What is the GRE protocol?
Generic Routing Encapsulation, or GRE, is a tunneling protocol that creates a virtual point-to-point connection between two endpoints over an IP network. The endpoints are usually routers or firewalls that are assigned IP addresses when connected with a GRE tunnel. Much like a real-life tunnel, a GRE tunnel acts as a pathway for data to travel from point A to point B.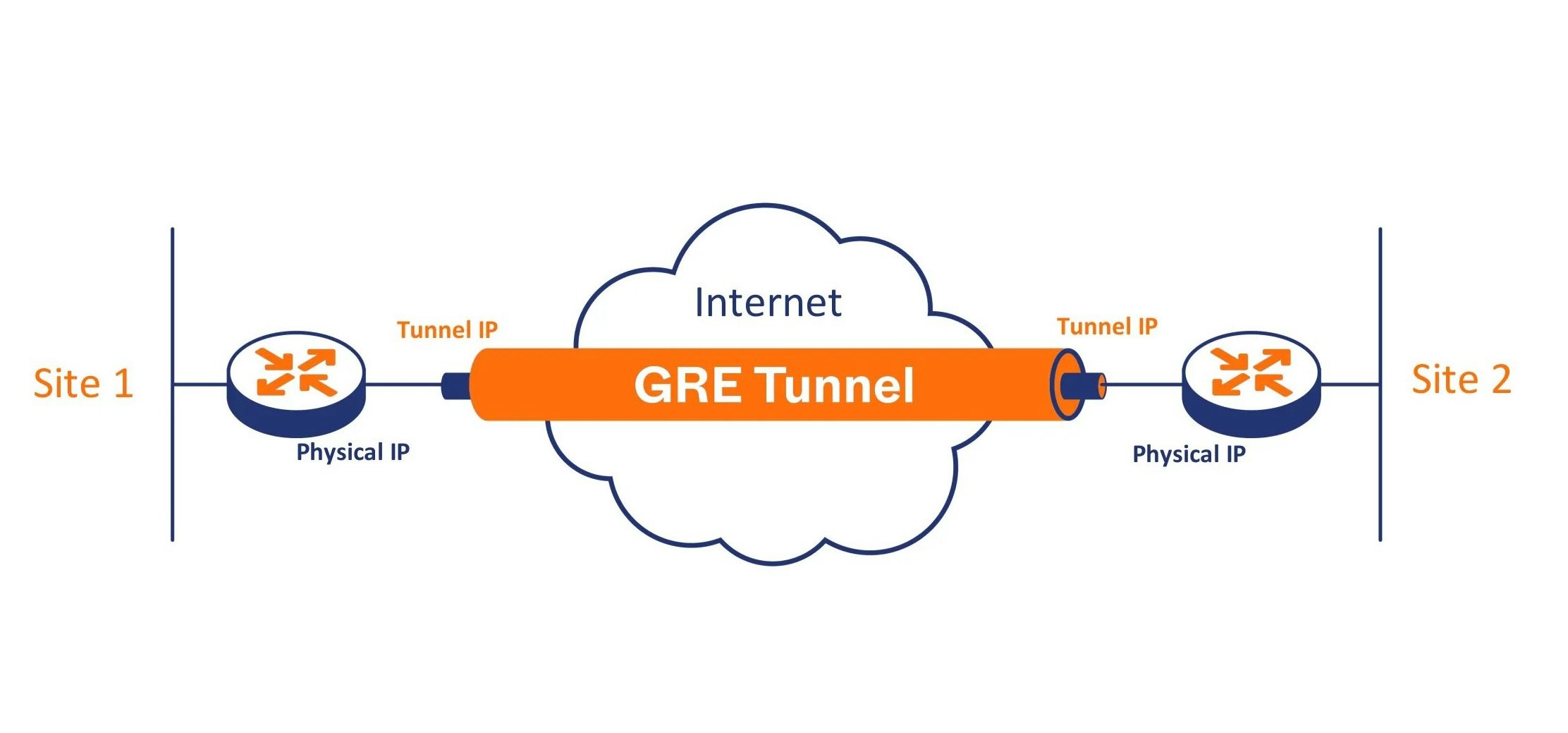
GRE header and network requirements
The GRE protocol adds an additional header to data packets, increasing the overall packet size. You should factor in this size increase before establishing a tunnel. MTU (maximum transmission unit) refers to the maximum size of a data packet that can be transmitted without fragmentation, while MSS (maximum segment size) refers to the maximum amount of TCP packet payload. When extra GRE bytes are added to the packet size, it can exceed the standard MTU and MSS limits, resulting in packet fragmentation. Fragmentation slows down delivery, increases resource usage, and may lead to packet drops. This can be avoided by reconfiguring MTU and MSS limits to accommodate GRE headers.What is the BGP protocol?
BGP, which stands for Border Gateway Protocol, is a routing protocol which provides information about all available data transmission paths between multiple autonomous systems that form the internet. Imagine the internet as a big interconnected network of cities, where each city is a network or an autonomous system (AS) with its unique address or IP prefix (range of IP addresses.) The roads between the cities are like the network links between different ASs. BGP routers in each city act as the GPS navigation system. They exchange routing information with neighboring cities (ASs) to determine the best routes for data to reach its destination. This routing information includes the available paths (highways/roads) and the associated metrics (e.g., link cost or traffic conditions.) Routing information can change in real-time due to network changes, link failures, or network administrators’ policy adjustments. BGP routers continuously exchange updates with neighboring routers to reflect these changes, ensuring that traffic is directed along the most optimal and reliable paths. For more information about BGP, please refer to our blog article.How do GRE and BGP work together?
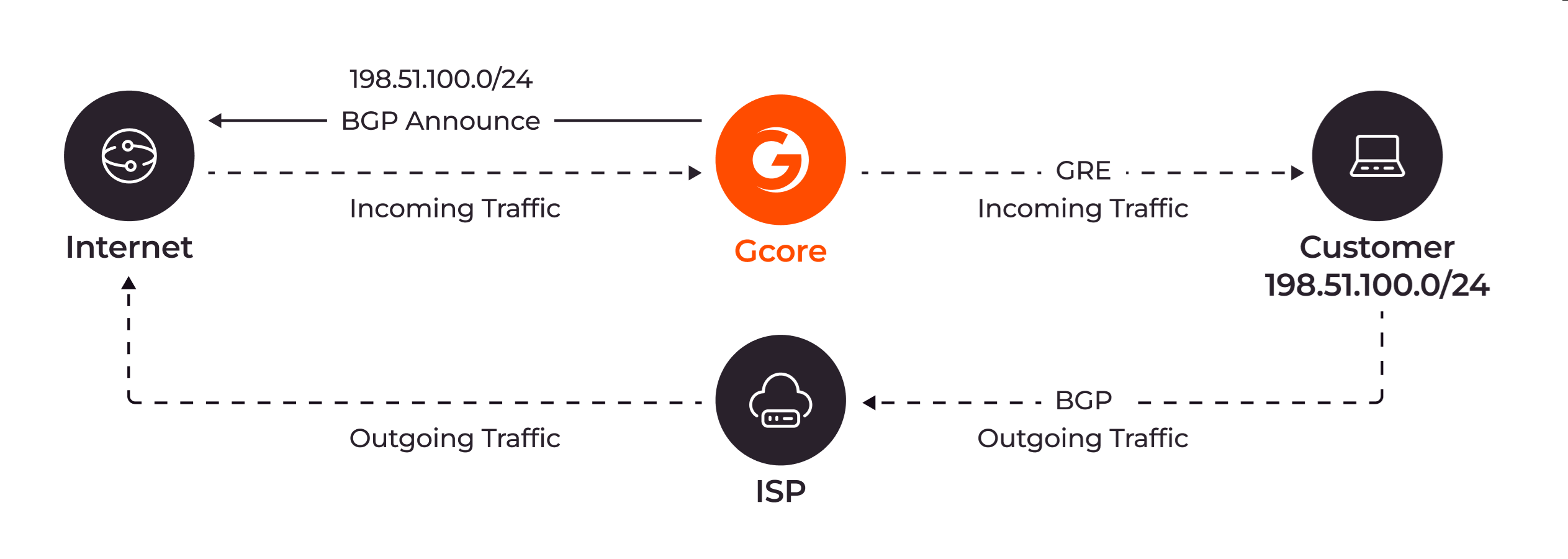
When building a GRE tunnel, you have to specify the address of the endpoint located at the other end of the tunnel. But the address specification is bidirectional: the recipient on the other end of the tunnel should also specify your address. This ensures that both endpoints know where to send and receive encapsulated packets. This is when BGP comes into play. Similarly to the real-world analogy, where GPS can help you understand the exact location of two cities that you want to connect with a tunnel, BGP will provide users with the information about each other. So when they access the BGP table, both of them can see the user on the other end of the tunnel, and they can set a GRE tunnel. By default, DDoS protection only handles incoming traffic (from the Internet to the customer’s network). Outgoing traffic from the customer’s servers back to clients is routed through the customer’s data center edge router, using its default routing table and uplinks to the Internet or ISP. This return traffic does not pass through Gcore or its tunnels.