Upload a PKCS12 file
If you already have a PKCS12 file containing your SSL/TLS certificate, certificate chain, and private key, you can quickly upload it to the Secrets Manager. To upload a secret as a PKCS12 file:- In the Gcore Customer Portal, navigate to Cloud.
- Open the Secrets Manager page.
- Click Create Secret.
- Enable Upload as PKCS12 file.
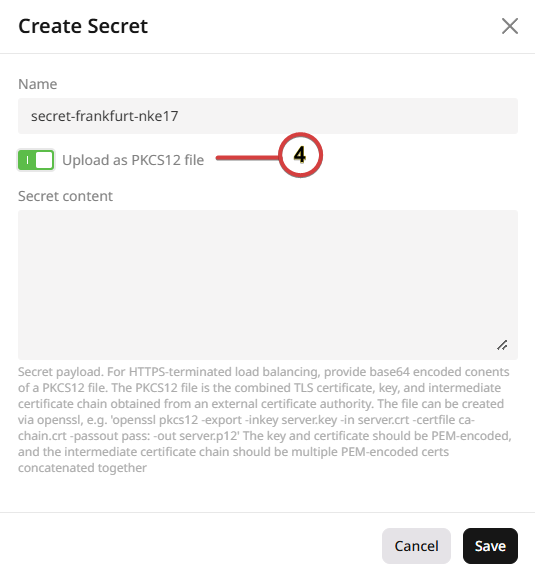
- Enter a name for your secret and choose your file.
- Click Save.
Add certificates directly
If you don’t have a PKCS12 file or prefer to add the certificate details individually, you can enter them directly in the Secrets Manager. To add a secret manually:- In the Gcore Customer Portal, navigate to Cloud.
- Open the Secrets Manager page.
- Click Create Secret.
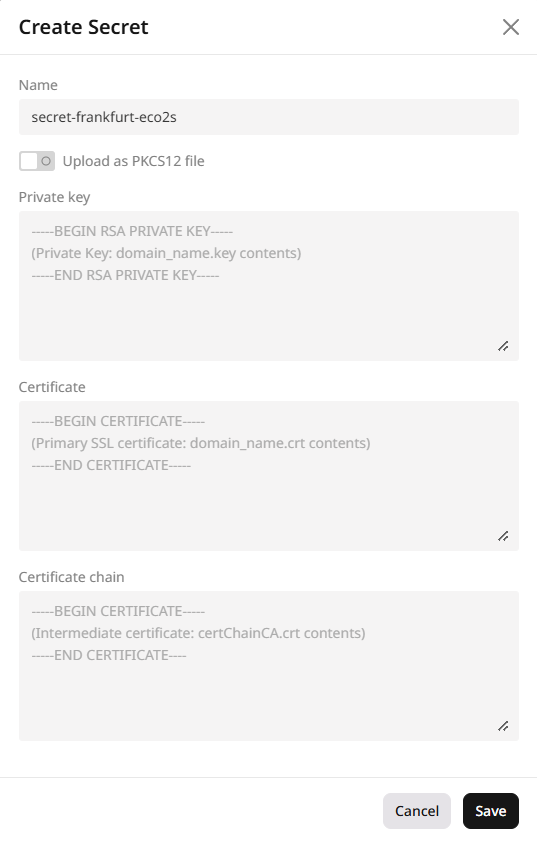
-
In the form that opens, fill in the following fields:
- Enter a name for your secret.
- Paste the content of your private key file.
- Paste the content of your main SSL/TLS certificate file.
- If required, paste the content of the certificate chain file. This should include root and intermediate certificates in the correct order.
- Click Save.
Create a PKCS12 file
PKCS12 (Public-Key Cryptography Standards) is a binary format for storing SSL/TLS certificate, certificate chain, and private key in one encrypted file. Basically, you “pack” the main SSL/TLS certificate, the certificate chain, and the private key into the PKCS12 file to transfer them easily. Each element is essential for establishing an HTTPS connection:- The main certificate is a digital signature of the site, which confirms that the resource actually belongs to you and not to criminals who impersonate you.
- The certificate chain is information about the CAs (certificate authorities) that participated in the issuance of your certificate and confirm its authenticity.
- The private key is a unique set of letters and numbers (key), using which the cryptographic algorithm will encrypt all data exchanged between the resource and a user.
1. Prepare certificate files
You need the SSL/TLS certificate for the domain, the chain of certificates, and the private key. The domain must be configured with a DNS A record with the virtual IP address of the Load Balancer (the IP is specified in the Load Balancers tab). If you are using our DNS zone, you can create an A record according to the instructions. Your domain will send requests to the IP of the balancer and it will distribute them among the machines. CA does not always send a client a chain of certificates along with the main certificate — sometimes it only sends the main one, because often it is enough for browsers to confirm the domain name. In this case, you can get the certificate chain yourself:- Download the root and intermediate certificates from the site of the CA that issued you the certificate.
- Create the file in any text editor.
- Inside the created file, place the contents of the certificates in the following order: root certificate, then intermediate certificates in order, the certificate for the domain in the end. Like this:
- Content of the root certificate (for example, CARoot.crt)
- Content of the intermediate certificate no. 1 (for example, Intermediate1.crt)
- Content of the intermediate certificate no. 2 (for example, Intermediate2.crt)
- Content of the certificate for the domain (for example, domain.crt)
2. Merge certificate files into PKCS12
Now you have all the files needed. There are several ways to merge them into PKCS12 format. Below we describe a common case — creating PKCS12 from PEM files. 1. Install OpenSSL. This is a library containing tools for working with SSL/TLS protocols. You can find installation links and instructions for working with OpenSSL on its official website. 2. Check if your certificate files are in PEM format. Such files must have the extension .pem, .crt, .cer or .key, begin with the line----- BEGIN CERTIFICATE ----- and end with the line ----- END CERTIFICATE -----. To see the beginning and the end of a file, open it in a text editor. 3. If some files are not in PEM, convert them using OpenSSL. Enter the command in OpenSSL, replacing the text in square brackets with your names:
For a .crt, .cer or .der file
3. Base64 encode
Encode the contents of PKCS12 file to base64. This can be done by entering the command in the console: For Windows OS----- BEGIN CERTIFICATE ----- and ----- END CERTIFICATE -----. They are generated automatically and you don’t need them. The rest of the text will be the content of the Secret.
For Mac OS
How to create a load balancer with an HTTPS listener
InfoYou cannot delete a secret that is currently used by a Load Balancer’s listener. To remove a secret, first delete the associated listener, then remove the secret. If needed, recreate the listener afterward.