We provide DDoS protection for Bare Metal and Dedicated Servers. You can also get DDoS protection for equipment that’s not hosted by Gcore.
InfoAfter we set up the DDoS protection, the main IP of your server will be changed for Hosting. It will stay the same for Bare Metal.
Activate protection for a GCore server
There are two options for setting up DDoS protection services:
- Apply predefined protection profiles.
- Request custom configuration. This is the only option available for the Hosting platform.
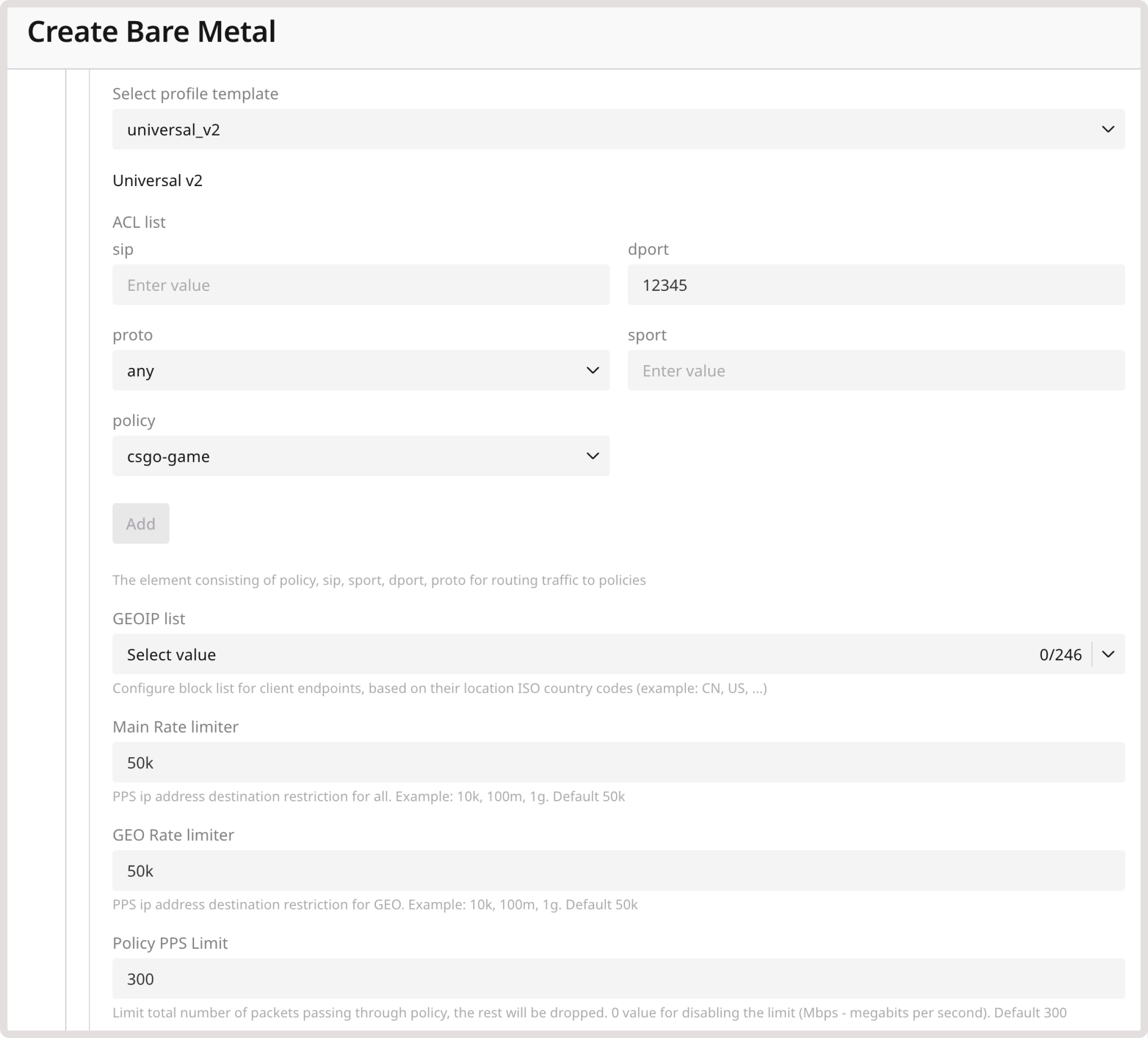
The predefined profiles are available on the Network tab in your server settings. For example, the following screenshot depicts the profile settings for Bare Metal:
If no predefined protection profile aligns with your requirements, contact the Gcore support team to request a custom configuration.
In your request, include the following information:
- Server ID
- Filled DDoS questionnaire
DDoS questionnaire
Complete the following questionnaire according to your infrastructure setup and DDoS protection requirements.
TipAll fields in the questionnaire are optional, but we recommend providing as much information as possible to help us configure DDoS protection settings that are best optimized for your infrastructure.
| Question | Your information |
|---|
| Specify IP addresses that should be added to the allowlist | |
| Do you want to configure the access control list? | |
| Do you want to set up game protection? | |
| Do you need to configure the GEO filter? | |
| Do you want to configure DNS protection? | |
| Do you want to configure RegEx-based filtering? | |
| Is your traffic encrypted by TLS protocol? | |
| Do you want to configure rate limiting for incoming traffic from your own IP range? | |
| Question | Your information |
|---|
| Clean traffic bandwidth in Mbps | |
| Question | Your information |
|---|
| What is your autonomous system number (ASN)? | |
| What IP prefixes do you want to announce /24? | |
| What’s your GRE tunnel endpoint? | |
| Protocol | Destination IP | Destination port | Service |
|---|
| | | |
| | | |
| | | |
| Protocol | Source IP | Source port | Destination IP | Destination port | Service |
|---|
| | | | | |
| | | | | |
| | | | | |
Activate protection for a third-party server
For detailed configuration instructions, refer to the Configure your infrastructure for Secure Transit guide.
Rent a new dedicated server with DDoS protection
The configuration for a rented dedicated server is almost identical to the activation of a DDoS protection for an existing server.
The key difference is that you first need to select and order the preferred configuration in the Dedicated Servers section of our website. After that, proceed with the same configuration steps that are outlined in the Activate protection for a Gcore server section.
Deactivate DDoS protection
To deactivate your server’s protection, contact the Gcore support team. We will stop the service. Note that the main IP of your server will be changed after deactivation.