Your web application just processed what looked like a normal login request, but it was actually an SQL injection attack that exposed your entire customer database. Cross-site scripting (XSS), SQL injection, and other application-layer attacks rank among the most dangerous OWASP Top 10 vulnerabilities, targeting the exact entry points where your customers interact with your business, targeting the exact entry points where your customers interact with your business.
Traditional firewalls can't stop these threats. They're designed to filter traffic based on IP addresses and ports, completely blind to the malicious payloads hidden inside legitimate-looking HTTP requests. If you're running an e-commerce site, banking platform, healthcare portal, or any application handling sensitive data like credit card numbers or personal information, you're exposed at Layer 7, the application layer where these attacks operate.
You'll discover how specialized security solutions protect against these application-specific threats, the three deployment models you can choose from, and why organizations handling customer data increasingly rely on application-aware protection that goes far beyond what traditional network security can offer.
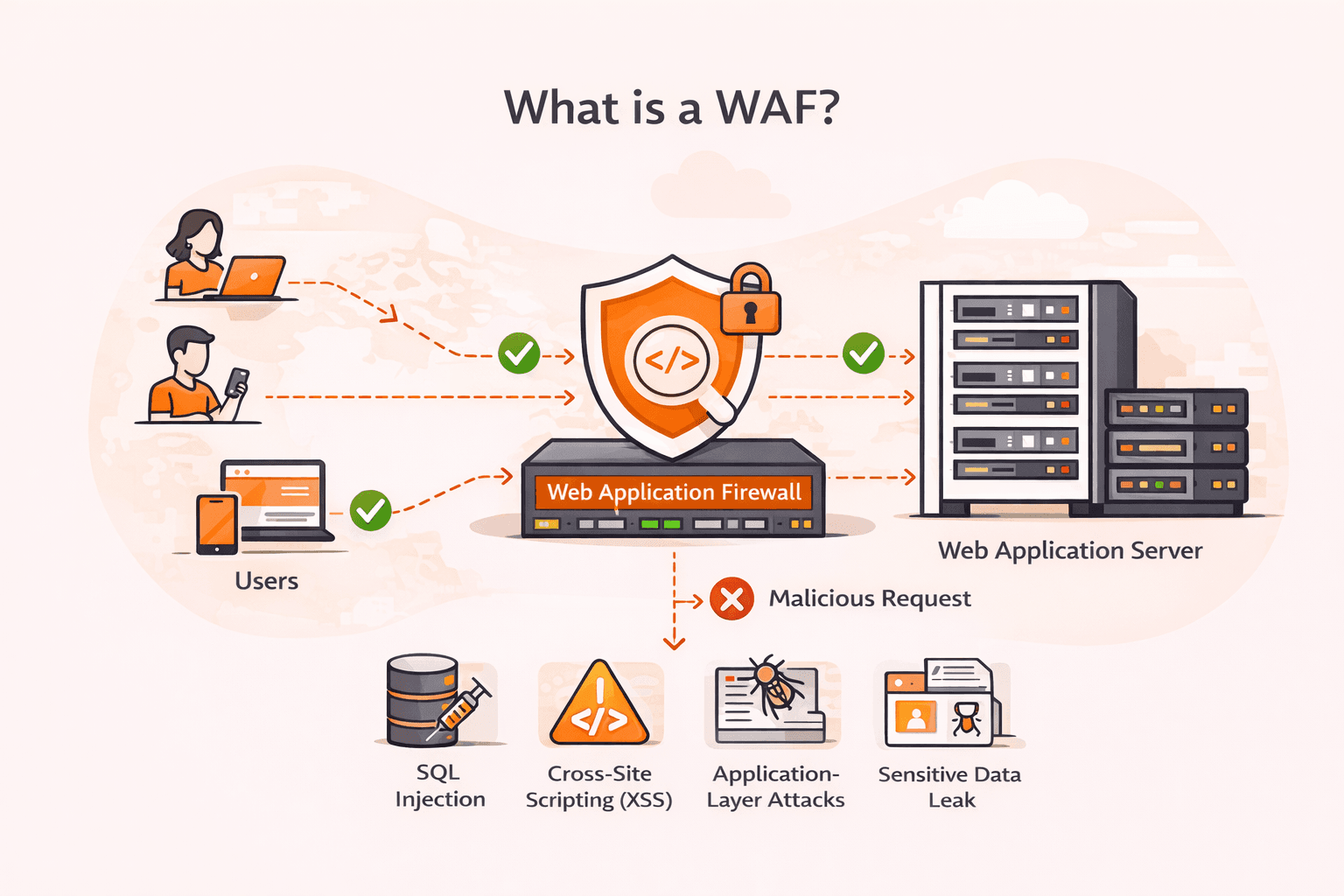
What is a WAF?
Think of a WAF (Web Application Firewall) as a security checkpoint that sits between your web application and incoming traffic, filtering out malicious requests before they reach your servers. It works at the application layer (Layer 7 of the OSI model), where it can inspect the actual content of HTTP and HTTPS requests, not just IP addresses and port numbers like traditional firewalls do. This means a WAF can detect and block attacks like SQL injection, cross-site scripting (XSS), and other threats that target vulnerabilities in your application code itself. The firewall acts as a reverse proxy, analyzing everything from URL parameters and cookies to request headers and payloads, stopping harmful traffic while letting legitimate users through.
How does a WAF work?
A WAF positions itself between users and your web application server, inspecting every HTTP and HTTPS request before it reaches your application. When a request arrives, the WAF examines the entire HTTP conversation (URL parameters, headers, cookies, and the actual payload), looking for patterns that match known attack signatures or violate your security rules.
Here's what happens during inspection: The WAF compares incoming traffic against its rule sets, which define both malicious patterns to block (like SQL injection attempts) and legitimate traffic to allow. If a request contains suspicious elements (say, SQL commands in a form field or JavaScript code in a URL parameter), the WAF blocks it immediately and logs the attempt. Clean requests pass through to your application server without delay.
The inspection happens in real time, typically adding only milliseconds of latency. Modern WAFs use three detection methods: signature-based rules that catch known attacks, behavioral analysis that spots unusual patterns, and machine learning models that identify novel threats. You can customize these rules to match your application's specific needs, adjusting sensitivity levels and creating exceptions for legitimate traffic that might otherwise trigger false positives.
The WAF also monitors outbound responses from your server, verifying that data leaving your application matches expected content types and doesn't contain sensitive information that shouldn't be exposed.
What are the main benefits of using a WAF?
WAF benefits go beyond basic security to include performance improvements, compliance support, and operational flexibility. Here are the main advantages.
- Application-layer protection: WAFs defend against attacks that target your web applications directly, like SQL injection and cross-site scripting (XSS). Traditional firewalls can't catch these threats because they only check IP addresses and ports, not the actual content of requests.
- Compliance support: WAFs help you meet regulatory requirements like PCI DSS by blocking traffic that violates security standards. This is particularly important for retail, banking, and healthcare organizations that handle sensitive customer data like credit card numbers and personally identifiable information.
- Rapid threat response: You can modify WAF policies quickly to counter active attacks. During a DDoS attack, for example, you can deploy rate limiting within minutes to protect your application from being overwhelmed.
- Encrypted traffic inspection: Advanced WAFs decrypt SSL/TLS traffic to inspect encrypted requests for malicious payloads. Without this capability, attackers can hide threats inside encrypted connections that bypass other security tools.
- Custom rule flexibility: WAFs let you create application-specific rules that match your unique security needs. You can update these rules automatically based on global threat intelligence, so your protection evolves as new attack methods emerge.
- Basic bot filtering: WAFs can block known malicious bots using IP reputation lists and apply rate limiting to prevent automated abuse. For advanced threats like sophisticated scrapers and credential stuffing, dedicated bot management solutions or WAAP platforms offer additional behavioral analysis and device fingerprinting capabilities.
- Reduced security overhead: Cloud-based WAFs eliminate the need to manage security hardware on-premises. This deployment model reduces maintenance costs while providing protection that scales with your traffic.
- Integration with security tools: WAFs connect with SIEM and SOAR platforms to automate incident response and centralize security logging. This integration gives your security team better visibility into threats and faster response times.
What are the different types of WAF solutions?
WAF solutions come in three main deployment models, each designed for different infrastructure needs and security requirements. Organizations choose between network-based, host-based, and cloud-based options depending on factors like control requirements, resource availability, and scalability needs.
- Network-based WAF: This hardware appliance sits directly in your data center, positioned between your firewall and web servers. It offers the lowest latency since traffic doesn't leave your network, giving you complete control over security policies and data. The tradeoff is higher upfront costs for hardware and the need for dedicated IT staff to manage and maintain the equipment.
- Host-based WAF: You install this software directly on each application server that needs protection. It's more affordable than network appliances and offers deep integration with your application code, allowing for customized protection rules. The downside is increased server resource consumption and the complexity of managing separate WAF instances across multiple servers.
- Cloud-based WAF: A third-party provider manages this solution entirely, requiring minimal setup (often just a DNS change to route traffic through their infrastructure). You get automatic updates, built-in scalability to handle traffic spikes, and no hardware to maintain. It's the most cost-effective option for organizations without dedicated security teams, though you'll have less granular control compared to on-premises solutions.
- Hybrid WAF: Some organizations combine deployment models to balance control and convenience. For example, you might deploy a network-based WAF for internal applications while protecting public-facing services with a cloud solution. This approach lets you optimize costs while maintaining strict control where it matters most.
- Next-generation firewall integration: Modern NGFWs bundle WAF capabilities with traditional network security, antivirus, and threat intelligence into one platform. These integrated solutions reduce the number of security tools you need to manage, though they may not offer the same depth of application-layer protection as dedicated WAF products.
How does a WAF differ from other security tools?
A WAF differs from other security tools by focusing specifically on application-layer threats in web traffic, while traditional firewalls and intrusion prevention systems operate at the network layer. Here's how they compare.
Traditional firewalls work at Layer 3 and Layer 4 of the OSI model. They filter traffic based on IP addresses, ports, and protocols but can't inspect the actual content of HTTP requests. If you're running a web application, a network firewall won't catch SQL injection attacks hidden in URL parameters or malicious JavaScript in form submissions.
Intrusion prevention systems (IPS) sit between network firewalls and WAFs in capability. They can detect some application-layer attacks through signature matching, but they don't understand web application context the way WAFs do. An IPS might miss an attack that exploits legitimate HTTP methods or manipulates session cookies.
WAFs analyze the full HTTP/HTTPS request (headers, cookies, payloads, and URL parameters). They understand web application logic and can detect threats like cross-site scripting and cross-site request forgery that other tools miss. When you decrypt SSL/TLS traffic, a WAF inspects encrypted requests that would pass through traditional security layers unexamined.
API gateways traditionally focus on API management features like authentication, rate limiting, and routing. However, they typically require integration with a dedicated WAF or a combined WAF/API gateway platform—to provide comprehensive protection against OWASP Top 10 vulnerabilities. Some modern solutions bundle these capabilities together, while others require separate WAF deployment for full application-layer security.
What are the key WAF use cases?
WAF use cases cover the security scenarios where organizations deploy web application firewalls to protect their applications and data. Here are the primary use cases.
- E-commerce protection: Online retailers need WAFs to safeguard customer payment data and personal information during transactions. A WAF blocks SQL injection attempts that could expose credit card numbers and prevents form manipulation attacks that might alter pricing or inventory data.
- API security: Modern applications rely on APIs to exchange data between services, making them attractive targets for attackers. WAFs inspect API traffic for malicious payloads, enforce rate limits to prevent abuse, and validate that requests follow expected patterns.
- PCI DSS compliance: Organizations that process credit card payments must meet Payment Card Industry Data Security Standard requirements. WAFs help satisfy these compliance mandates by filtering traffic that violates security policies and providing detailed logs of all web application access attempts
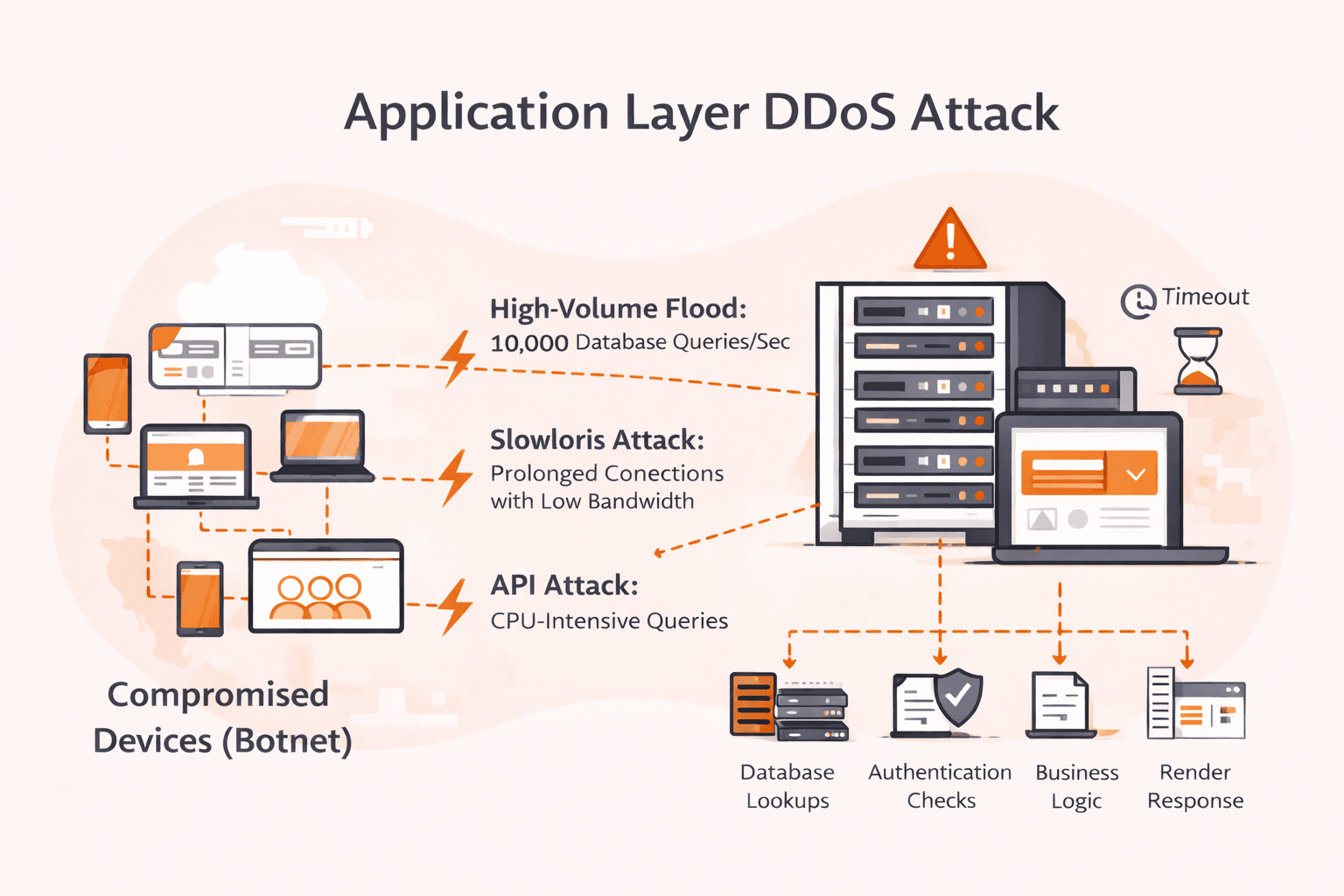
- Application-layer DDoS mitigation: WAFs help defend against Layer 7 DDoS attacks like HTTP floods and slow-request attacks through rate limiting and traffic filtering. For volumetric network-layer attacks, additional DDoS protection services are required.
- Protection for legacy applications: Older web applications often contain security vulnerabilities that can't be easily patched without major code rewrites. A WAF acts as a virtual patch by blocking exploitation attempts before they reach vulnerable code.
- Mobile app backend security: Mobile applications communicate with backend APIs that need protection from malicious requests. WAFs analyze traffic from mobile clients to detect bot activity, credential stuffing attacks, and attempts to reverse-engineer API endpoints.
- Healthcare data protection: Medical applications handle sensitive patient information that's subject to HIPAA regulations and frequent attack attempts. WAFs prevent unauthorized access to electronic health records and block attacks that could compromise patient privacy.
- Bot filtering: Automated bots scrape content, create fake accounts, and attempt credential stuffing at scale. WAFs provide foundational protection through IP reputation and rate limiting, while dedicated bot management solutions add behavioral analysis and ML-based detection to identify sophisticated bots that mimic human behavior.
How to choose the right WAF for your business?
When you're evaluating WAF solutions, focus on how well they match your application architecture and threat profile. Here are the key factors to consider:
- Deployment model flexibility. Choose between network-based, host-based, or cloud-based options depending on where your applications live. Cloud-based WAFs offer the fastest deployment and automatic scaling, while network-based solutions give you more control over on-premises infrastructure.
- Rule customization and management. Look for solutions that let you create custom rules for your specific applications while also providing automatic updates for emerging threats. The best WAFs balance pre-configured protection against common attacks like SQL injection and XSS with the flexibility to address your unique security requirements.
- Performance and latency impact. Test how the WAF affects your application's response times, especially if you're running high-traffic sites. SSL/TLS decryption for inspecting encrypted traffic adds processing overhead, so verify the solution can handle your peak traffic loads without degrading user experience.
- Advanced threat detection capabilities. Beyond signature-based blocking, consider whether you need machine learning for detecting novel attacks, bot protection to prevent scraping and abuse, and rate limiting to defend against DDoS attempts. These features become essential as attack methods grow more sophisticated.
- Integration and visibility. Check compatibility with your existing security stack, including SIEM and SOAR platforms for centralized logging and incident response. You'll want detailed analytics on blocked threats and false positives to fine-tune your rules over time.
- Compliance support. If you handle payment data or operate in regulated industries, confirm the WAF helps meet standards like PCI DSS. Some solutions include pre-built rule sets designed specifically for compliance requirements.
- Total cost of ownership. Factor in licensing models, bandwidth costs for cloud-based solutions, and the staff time required for ongoing rule management and tuning. A solution that's cheap upfront but requires constant manual adjustments can end up costing more than a higher-priced option with better automation.
How can Gcore help with WAF deployment?
Gcore secures your web applications through a cloud-based WAF that filters malicious traffic across 210+ global PoPs before attacks reach your origin servers. This solution protects against SQL injection, XSS, and other OWASP Top 10 threats while you customize rule sets to match your application's specific security requirements.
You'll get real-time threat intelligence updates and DDoS mitigation built into the same platform, so there's no need to stitch together multiple security vendors. The Gcore WAF also includes bot protection and rate limiting to stop credential stuffing and API abuse without impacting legitimate user traffic.
Learn more about Gcore Web Application Security at gcore.com/cloud/web-security.
Frequently asked questions
What's the difference between a WAF and a CDN?
A WAF protects web applications from attacks like SQL injection and XSS, while a CDN delivers content faster by caching it closer to users. Many CDN providers bundle WAF features into their platforms, so you'll often deploy both together for security and performance.
How much does a WAF solution cost?
WAF costs vary widely from $20 per month for basic cloud-based solutions to over $200,000 annually for enterprise hardware appliances, depending on deployment model, traffic volume, and feature requirements. Cloud-based WAFs typically charge based on requests processed or bandwidth consumed, while network-based and host-based solutions involve upfront hardware or software licensing costs plus ongoing maintenance.
Is a cloud-based WAF secure enough for enterprise deployment?
Yes, cloud-based WAFs provide enterprise-grade security with advantages like automatic updates, global threat intelligence, and elastic scalability that often surpass on-premises solutions. Leading cloud WAF providers offer 99.9%+ uptime SLAs, SSL/TLS decryption, and integration with SIEM platforms for complete threat monitoring.
What are the performance requirements for WAF deployment?
WAF performance requirements depend on your traffic volume, latency tolerance, and deployment model. Network-based WAFs need one to 10 Gbps throughput capacity, while cloud-based solutions scale automatically. You'll want to ensure your WAF adds less than 10 ms of latency and can handle your peak requests per second without becoming a bottleneck.
How does machine learning improve WAF effectiveness?
Machine learning improves WAF effectiveness by detecting novel and evasive attack patterns that signature-based rules can't identify, adapting to emerging threats without manual rule updates. This lets WAFs analyze traffic behavior patterns and automatically flag suspicious anomalies that traditional static rules would miss.
Do small businesses need a WAF?
Yes, small businesses need a WAF if they handle customer data online, accept payments, or face compliance requirements like PCI DSS. Cloud-based WAFs offer affordable, scalable protection without requiring dedicated security infrastructure or expertise.
What compliance standards do WAFs help meet?
WAFs help organizations meet PCI DSS requirements by blocking malicious traffic that violates payment card industry standards, particularly for applications handling credit card transactions. They also support compliance with HIPAA, GDPR, and SOX by protecting sensitive data through application-layer security controls and detailed logging capabilities.
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.