In this article, we’ll deep into what cloud servers are, how they work, their types, benefits, and challenges. We’ll also cover factors to consider when choosing a cloud provider.
What Is a Cloud Server?
A cloud server is a pool of powerful virtual or dedicated physical computer resources. These resources are hosted in the public or private cloud infrastructure and can be accessed through the internet or a virtual private network (VPN.)
Despite their off-site locations, the servers in the cloud provide broadly the same functionality as the traditional on-premises physical servers. However, the cloud environment offers scalability, flexibility, and has a lower cost of entry, since it does not require upfront investments in physical infrastructure like an on-premises data center.
A typical cloud server combines high-performance components and systems in one or more locations via high-speed networks. These may be physically located in one or more machines or distributed across several networks. For example, a physical server cluster may provide the CPU and memory (RAM) while the storage is in another location or system, such as network-attached storage (NAS.)

While shared cloud server hosting is adequate for many organizations, it may not suit high-traffic applications or those dealing with sensitive data. So, those projects that require more resources or to be isolated from noisy neighbors find private cloud to be a better fit. Healthcare, banks, and other resource-intensive industries, such as gaming websites, video streaming, and research organizations, prefer private cloud servers where resources are physically isolated from all other users.
Types of Cloud Servers
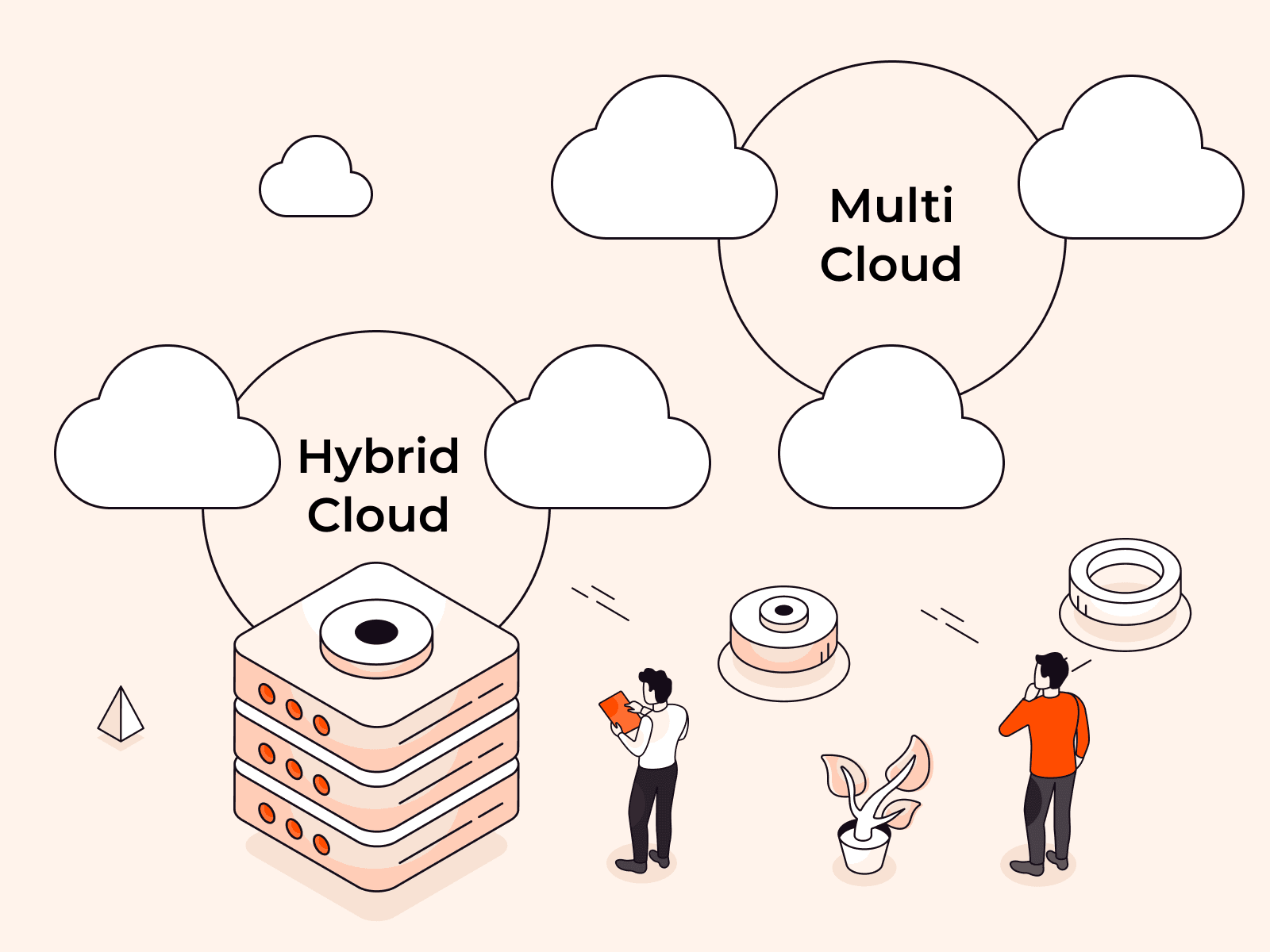
Cloud servers can be categorized into three types, based on where they reside: public, private, and hybrid.
Public Cloud Server
Public cloud servers are computer resources hosted on a public cloud infrastructure, which means they are owned, managed, and maintained by a third-party service provider. The provider makes all resources available to the public via the internet. For example, Gcore offers bare metal servers, virtual dedicated servers, and managed Kubernetes containers.
Private Cloud Server
A private or dedicated cloud server is a cloud architecture where resources are only available to a single organization. The cloud provider installs the dedicated cloud server, such as Gcore’s Bare Metal, in a private region. Private servers provide better performance, control, and security, making them suitable for highly regulated industries, high-traffic websites, or running mission-critical or sensitive applications.
In-House Versus Third-Party Private Cloud Servers
Organizations can host private cloud servers either in-house or in a third-party cloud environment. In the latter case, the provider owns and manages the hardware and software resources, including the supporting infrastructure. The choice depends on objectives regarding control, convenience, cost, and flexibility. Third-party cloud hosting offers less control, but deploying and scaling are faster, simpler, and more cost-effective.
When the private cloud operates from the in-house data center, users access it over the local area network (LAN.) External users or remote offices can access the server over a private network such as a VPN or the organization’s intranet.

Hybrid Cloud Server
Hybrid cloud servers are a mix of public cloud and on-premises or private infrastructure. Hybrid cloud offers the best performance, flexibility, availability, and scalability. A hybrid cloud server enables businesses to take advantage of the best of these two environments to achieve optimal outcomes regarding compliance, availability, and security. A typical configuration could involve an off-site public cloud server combined with an in-house or third-party-hosted private cloud server. An example of a hybrid cloud server is our Virtual Private Cloud Services.
Read: What is a bare metal server?
How Does a Cloud Server Work?
Public and private cloud servers work like traditional on-premises physical servers. They provide processing power, run applications, store data, and perform other functions like running databases, mail servers, etc. However, unlike the in-house servers that run locally from the in-house data center, most cloud servers are hosted and managed by third-party cloud computing providers. They are only accessible over the internet or a virtual private network (VPN.)
Most public cloud servers are software-defined using a virtualization process that creates multiple virtual machines on a single physical server. Providers may use a hypervisor or other virtualization technology to abstract the CPU, memory, storage, and other server resources.
For shared public cloud servers, the virtualization technology pools the configured resources to create multiple cloud servers that function like physical machines, but are only accessible via the Internet. This allows customers to share the hosting server’s compute, memory, storage, and other resources. However, each can access a separate instance with the individual operating system. Clients on the same physical server can run different applications and store data independently.
Cloud computing service providers usually invest in, manage, and maintain a high-capacity infrastructure, benefiting from the economies of scale. Consequently, they can pass on these benefits to customers and offer reliable, high-performance servers at lower costs than clients would have spent deploying equivalent systems in their data centers.
Most cloud computing providers have self-service portals that potential customers use to create and deploy cloud servers in less than ten minutes. Automated systems enable the customers to choose predefined servers or configure custom CPU, storage, memory, and other resources that align with their specific requirements and budget.
Who Should Use Cloud Servers, and Why?
The cloud computing delivery model is suitable for all types and sizes of workloads. Since it allows deployment of powerful virtual machines and bare metal servers without the high upfront costs associated with an on-premises system. The flexibility and affordability of cloud’s pay-as-you-go pricing plans enable everyone, including those with limited budgets—to deploy cloud servers that meet their specific needs.
By contrast, setting up an equivalent in-house system would mean installing physical servers and adequate storage in the organization’s data center. This capital-intensive exercise would require significant time and skill to install, configure, and manage, making it impractical and unaffordable for those with inadequate resources.
To understand the problem users of on-premises servers face is to imagine an organization with seasonal traffic spikes—a good example is an e-commerce platform with traffic spikes during the sales season, such as Black Friday.
The company may invest in large local infrastructures with enough capacity to handle traffic spikes, but those expensive resources remain idle most of the time. A cloud server can reduce deployment costs, time, and overprovisioning of resources while improving efficiencies and revenues.
In this article, we’ll discover what a cloud server is, the different types of cloud servers, how a cloud server works, its many benefits and limited challenges, and why cloud is essential for most individuals and organizations.
What are the benefits of cloud servers?
The specific benefits of a cloud server vary depending on the organization’s objectives, workload, and type of server and plan. However, numerous common advantages to individuals and businesses are worth a closer look.
Low Deployment and Maintenance Costs
Customers can rent virtual cloud servers and storage at a much lower deployment and maintenance cost. This results in savings in CapEx, space, and running costs, such as highly skilled in-house staff, electricity, cooling, and other requirements for maintaining an on-premises system.
Highly Scalable and Flexible Computing Resources
Servers in the cloud are highly scalable, with an almost unlimited capacity to process resource-intensive workloads and store vast quantities of data. Most providers offer flexible plans, enabling users to choose the appropriate configuration and operating system based on workloads. Customers can quickly and easily create or remove the servers or resources depending on current needs, demand, and budget.
Cloud computing providers often invest in vast capacities so that customers can add resources to meet temporary high-demand workloads and then remove them when demand is low. When a configured cloud server capacity cannot handle a particular workload, the customer organization can scale by quickly adding resources. Cloud servers scale up or down to match the current workload quickly and easily.
Easy to Deploy and Use
Provisioning a cloud server is almost instant. It usually takes less than ten minutes to configure and start using a virtual instance. Installation, physical upgrades, and maintenance associated with on-premises infrastructure are all taken care of by the cloud computing provider.
Global Access and Universal Workload Capability
Cloud servers provide the same functions as on-premises servers. However, they are accessible by more users regardless of their location. An on-site server is only accessible by the users on the company’s network. However, a server in the cloud is accessible through the internet, hence the ability to serve a broader user base.
Internet connectivity enables cloud servers to handle global workloads. However, unexpected disruptions, instabilities, and network latency can degrade performance for users, especially in locations with less reliable internet connectivity. To overcome this, cloud service providers can create duplicate instances to process workloads on servers in different locations, thus ensuring faster connectivity, continuity, and better user experience.
Affordable Pricing Plans
Cloud service providers offer a wide variety of pricing plans based on the specifications. Customers can opt for annual, monthly, or pay-as-you-go payment plans. There are usually different commitment plans available, commonly for three or six months or one or two years. In general, cloud services are charged at an hourly rate. Customers pay for the resources used at the end of the month.
Besides the annual and monthly rates, Gcore offers per-hour billing on production-grade instances designed for heavy workloads, complex calculations, and other high CPU-intensive applications. Per-hour billing is suitable for customers who do not want to sign up for monthly or annual contracts. Typical rates range from $0.03496/hr for a 2vCPU, with 2GB RAM, to $2.9/hr for a 32vCPU, 128GB RAM, and 4GPU.
The overall cost of an instance depends on the allocated computing resources, operating system, and usage time, which are calculated from the moment use begins until it is completely stopped. Storage and network usage are charged separately.
Flexible Cloud Server Specifications
Cloud servers allow client customization to suit unique business needs and use cases. While the providers offer some cloud servers with standard specifications, they also allow the customization of various resources.
Highly Available and Reliable
Cloud servers are highly available, and most providers guarantee 99% uptime. As such, it is rare to experience frequent and lengthy downtimes. Unlike a traditional on-premises server that may experience downtime and take time to fix, cloud servers have several redundant components and faster recovery features, which make them highly available and reliable.
Top-Notch Security
Cloud computing providers use highly effective security solutions to protect the infrastructure and data, and have skilled IT security teams to ensure the servers’ constant protection. They also observe security best practices, such as updating the software and tools.
Read: What is Latency?
What Are the Challenges of Using Cloud Servers?
Before migrating to the cloud, it is essential to evaluate the challenges you are likely to experience. Issues to consider include performance, security reliability, availability, and more. These may differ from one deployment and cloud server type to the other. However, some common issues include cloud server performance issues, meeting regulations, cloud outages, a lack of direct server control, and incompatibility. Let’s review each one in depth.
Cloud Server Performance Issues
Shared or “logical” cloud servers reside in multi-tenant environments. You don’t have direct control over the VM, its location, or other cloud servers on the same physical machine. As such, excessive usage of resources such as network and storage by other tenants may degrade the performance of your server.
One way of overcoming performance degradation is to migrate your workloads to regions with fewer activities. But the ultimate solution is to move to a server with more capacity. The cost of such a server depends on the type and configuration, with dedicated servers being costlier than virtual servers.
For example Gcore virtual dedicated servers that support Linux and Windows operating systems start at $4.99. The entry-level servers have 1vCPU, 512MB RAM, and 20GB disk, and you can adjust the specifications to match your workload. A dedicated server with an E-2236 Intel Xeon CPU, 32 GB RAM, and 2x 480 SSD disks starts at $206 per month and guarantees outstanding performance without exception, even for highly demanding workloads. A user who needs the full capacity of Gcore’s top-end cloud server could experience performance issues if they tried to put that same workload through an entry-level server, which is why it’s important to pick the option that matches your use case. Gcore’s experts can help with that.
Regulations, Compliance, and Governance
Data privacy rules, regulations, and other industry standards mean that cloud users can come up against challenging differences between geographical locations, which limit options for cloud servers. For example, if regulations or industry standards demand that the organization must store its data within its political and geographic boundaries, this means a limited choice of cloud servers.
Unexpected Cloud Server Outages
Cloud servers may experience unexpected outages due to a problem within the service provider’s infrastructure or as a result of internet issues. Since the servers are hosted at a physical distance, customers have no way to remedy outages and are reliant on the cloud provider for both information and a fix.
Such problems may include network issues or slow performance due to spikes in demand. Additionally, unexpected network issues could be beyond even the provider’s control. To safeguard against such a challenge, organizations may opt to keep the critical workloads in on-premises servers. Choosing a reliable cloud provider, such as Gcore, can help to limit such outages.
Limited Direct Control of the Server
The cloud provider manages the cloud infrastructure, including the type of hardware components and location. This leaves you unable to optimize the systems for the best performance, since you have no direct control of the server.
Incompatibility
If the cloud servers only support some of your operating systems, workloads, and applications, you may experience compatibility issues. Selecting a cloud provider and planning carefully upfront can help mitigate this problem but does not always account for future additional or changed needs.
Factors to Consider When Looking for a Cloud Server
The choice of a cloud server depends on a combination of factors, such as your workload, budget, server technology, and providers’ reputations. Below are the key issues to consider.
Type of Cloud Server to Deploy
Virtual machines are budget friendly and easier to manage. However, performance issues are always a threat, especially when other tenants have a high demand for resources on the same physical machine. As such, they are suitable for less resource-intensive and non-critical workloads. If you want a third-party vendor-controlled virtualized layer, this is the right choice.
If you need more resources and your workload requires an entire system built from the ground up, then you need a bare metal server. Bare metal offers superior resources compared to VM, and other clients’ demands do not affect bare metal. However, bare metal is costlier than VM. You can host the bare metal server on-premises or on a third-party provider’s infrastructure.
Type of Server Virtualization Technology
Providers may use hardware or software virtualization technologies to subdivide a physical server into several virtual machines. In a logical cloud server, virtualization abstracts resources such as the CPU, storage, memory, and network from the physical hardware, so that services and applications can function without depending so much on the hardware.
Besides hypervisor-based virtualization, providers can use other technologies such as OS-level virtualization, hardware virtualization, hardware-assisted virtualization, etc. It’s important to check whether the virtualization technology is suitable for your operating system, applications, and workloads.
Cloud Server Security
Securing your users, workloads, and data on the cloud server should be a priority. This prevents or reduces risks of cyberattacks by implementing effective DDoS mitigation, while also addressing threats like ransomware and other security issues that could compromise your systems, degrade performance, and cause financial or reputational losses.
Unlike an on-premises data center, where you can protect your digital assets using perimeter security and other technologies, you have less control over the cloud-based server. Instead, you have to rely more on the security measures of the cloud service provider.
It is, therefore, vital to evaluate their technologies and ensure the provider can adequately secure your cloud server. However, cloud security is a shared responsibility between the provider and customers. As such, you still need to deploy various security measures, policies, and practices to protect your users, applications, and data.
Cost-Effective Cloud Services
Good value doesn’t always mean picking the cheapest option available. Select a cloud service that delivers the best features at a fair price. Customizing and optimizing the server comes with added costs, but ensures better performance and security of your workloads and data. It’s also worth paying attention to the available pricing plans, their flexibility, and their compensation policy if you decide to move away before the contract ends.
Support for Private Cloud Server
The public cloud servers offer some level of cost-savings and convenience. However, compliance and data governance requirements may require deploying a private cloud server with resources fenced off from other users. In such a case, you need a provider who supports the private or hybrid cloud server system while offering favorable customization options.
Numerous and Diverse Cloud Features
It is vital to look for a provider who offers a service that meets your current and future needs. Choose a provider offering features such as automatic scaling, load balancing, easy server upgrades, backups, and disaster recovery so that you can feel confident in your efficiency, performance, and continuity.
Reliable and Prompt Support
A good provider must offer reliable support to minimize downtimes. Ideally, look for a provider that provides 24/7 support. Check the reviews to see what other customers have experienced when it comes to support from your potential provider.
Compliance with Regulatory Standards
If you are in an industry that requires compliance with regulations such as GDPR, CCPA, ISO/EIC 27 001, HIPAA, PCI-DSS, and others, look for a compliant provider.
Seamless Migration to the Cloud
Whether switching from an on-premises data center or another cloud provider, your new cloud service provider should assist you in the migration process. Such support ensures a smooth transition and minimal interruption or downtime.
Cloud Server Customization Options
If you anticipate that your business will grow rapidly or experience temporary demand spikes, look for a scalable and customizable service where you can add or remove resources to meet current and future needs. Auto-scaling features enable the automatic addition or removal of server resources, ensuring that you can easily and quickly process any workload while only paying for the computing resources that you actually use.
Should You Switch to a Cloud Server?
Most individuals and organizations benefit from switching to the cloud because it offers cost-effective, scalable, and reliable on-demand computing services without an upfront cost.
However, public cloud is not always the best choice, especially for use cases involving unusually sensitive data (such as healthcare or finance companies) or extreme performance computing requirements. For sensitive workloads, Gcore offers highly secure virtual cloud servers with Intel SGX support. The technology provides extra security such that only authorized users can access the encrypted data.
An assessment of your specific needs and circumstances is important before deciding to switch to cloud, but in almost all cases, it’s a move worth making.
Examples of Cloud Servers
Most organizations and individuals are using cloud servers in one way or another. Some use cases include email, file storage, and web applications. The cloud servers power major platforms and diverse application types, such as Software as a Service (SaaS,) Infrastructure as a Service (IaaS,) and Platform as a Service (PaaS.) Let’s take a look at two examples: Dropbox and Gcore.
Dropbox is a popular web-based file storage, sharing, and synchronization platform. It allows users to store files from their computers and access them from anywhere over the internet and supports real-time collaboration.
Gcore provides customizable cloud computing, CDN, infrastructure, security, and other services to meet computing needs across all industries. These include:
- Computing
- Bare Metal
- Object Storage Cloud
- Containers & Managed Kubernetes Hosting
- Hybrid Cloud
- AI platform
Conclusion
Cloud servers provide customers with a cost-effective solution to meet varying workloads on demand. We have learned about the cloud-based server, how it works, its benefits, and the type to deploy. The next step is to look for a reliable provider with the capacity and ability to meet your needs, which means balancing a number of complex factors.
Choosing the right cloud service provider is critical to achieving your organization’s objectives and success. It’s vital to opt for a service that meets both your current and future needs. At Gcore, we offer high-performance, scalable, affordable cloud servers to support customers and industries with different needs and workloads.
To learn more about Gcore, check out our cloud server products or talk to one of our experts for a free consultation on deploying your cloud servers and improving your operations.
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.