InfoThe IP Spotlight feature is available on the Enterprise plan. To enable it for your domain, contact our sales team.
Analyze an IP
IP Spotlight provides IP details as its source, total number of requests, destinations, whois data, and whether it has been involved in any malicious activity against other domains within our network. To check an IP address, follow these steps:- In the Gcore Customer Portal, navigate to WAAP > IP Spotlight.
- In the domain dropdown at the top of the page, select the needed domain.
- In the address field, enter the IP address that you want to inspect.
- Click the Analyze IP button.
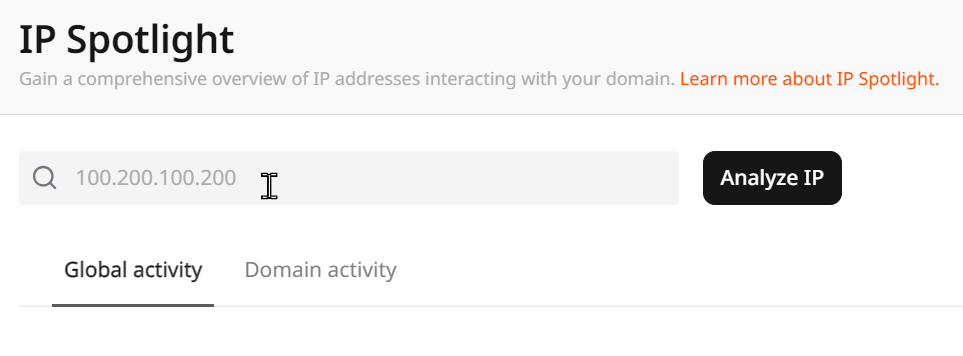
- All collected information about the address will appear on the Global Activity and Domain Activity tabs
Inspect global and domain activity
We analyze IP addresses past activities in two areas: activity across the whole Gcore network (global activity) and interactions specific to your domains (domain activity).Global activity
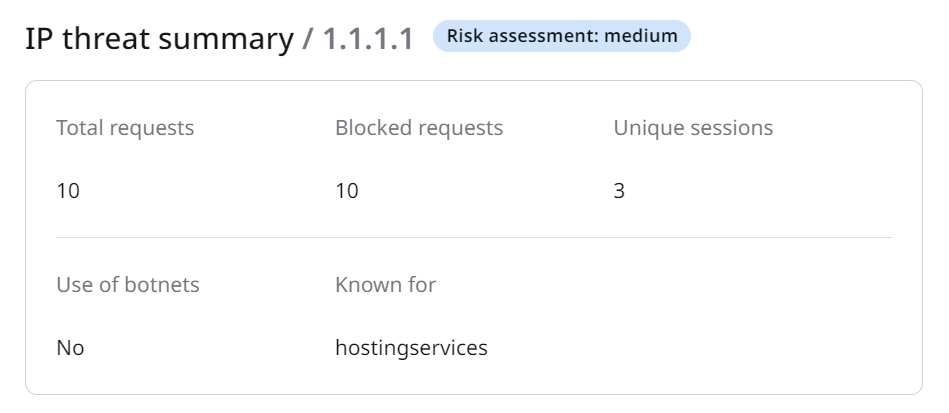
The Global activity tab shows generic IP information and insights gathered from other domains on our platform. This data is more aggregate than the domain activity.IP threat summary
In this section, you can find out if we detected any threats to resources in our network in the past. The section includes the following details:- The risk assessment score, which has five levels:
- No risk
- Low risk
- Medium risk
- High risk
- Extreme risk
- Total number of requests
- Number of blocked requests
- Number of unique sessions
- Information if the IP address was used for botnet attacks
- The threats and services the IP is known for. The information will be presented as tags associated with the IP addresses, such as SQL injection, injection attacks, or headless browsers.
IP risk assessment
We query multiple external and internal databases to retrieve and store information about an IP address. This allows IP Spotlight to provide a risk assessment and score related to the IPs’ threat level. This score, ranging from Low to Extreme, allows you to determine what actions to take against any flagged IP that sends requests to your domain. The High and Extreme risk scores are typically assigned to addresses that exist on external block lists, participate in DDoS attacks, or make a higher number of requests than usual.InfoIf the IP is no longer associated with malicious activity, its score might decrease from extreme to Low or even No risk over time.
WhoIs
This section provides information from the global WHOIS database. It includes details like the name and type of organization that owns the address, its location, related IP ranges, contact information for reporting abuse, and registry details.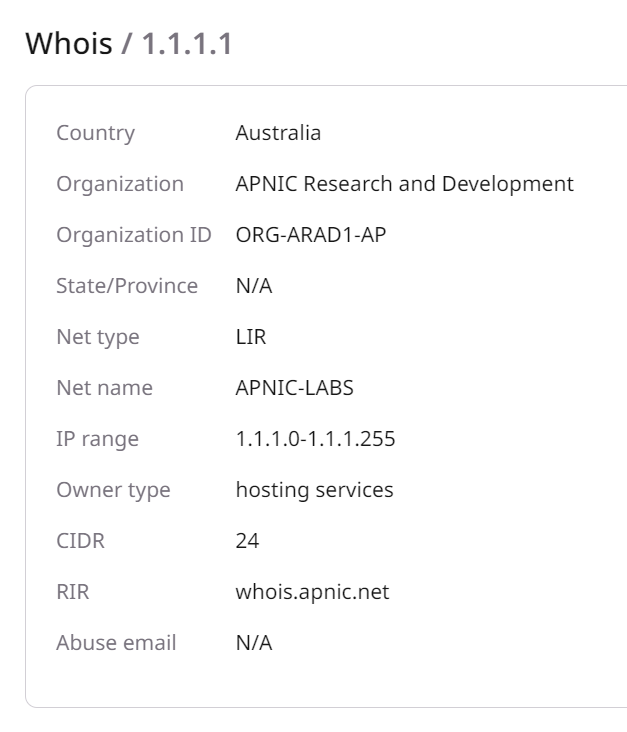
Top 10 attack targets
This section provides you with a map that shows the targets of past attacks originating from the scanned address. It also includes a list of the top 10 targets of these attacks.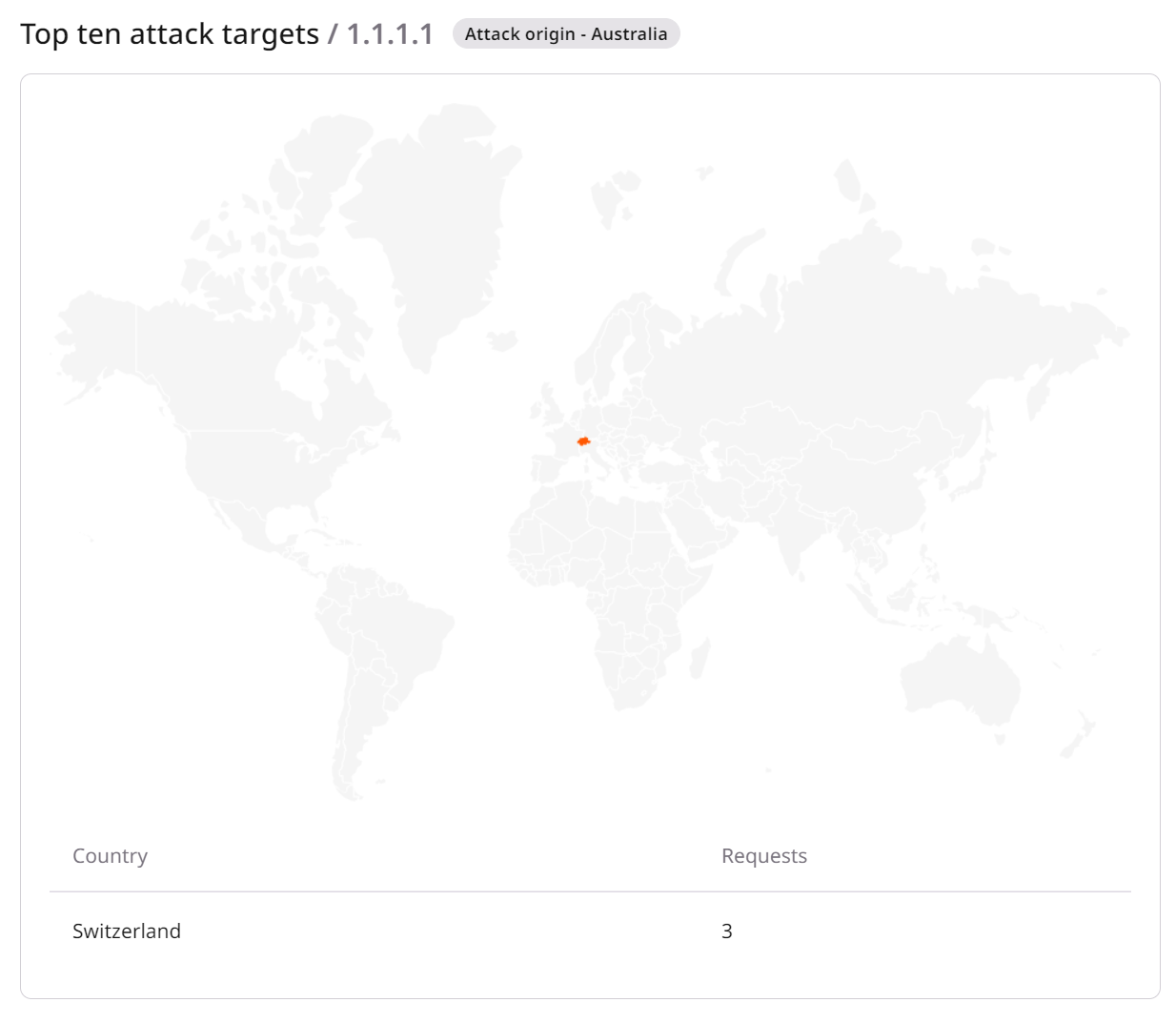
Attack distribution over time
This section displays a graph with the number of blocked requests that are filtered by the triggered WAF policy.Domain activity
InfoTo view this information, you need to have WAAP enabled for your domain.
Overview
In this section, you can find the following information about the address’ activity on your domain:- Total number of requests
- Number of blocked requests
- Number of unique sessions
Top 10 triggered policies
This section provides a list and donut chart of policies applied to the IP and a graph displaying how many times each policy triggered.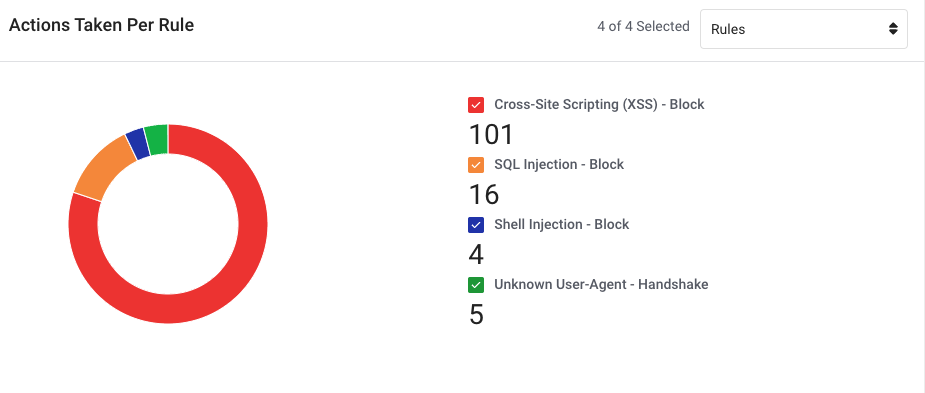
Top 10 visited URLs
This section provides you with top 10 URL paths visited by the IP address, along with the number of times these URLs were requested.Top 10 sessions
This section contains a table displaying information about the top 10 sessions from the specified IP to your domain. You can check the session ID, the date the session took place, the time-to-live (TTL) of the request, if it was blocked, and the session duration.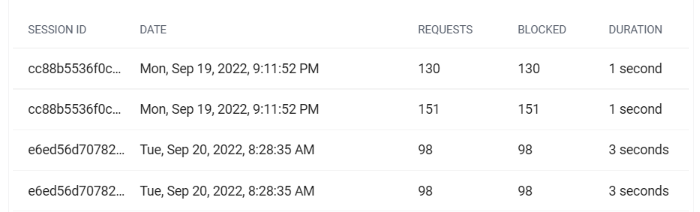
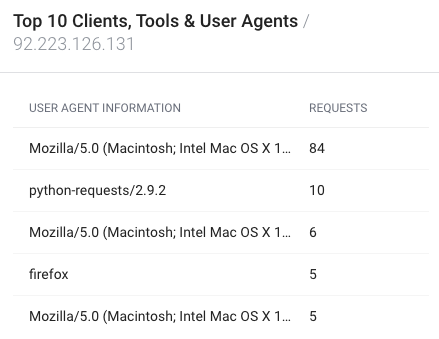
Top 10 user agents
Here, you find a table with information about the top 10 user agents that accessed your domain from the specified IP.