is split between tunnel and the Internet | All traffic encrypted and sent through tunnel |
| Network visibility | Limited visibility into local network traffic | Local network resources visible while connected to tunnel | Private network resources are accessible |
| Impact | Minimal overhead with some latency | Depends on number of split tunnels, can result in increased latency | Additional processing needed, resulting in increased latency |
| Use case | Point-to-point VPN | Balancing network performance and resource optimization | Remote access, bypassing restrictions, enhanced privacy |
Whatever your preferred tunneling technique, tunneling is an effective measure in shielding servers and networks from incoming malicious traffic.
How to Protect Against Tunneling Attacks
Tunneling techniques can be exploited in attacks like DNS tunneling to create covert channels that bypass security measures, compromising network integrity. To safeguard against these multi-layer attacks, various effective mitigation measures are essential:
- Web application firewall (WAF): Implementing a WAF provides comprehensive application layer and API protection against tunneling-based threats. WAFs scan and filter incoming traffic, blocking malicious traffic and protecting your web server. Gcore’s advanced WAF utilizes machine-learning techniques and real-time monitoring to defend applications and APIs, acting as a first line of defense against tunneling-based attacks. It also scans resources in real time to find potential vulnerabilities.
- Bot protection: Botnets and malicious bots can exploit encrypted tunnels to execute DDoS attacks and other malicious activities. Gcore offers comprehensive Bot Protection, effectively detecting and mitigating aggressive bot activity, across the network, transport, and application layers, including web scraping, API scraping, account takeover, TLS session attacks, and form submission abuse.
- GRE tunnel: A GRE tunnel establishes a secure, private connection between network endpoints or routers, providing protection against brute force and GRE DDoS attacks in cases where there’s no point of presence (PoP) in client server location. Gcore’s global server network and scrubbing centers power GRE tunnels, offering fast and highly secure connections.
- DNS protection: DNS-based attacks, such as DNS tunneling, can be difficult to detect, as DNS resolvers may be compromised and exploited for tunneling attacks. Gcore’s free, public DNS resolvers offer fast, secure, low-latency services, leveraging our 150+ node Anycast network for robust DNS protection. Combined with Gcore’s DNS hosting service, we provide reliable protection against DNS-related tunneling threats.
Conclusion
Tunneling plays a crucial role in establishing secure network connections, enabling organizations to maintain the confidentiality, integrity, and availability of their key data. Whether for remote teams or overall network security, the right tunneling solution is essential to ensure a robust and protected networking environment.
Gcore’s tunneling services offer a comprehensive approach to network protection, leveraging the advantages of a public network’s wide coverage while ensuring the security and privacy of a local network. By utilizing Gcore’s WAF and Bot Protection, and GRE tunneling, businesses can provide safe and uninterrupted 24/7 access to critical company resources, enabling seamless and secure communication across the network.
Sign up to get started for free!
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.