HTTP, also known as Hypertext Transfer Protocol, serves as a language for your browser and web server to communicate over the internet. Every action on the Internet, from searching for recipes to online equity trading—you can do it thanks to HTTP data transfer. Although it is good to know how important HTTP is for successful data communication on the World Wide Web, it has one significant flaw: it is not secure. That’s where HTTPS (Hypertext Transfer Protocol Secure) comes into play. HTTPS is a secure protocol that uses encryption to protect the data transmitted between your browser and the server.
In this article, we’ll compare and contrast the differences between HTTP and HTTPS. Additionally, you’ll learn about the basics of HTTP and why it is not secure. By the time you finish reading, you will fully understand the importance of using HTTPS to secure your website and application.
Key points about HTTP
HTTP is a communication protocol. It enables the exchange of information between clients and servers over the internet, using a request-response model where the client (typically a web browser) sends an HTTP request to the server, and the server responds with an HTTP response.
For example, once you visit a website and type the URL in the browser, the browser sends an HTTP request to the server, which then sends back the requested web page.
HTTP is a stateless protocol. The protocol itself does not retain any information about previous requests—it doesn’t “remember” at end points and therefore each request from the client is treated as new. That being said, services using HTTP require the ability to associate multiple requests from the same browser and cookies function as unique identifiers stored in browsers to help applications retrieve session data.
For example, when you bypass entering login credentials while visiting the same site repeatedly—that’s a cookie in action (and HTTP is transferring that info unencrypted, which we address in the next section).
HTTP is a text-based protocol. HTTP uses a set of standardized messages to facilitate communication between clients and servers. These messages include HTTP methods (such as GET, POST, PUT, and DELETE) and status codes (such as “200 OK,” “404 Not Found,” and “500 Internal Server Error”). We’ll dive into these concepts in more detail later.
For example, when you click a link on a web page, the browser sends an HTTP GET request to the server to retrieve the linked page, and the server responds with a 200 OK status code and the HTML for the new page.
How does HTTP work?
It works by following a set of rules for formatting messages that are sent between the client (e.g. a web browser) and the server that hosts the requested web page. Here’s how:
- A client sends an HTTP request to the web server. When a user enters a website address (URL) and presses “enter” on their device, the client sends an HTTP request to the web server. The request contains specific details about the requested resource, such as the type of request (e.g., GET, POST), headers (metadata about the request), and a message body (optional).
- The web server receives the request. The server processes it, and sends back an HTTP response to the client. The response contains information about the requested resource, such as the HTTP version, status code, headers (metadata about the response), and a message body (optional).
- The client receives the response. It now renders the content in the browser window.
For instance, say you’re planning a movie night with friends and you’re interested in checking out some reviews for the latest releases. While connected to the internet, you might type in “http://imdb.com” into your browser’s address bar, and the browser will do the rest, connecting to the server and returning the web page to you.

What is HTTP request and response?
An HTTP request is a message generated by the client (usually your browser) that is sent to the server. For instance, if you search for a “reliable CDN at an affordable price” on Google, you might click on one of the websites in the search results. Once you click on that link, your browser generates an HTTP request for you to visit the site and get that information.
Here are the following components in the HTTP request:
- HTTP method. This is the type of request that a browser (client) sends to the server to initiate an action. The most commonly used HTTP methods are GET, POST, PUT, DELETE and PATCH. Each method has a specific purpose and can perform different types of operations on the server. For example, when you open a website about CDNs, you send a GET request. It’s called “get” because such a request helps to get the content of the website.
- URL. This stands for “uniform resource locator” and it refers to the address of the page you are trying to access. For example, you may visit the https://gcore.com address because we provide a CDN.
- Resource path. The part of a URL that identifies a specific resource on a server. This portion of the URL comes after the domain name and any subdirectories. For example, in the URL “https://gcore.com/cdn/gaming,” the resource path is “/cdn/gaming.” The server uses the resource path to locate and retrieve the requested resource, such as a web page, an image, or any other data type.
- HTTP protocol version. This is a number indicating the version of the HTTP protocol being used for a particular request or response. The HTTP protocol has gone through several versions, including HTTP/0.9, HTTP/1.0, HTTP/1.1, HTTP/2 and HTTP/3. Each version has its own features and improvements over the previous versions.
- Request headers. These are a list of additional details included in an HTTP request to provide more context and information about the request being made. For example, it can include the type of browser being used, the language preferences of the user, and the type of content being requested.
- HTTP body. This is the optional data that your browser sends as part of the HTTP request. The HTTP body might contain HTML, JSON, XML, or any other type of content that the client wants to send.

In this example, the client uses the GET method with index.html as the resource path for the URL www.example.com with HTTP/1.1 protocol version. This also includes request headers that provide more information such as the type of browser (Mozilla/5.0) and what language and type of content.
Now that you’re familiar with HTTP requests, let’s discuss what HTTP response is.
An HTTP response is the message that a server sends to a client after receiving an HTTP request. It contains the data that the client requested, such as a web page or a file, along with additional information such as the status of the request and any headers. The response is typically sent using the HTTP protocol and can be customized based on the specific request from the client.
HTTP responses generally consist of the following information:
- HTTP protocol version. Same with HTTP request, it indicates what protocol version was being used for a certain request or response. The standard versions are HTTP/1.1, HTTP/2 and HTTP/3.
- HTTP status code. The HTTP status code is a three-digit code that a server sends back to the client in response to its request. This code indicates the success, failure, or other status of the request. For example, the “200 OK” status means that the request succeeded.
- Status message. A server generates an HTTP response and sends it to a client with the purpose of fulfilling the client’s request for a resource, notifying the client that the requested action has been completed, or indicating that an error occurred during the processing of the request.
- Response headers. An HTTP response header is a section of a network packet that a web server transmits to a web browser or client device in response to an HTTP request. Its purpose is to provide additional information about the server’s response and the requested resource. The header also facilitates the transfer of web content and other web-based data from the server to the browser of the end-user who requested it during web communications.

In this example, the response headers indicate that the server responded with an HTTP 200 OK status code on November 15, 2022 at 9:12:31 GMT. It says here that the server is running Apache version 2.4.6 (CentOS). Then, based on the response, the content type is text/html, telling us that the response body (which is the content) contains an HTML code. From here, it tells us that the content length is 1274 bytes, indicating the overall size of the content.
Why is HTTP not secure?
HTTP does not encrypt data during client-to-server communication, which means that any data transmitted over HTTP is sent in plain text without any encryption or security mechanisms. As a result, it can be intercepted and read by anyone with access to the network traffic, including cybercriminals. Additionally, HTTP does not provide any authentication, making it vulnerable to man-in-the-middle attacks. Attackers can eavesdrop on communication between a server and a client, resulting in the theft of personal information such as login credentials and credit card numbers.
For instance, say you set up an e-commerce website that sells shoes and you take online payments. If your website uses HTTP, chances are high that users’ credentials and other account details can be easily intercepted and stolen by cybercriminals.
Therefore, using HTTP on a website or application can indeed lead to various security risks and potential losses, including data theft, legal liabilities and negative impact on business revenue. Here are just a few examples of the consequences possible when relying on HTTP:
| Consequences of Using HTTP | Potential Losses |
|---|---|
| Loss of customer trust | Customers may lose trust in the business due to the lack of security on the website. This will lead them to take their business elsewhere. |
| Data breaches | Using HTTP can put sensitive customer information at risk of being stolen by hackers. This can result in legal issues, fines, and a damaged reputation. |
| SEO disadvantages | Websites using HTTP are likely to rank lower in search results compared to HTTPS websites. This can result in decreased website traffic and revenue. |
| Liability issues | If a data breach occurs on a website using HTTP, the business owner may be held liable for damages, fines, and legal fees. |
| Lost revenue | Data breaches and loss of customer trust directly translate to lost revenue for the business. |
How do I know if a website is secure?
There are two easy steps to check if your site is secure.
- Check the URL of the website in the address bar. If the beginning of the URL says “http” and not “https”—for example, “http://example.com”—it means that your connection to the site is not secure. This lack of encryption can potentially compromise the security of user data.

- Check the security status symbol. On the web address bar, there are symbols that tell us the security of the connection. As an example, with Google Chrome, a padlock icon typically indicates a secure connection, while a not secure icon indicates an unsafe connection. The Info icon may appear in different contexts, such as when displaying additional information about the website or if it’s not secure.
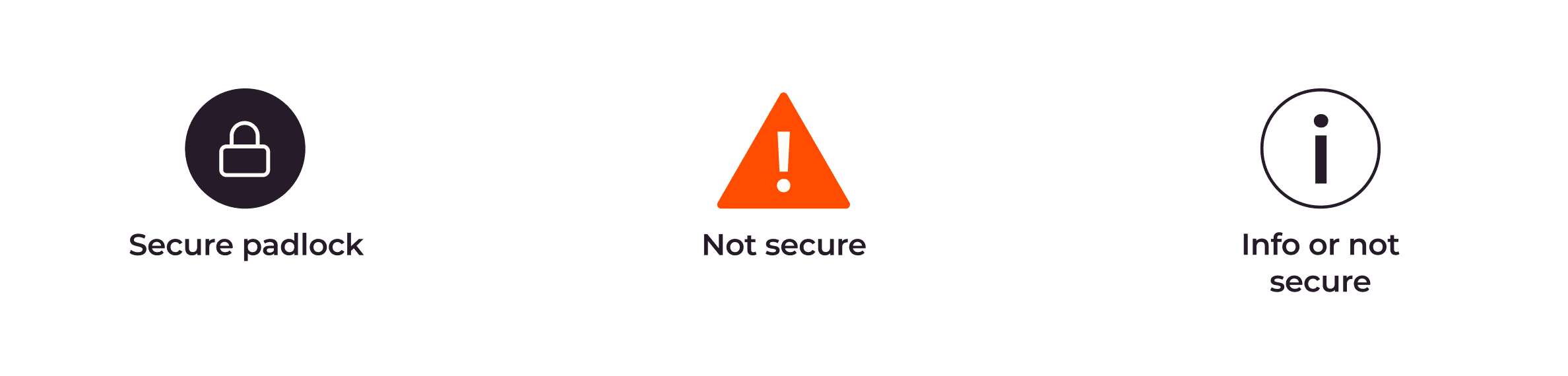
Once you become aware of the security symbols in web browsers, it’s easier to distinguish whether a website is secure. If you own a website and it’s still using HTTP, it’s highly recommended to switch to HTTPS to improve security for potential customers.
What is HTTPS?
HTTPS, short for Hypertext Transfer Protocol Secure, is a more secure version of HTTP. Unlike HTTP, HTTPS encrypts the communication between a web browser and a website, making it more difficult for hackers to eavesdrop, tamper with, or forge data.
This enhanced security makes HTTPS the preferred protocol for online transactions, including online banking and e-commerce, where sensitive information like credit card numbers, passwords, and personal details are transmitted over the internet.
By encrypting data and verifying website identity, HTTPS provides a safe way for users to share and receive information online without worrying about the security of their data.
How does HTTPS work?
HTTPS secures communication between the client and server using asymmetric encryption, a significant improvement over HTTP’s plain text. The encryption protocol used in HTTPS is called Transport Layer Security (TLS). In other words, when a website uses HTTPS, it signifies that the TLS standard is being used to encrypt the data being transmitted between parties. In order to do this, a valid SSL certificate should be installed on the server. From that point, a website can switch from HTTP to HTTPS and activate the lock icon in the address bar.
At its core, TLS provides three key services: encryption, authentication, and data integrity.
- Encryption. TLS uses encryption to protect data transmitted between clients (e.g., a browser or a native app) and servers. With TLS encryption, plaintext data is transformed into an unreadable text (called ciphertext) that only those with the secret key can access or decrypt. This helps to keep the data secure and protected from unauthorized users.
- Authentication. TLS assists in confirming the server and the client identity verification. This is crucial, since it makes sure that the client is speaking with the correct server and not an imposter who might try to steal information.
- Data integrity. TLS aids in preventing data modification or tampering while it is being transmitted. This proves that the information sent by servers and received by clients is accurate and hasn’t been changed in any way.
What are the benefits of using HTTPS?
As you continue reading and learn more about how HTTPS works, you may be curious about the benefits of using it as either a website owner or a regular user. Is it really worth it to switch from HTTP to HTTPS? And what advantages does HTTPS bring to the table? Here are the benefits:
- Data encryption and integrity. HTTPS uses encryption to protect sensitive data that users send and receive on a website, such as login credentials or credit card information. It also ensures data integrity where the data being transmitted between the user’s browser and the web server has not been tampered with or altered during transmission. This can help prevent hackers from intercepting or stealing this data.
- Authentication. HTTPS verifies that the website that a user is visiting is the authentic website and not an impostor. This can help prevent phishing attacks and build trust with visitors.
- Improved SEO. Google uses HTTPS as a ranking signal, so websites that use HTTPS may rank higher in search results than those that don’t.
- Regulatory compliance. Many industries have regulatory requirements for data security and privacy, and using HTTPS can help meet these requirements.
- Boost brand reputation. Alert signs for non-HTTPS websites are displayed by popular web browsers like Chrome and Firefox, which may discourage visitors and damage a website’s credibility. These warnings can be avoided by using HTTPS.
HTTP vs. HTTPS—What’s the difference?
Both HTTP and HTTPS are protocols used for transferring data between web browsers and web servers. However, the main difference between the two is the level of security they offer. HTTPS uses SSL/TLS protocols to authenticate both the web browser and the web server, ensuring that data transmitted between them is encrypted and secure. In contrast, HTTP doesn’t use any encryption protocol, leaving data vulnerable to interception and unauthorized access.
Now that you have learned about the benefits of HTTPS and the potential drawbacks of using HTTP, let’s compare the two in real-life situations to understand how they can differ in impacting your business.
| Feature | HTTP | HTTPS | Real-life example |
|---|---|---|---|
| Data Security | Not secure, as data is transmitted in plain text | Secure, as data is encrypted between the web browser and the web server | Without HTTPS, sensitive data such as customer login credentials and payment details are vulnerable to interception and theft by hackers. For example, a business that processes credit card transactions on their website would need to use HTTPS to ensure their customers’ financial information is kept safe. |
| Search Engine Optimization (SEO) | Not a ranking factor for SEO | A ranking factor for SEO, as Google prefers secure websites | HTTPS can give a business an SEO advantage over non-HTTPS websites. For example, an e-commerce site that uses HTTPS may rank higher in Google search results for certain keywords compared to a competitor site that doesn’t use HTTPS. |
| Brand Reputation | Lack of HTTPS can harm a business’ reputation and deter potential customers | HTTPS can improve a business’ reputation and instill trust in customers | Without HTTPS, customers may perceive a business as untrustworthy and be less likely to make purchases or share personal information on the site. For example, a medical practice that uses HTTPS to protect patient data can gain a reputation for taking security seriously and earn the trust of its patients. |
| Legal Compliance | Lack of HTTPS could lead to legal issues and fines | HTTPS is increasingly becoming a legal requirement for businesses that process sensitive data | In some industries, such as healthcare and finance, businesses are required by law to protect sensitive data using HTTPS. For example, a financial institution that doesn’t use HTTPS could face legal repercussions for failing to meet data protection standards. |
How to convert from HTTP to HTTPS
Now that you understand the advantages of using HTTPS, you may be wondering how to make the switch from HTTP to HTTPS. To enable HTTPS on your website, you typically need to obtain an SSL/TLS certificate and configure your web server to use it.
- Obtain an SSL/TLS certificate. This can be done by purchasing a SSL certificate from a trusted Certificate Authority (CA) or by using a free one like Let’s Encrypt. To obtain an SSL certificate, you will need to provide certain information such as your domain name, organization name (if applicable), and contact details. This information will be used to generate a Certificate Signing Request (CSR), which you will then pass on to the Certificate Authority (CA) to obtain the SSL certificate. Please note that specific information may vary depending on the type of SSL certificate you’re using.
- Install the certificate on your web server. The installation process will vary depending on your web server software. Generally, you’ll need to configure your web server to use the certificate and private key you obtained in the previous step. This makes your website available over HTTPS and ensures that the encryption key is in place.
- Update your website links. Once the certificate is installed, you’ll need to update your website links to use HTTPS instead of HTTP. This includes updating all internal links, as well as any external links you may have on your site. This step ensures that all content on your website is available over HTTPS and that there are no content warnings.
- Test your site. After you’ve enabled HTTPS on your site, it’s important to test it to ensure that everything is working properly. You can use various online tools to check for SSL/TLS certificate errors and mixed content warnings. This step further ensures that your website is available over HTTPS and that there are no errors or warnings that could impact user experience or search engine ranking.
How does Gcore help website owners to enable HTTPS encryption?
At Gcore, we are dedicated to helping our clients to make the switch from HTTP to HTTPS.
With any of our CDN plans, you can issue a free Let’s Encrypt SSL certificate for all domains associated with your Gcore account. Also, you can install a custom SSL certificate from another provider. When the certificate is installed, you can switch from HTTP to HTTPS in a few clicks.
Furthermore, we offer various paid SSL certificates to cater to different industries and sectors. Let’s delve into each of the SSL certificate types we provide:
| Certificate Type | Description | Best for |
|---|---|---|
| DV certificate with domain validation | This certificate is useful for protecting basic web pages such as personal websites and blogs. A Domain Validated (DV) certificate is a type of SSL certificate that provides basic encryption and is issued within minutes. It is typically the most affordable type of SSL certificate and offers the lowest level of validation. An example of a DV certificate is the Let’s Encrypt SSL certificate. | Blogs, informational websites |
| OV certificate with organization validation | This certificate is required for e-commerce and online sales. An OV certificate identifies the website owner and contains a company name. Fraudsters will not be able to pass the validation check and get this certificate. Once this certificate is obtained, a company name is displayed in the browser bar. Such websites are more trustworthy for visitors. | Online stores, websites that require its users to log in |
| IDN certificate | This certificate supports domains in native language characters. If your website domain name does not contain ASCII characters, you’ll need to get an IDN certificate. | Domain and subdomain. Domain names that use non-English languages |
| Wildcard certificate | This certificate covers both the domain and its subdomains. Subdomains must have the same second-level domain name (i.e., domain.com). | Mail server, online banking services, social media platform |
To review the price of each certificate, check out our pricing comparison.
Conclusion
In summary, HTTP is a protocol that is vulnerable to attacks, while HTTPS is a secure version of HTTP that uses encryption to protect data in transit.
Fortunately, switching to HTTPS is a relatively simple process, and Gcore CDN service allows users to enable HTTPS encryption for free using Let’s Encrypt certificate. However, using a free SSL certificate has its limitations. Gcore has this covered as well, offering SSL certificates with various validation levels, including DV, OV, IDN, and Wildcard, giving website owners several options to choose from based on their specific requirements. Finally, seeking guidance from experts can help website owners ensure their websites are adequately secured and protected from potential threats.
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.