Slots and secret rollover
Usingget_effective_at to access different slots within a given secret and how to use slots.
InfoFor more information regarding secret usage in applications see the JavaScript SDK and the Rust SDK
Example 1 (Slots as indices)
Validating a token against a specific version of a secret. Having created a secret: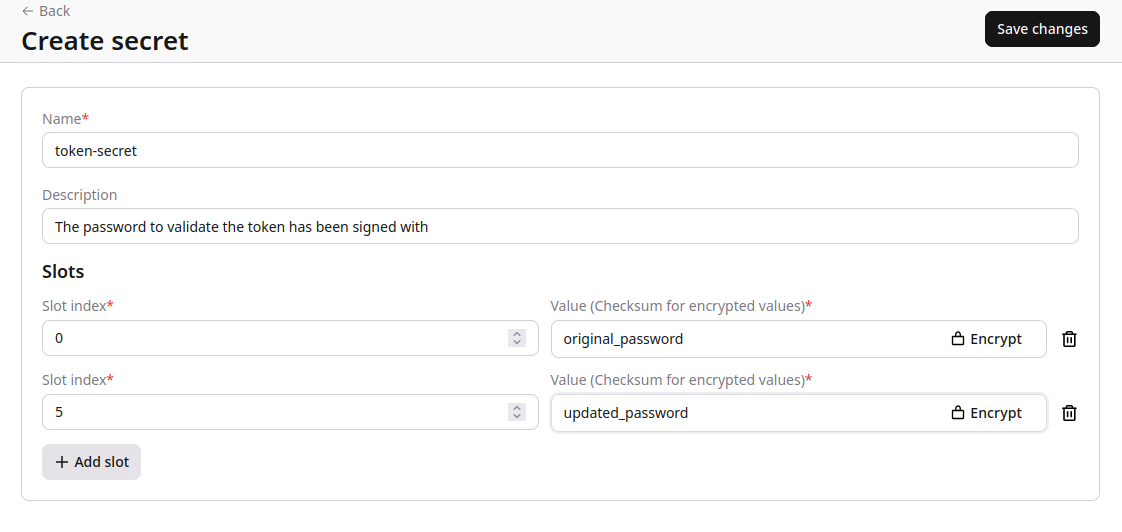
slot value within the tokens claims as to which
password it should validate against. This would allow you to slowly rollover from one password to
another and keep all users able to refresh their tokens without issues, as each users token also
carries the data to know which password was still in use when it was issued.
It always returns effectiveAt >= secret_slots.slot
So a request to:
secret::get_effective_at("token-secret", 0)would returnoriginal_passwordsecret::get_effective_at("token-secret", 3)would returnoriginal_passwordsecret::get_effective_at("token-secret", 5)would returnupdated_passwordsecret::get_effective_at("token-secret", 7)would returnupdated_password
>= logic makes it very easy to implement the following example.
Example 2 (Slots as timestamps)
Validating a token against a specific version of a secret using timestamps: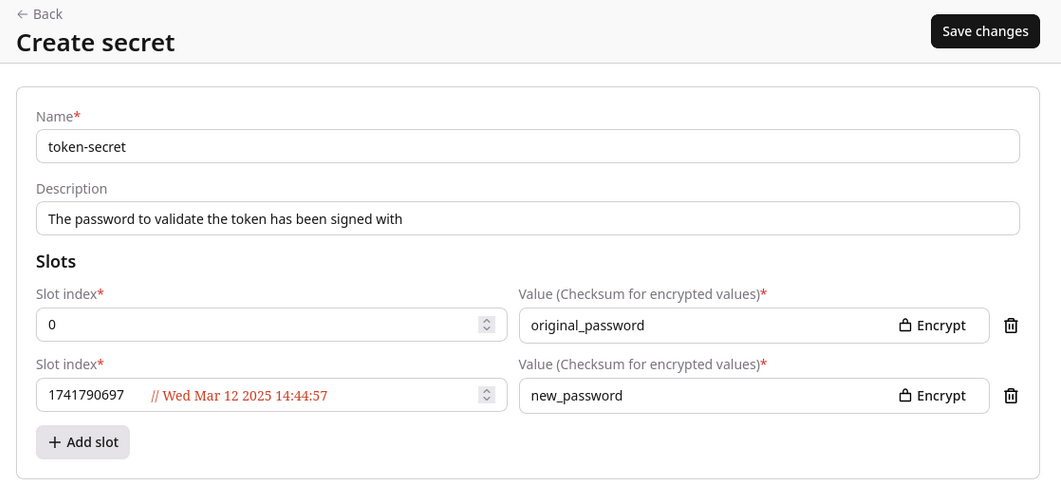
iat claim time before 1741790697 would use the
original_password and any token after this time would start to use the new_password