Your CFO's email account gets compromised overnight. By morning, cybercriminals have downloaded client banking information, stolen sensitive financial data, and grabbed credentials to your company's bank accounts. This isn't hypothetical, it's a reality costing organizations billions annually, with the majority of financial losses coming from targeted attacks where hackers manually exploit stolen credentials.
The threat goes far beyond executive accounts. Any login-protected account, from employee email and banking to social media and corporate systems, can become an entry point for fraud, data theft, and larger-scale breaches. Financial gain drives these attacks, whether through direct fund transfers, cryptocurrency theft, or selling your private information on the dark web. Once inside, attackers don't just steal. They change account details, launch phishing campaigns from your accounts, and use your access as a stepping stone to infiltrate your entire network.
You'll learn exactly how these attacks unfold, what makes certain accounts particularly vulnerable, and what multi-layered security strategies actually work to detect and prevent unauthorized access before criminals can exploit your credentials.
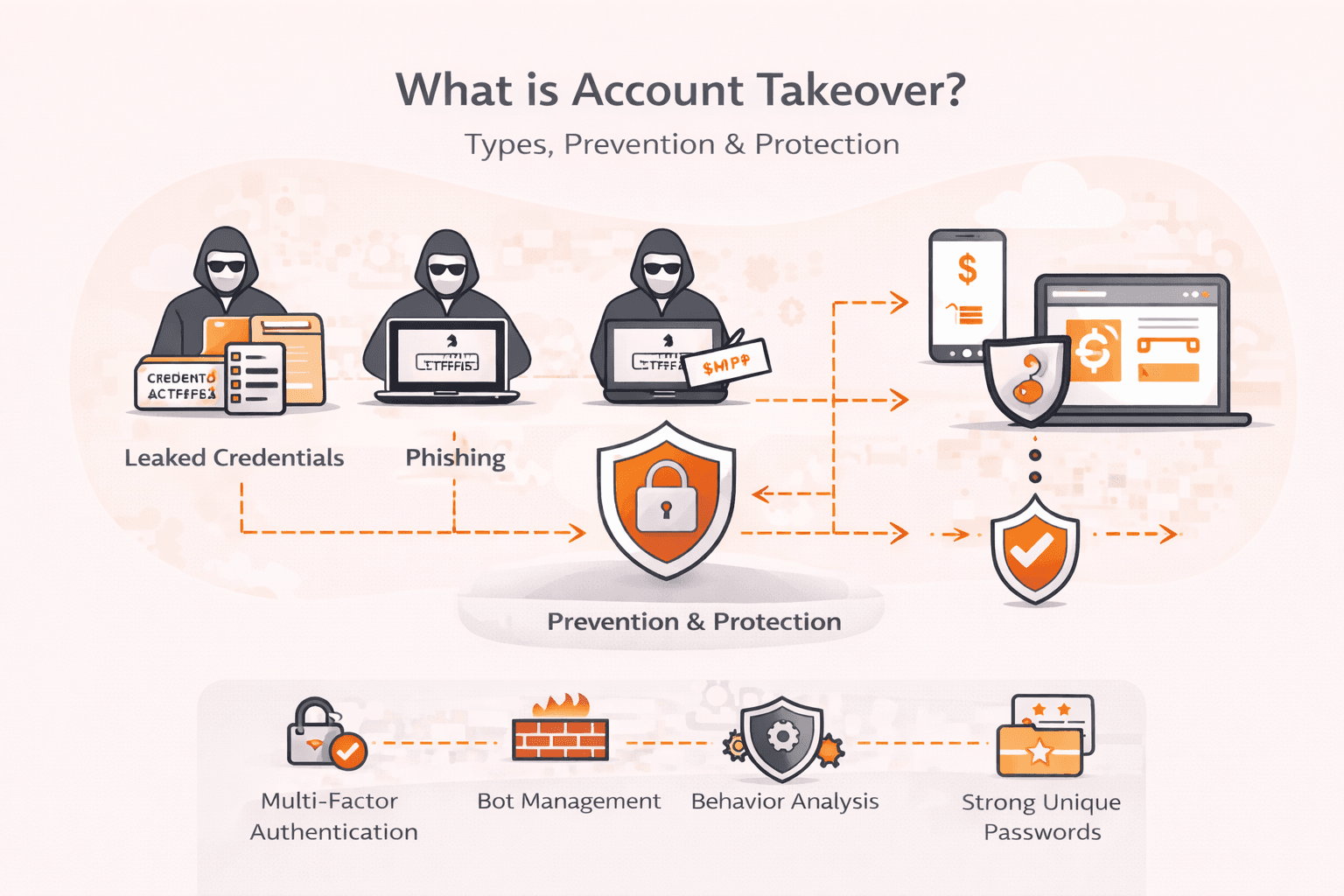
What is account takeover?
Account takeover happens when cybercriminals gain unauthorized access to someone's account using stolen or compromised login credentials. Once inside, attackers can steal money, extract sensitive data, send phishing emails to contacts, or use the account as a launching point for broader attacks against an organization. Any account protected by a username and password becomes a potential target, from personal email and banking to corporate employee portals and cloud services.
The threat affects both individuals and businesses, but the impact varies dramatically. When hackers take over a consumer banking account, they might initiate wire transfers or change withdrawal settings to pocket funds directly. In corporate environments, the stakes escalate. A compromised CFO email account could expose client banking information, organizational financial records, or credentials to additional business-critical systems. What makes account takeover particularly dangerous is its versatility. Attackers don't just steal what's immediately visible. They often conduct reconnaissance, mapping out network access and privileges before launching ransomware attacks or business email compromise scams.
Financial gain drives the vast majority of these attacks (over 90% according to Verizon's research), with targeted methods like phishing and social engineering proving far more damaging than automated credential stuffing. Criminals acquire login credentials through data breaches, dark web marketplaces, malware, or by simply tricking users into handing over their passwords. The timeline matters too. Targeted attacks typically happen within 18 to 24 months after a breach, before those credentials flood dark web markets and lose their exclusivity value.
How does account takeover happen?
Account takeover happens through a multi-stage process that starts with credential acquisition and ends with account exploitation. Attackers first obtain login credentials through data breaches, phishing campaigns, social engineering tactics, or by purchasing stolen credentials from dark web marketplaces. They might also use brute force attacks, testing common passwords against usernames, or deploy malware to capture keystrokes and login information.
Once attackers have valid credentials, they test them against target accounts. Because many people reuse passwords across multiple sites, credentials from one breach often unlock accounts on completely different platforms. This is called credential stuffing, and it's alarmingly effective.
After gaining access, attackers move quickly. They'll often change account details like email addresses or security questions to lock out the legitimate owner. From there, the exploitation phase begins. Financial theft is by far the most common motivation. Attackers initiate wire transfers, change banking details, or make fraudulent purchases. But that's not all. They might steal sensitive data to sell on the dark web, use the compromised account to launch phishing attacks against contacts, or establish persistent access for future attacks.
The timeline matters too. Targeted account takeover attacks typically occur within 18 to 24 months after a breach, before credentials get widely distributed on the dark web. This window represents the highest risk period for affected accounts.
What are the main targets of account takeover attacks?
Account takeover attacks target any system or account that relies on login credentials for access. These attacks don't discriminate. Criminals go after both individual users and organizations, focusing on accounts that offer the highest potential return through financial theft, data access, or further exploitation.
The main targets are listed below.
- Financial accounts: Banking platforms, investment accounts, and payment services sit at the top of attackers' target lists. Once inside, criminals can initiate wire transfers, change linked bank account details, or sell stocks to pocket the returns. The motivation here is straightforward, direct access to money.
- Email accounts: Corporate and personal email accounts serve as master keys to other systems. Attackers use compromised email to reset passwords for other services, launch phishing campaigns against contacts, or conduct business email compromise (BEC) scams. A CFO's email account, for example, can provide access to client banking information and organizational financial data.
- E-commerce accounts: Online shopping platforms store payment methods, shipping addresses, and purchase history. Criminals exploit these accounts to make fraudulent purchases, steal stored credit card information, or access loyalty program rewards. The combination of saved payment data and quick checkout features makes these particularly attractive targets.
- Social media profiles: These accounts offer value beyond the obvious. Attackers use them to spread malware, conduct social engineering against the victim's network, or damage personal and brand reputations. They're also reconnaissance goldmines, revealing security question answers and personal details useful for further attacks.
- Cloud service accounts: Access to cloud platforms opens doors to sensitive business data, application credentials, and infrastructure controls. Cybercriminals exploit these accounts to steal intellectual property, deploy ransomware, or pivot to other connected systems. IT, HR, and management accounts face elevated risk because of their privileged access levels.
- Healthcare portals: Patient portals and medical accounts contain valuable personal information, including Social Security numbers, insurance details, and medical histories. This data sells well on dark web marketplaces and can be used for identity theft or insurance fraud.
- Cryptocurrency wallets: Digital currency accounts represent high-value targets with often irreversible transactions. Once attackers gain access, they can transfer funds immediately, and the decentralized nature of cryptocurrency makes recovery nearly impossible.
- Travel and loyalty programs: Airline miles, hotel points, and reward program accounts have real monetary value. Criminals drain these accounts to book travel for resale or convert points to gift cards, causing both financial loss and program devaluation for legitimate users.
What are the warning signs of account takeover?
Warning signs of account takeover are unusual activities and behavioral anomalies that indicate unauthorized access to user accounts. The signs are listed below.
- Unexpected login notifications: Users receive alerts about account access from unfamiliar devices, locations, or IP addresses they don't recognize. These notifications often indicate someone else has successfully entered the account using compromised credentials.
- Changed account details: Email addresses, phone numbers, passwords, or security questions get modified without the legitimate user's knowledge. Attackers make these changes to lock out the real owner and maintain persistent access.
- Unusual transaction activity: Bank accounts show unauthorized withdrawals, purchases appear on credit cards, or cryptocurrency transfers occur without user initiation. Financial theft is the most common motivation behind account takeover attacks, with the majority of losses coming from targeted attacks.
- Failed login attempts: Multiple unsuccessful sign-in tries from different locations suggest attackers are testing stolen credentials through brute force methods. You'll often see these attempts clustered in short time periods.
- Suspicious outgoing messages: Friends, colleagues, or contacts receive phishing emails, spam, or unusual requests from the compromised account. Attackers use hijacked accounts to launch business email compromise scams and spread malware to connected networks.
- Missing or altered data: Files disappear from cloud storage, emails get deleted from inboxes, or account history shows gaps. Cybercriminals often erase evidence of their activities or steal sensitive information for ransom or dark web sales.
- Locked account access: The legitimate user can't log in because passwords no longer work or accounts become disabled. This happens when attackers change credentials to maintain exclusive control over the compromised account.
- New device authorizations: Account settings reveal unfamiliar devices or applications with granted access permissions. Attackers add their own devices to ensure continued entry even if passwords get reset.
Why do cybercriminals target accounts for takeover?
Cybercriminals target accounts for takeover because financial gain drives the vast majority of these attacks, making them one of the most profitable forms of cybercrime. Once attackers control your account, they can steal funds directly, drain cryptocurrency wallets, or sell your personal information on dark web marketplaces.
The returns don't stop at immediate theft. Compromised accounts give attackers access to sensitive data they can hold for ransom or use in future attacks against you or your contacts. A single breached email account can expose banking details, client information, and credentials for other services, all valuable commodities in underground markets.
Account takeovers also serve as entry points for larger operations. Attackers use compromised employee accounts to launch business email compromise scams, where they impersonate executives to authorize fraudulent wire transfers. They'll exploit elevated privileges in IT or management accounts to move laterally through corporate networks, bypassing security controls that would stop external intrusions.
The combination of high profitability and multiple exploitation paths makes account takeover attacks particularly attractive to cybercriminals. Your compromised credentials can generate revenue through direct theft, data sales, ransomware deployment, and fraud schemes, often all from a single successful breach.
How to prevent account takeover attacks?
You prevent account takeover attacks by using multiple security layers that protect credentials, detect suspicious behavior, and limit damage if an account gets compromised.
- Enable multi-factor authentication (MFA) across all accounts. This adds a second verification step beyond passwords, making it far harder for attackers to access accounts even with stolen credentials. Use authenticator apps or hardware tokens rather than SMS-based codes, which are vulnerable to SIM swapping attacks.
- Deploy AI-based anomaly detection to flag unusual login patterns. Monitor for suspicious signals like login attempts from new locations, unusual access times, or rapid changes to account settings. These behavioral analytics can catch compromised accounts before attackers cause significant damage.
- Use strong password policies and credential monitoring. Require passwords of at least 12 characters with complexity requirements, and scan for credentials exposed in known data breaches. Force password resets when breached credentials are detected in your systems.
- Use web application firewalls (WAF) to block automated attacks. Configure rate limiting to prevent brute force attempts, and deploy CAPTCHA challenges for suspicious login patterns. This stops attackers from testing large lists of stolen credentials against your systems.
- Monitor privileged accounts with heightened scrutiny. IT, HR, and management accounts need extra protection because they provide access to sensitive systems and data. Require additional authentication steps and log all activities from these high-value accounts.
- Train employees to recognize phishing and social engineering tactics. Since the majority of account takeover losses come from targeted attacks like phishing, regular security awareness training helps employees spot credential theft attempts before they succeed.
- Use session management controls and device fingerprinting. Limit concurrent sessions, automatically log out inactive users, and track device characteristics to identify when the same credentials are used from multiple locations simultaneously.
The key thing is combining prevention and detection. No single control stops all attacks, but layered defenses make account takeover significantly harder and catch breaches faster.
How can Gcore help protect against account takeover?
Gcore protects against account takeover through the Web Application Firewall and bot management solutions that operate across 210+ global PoPs. The Gcore platform identifies and blocks credential-stuffing attacks, brute-force login attempts, and suspicious authentication patterns before they reach your application.
You'll get real-time threat intelligence combined with rate limiting, geo-blocking, and device fingerprinting to distinguish legitimate users from attackers. This matters because the majority of account takeover losses come from targeted attacks that traditional security controls miss. The behavioral analytics catch anomalies like unusual login locations, device changes, and access pattern shifts that signal compromised credentials.
The edge infrastructure processes security rules with sub-30ms latency, so you can enforce strict authentication controls without degrading user experience. When an attack hits, the distributed network absorbs malicious traffic at the edge rather than letting it flood your origin servers.
Explore Gcore application security solutions at gcore.com/cloud.
Frequently asked questions
What's the difference between account takeover and data breach?
A data breach is when attackers steal credentials from a company's database, while account takeover is when those stolen credentials get used to access someone's actual account. Think of it this way: the breach exposes your password, but the takeover is when someone logs in as you and starts changing settings or stealing money.
How much damage can account takeover cause to businesses?
Account takeover can devastate businesses through direct financial theft, regulatory penalties for data breaches, operational disruption, and severe reputational damage that drives customers to competitors. A single compromised CFO account, for example, can expose client banking information, organizational financial data for ransom, and credentials for financial applications, leading to losses that extend far beyond the initial breach.
Is two-factor authentication enough to prevent account takeover?
No, two-factor authentication significantly strengthens account security but doesn't guarantee complete protection against all account takeover attacks. Advanced techniques like SIM swapping, social engineering against support staff, and session hijacking can bypass MFA, which is why organizations need layered defenses including behavioral monitoring and employee security training.
What should I do if my account has been taken over?
Immediately change your password, enable multi-factor authentication, and review recent account activity for unauthorized transactions or changes. Contact the service provider's security team to report the breach and monitor your other accounts for suspicious activity, as attackers often use stolen credentials across multiple platforms.
How quickly can account takeover attacks be detected?
Detection speed varies widely, from real-time for suspicious login patterns to days or weeks if the attacker mimics normal behavior. Organizations using AI-based behavioral analytics and continuous monitoring can catch anomalies within minutes, while manual reviews of compromised accounts may take significantly longer.
What industries are most vulnerable to account takeover?
Financial services, e-commerce, and healthcare face the highest account takeover risk because of the direct financial access and valuable personal data these accounts contain. Cloud-based SaaS platforms and social media accounts are increasingly targeted as attackers use them for reconnaissance, business email compromise, and launching secondary attacks against connected organizations.
Can account takeover happen on mobile applications?
Yes, mobile applications are highly vulnerable to account takeover attacks through the same credential theft methods that target web platforms: phishing, malware, data breaches, and brute force attacks. Mobile apps face additional risks from insecure device storage, compromised operating systems, and man-in-the-middle attacks on public WiFi networks.
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.