Basics you need to know
What are service accounts? Service accounts are used to allow pods to read and use Kubernetes API objects as well as to create a kubeconfig file, which grants access to the Kubernetes objects limited to the namespace for any user or service. For more information,refer to the Kubernetes documentation: Managing Service Accounts. What is a namespace? In Kubernetes, a namespace is a method of organizing and isolating groups of resources within a single cluster. This helps various teams, projects, or customers to share a Kubernetes cluster. For more information, refer to the Kubernetes documentation: Namespaces.Add users with limited rights
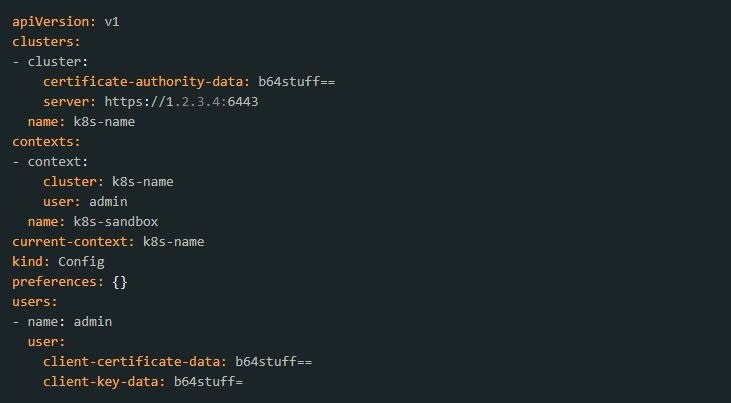
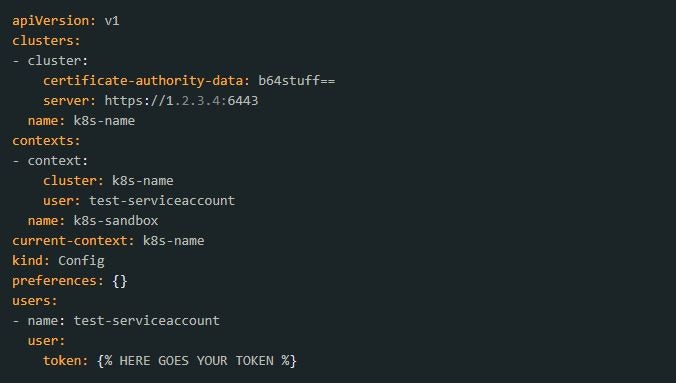
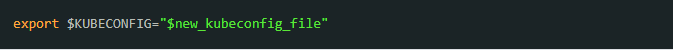
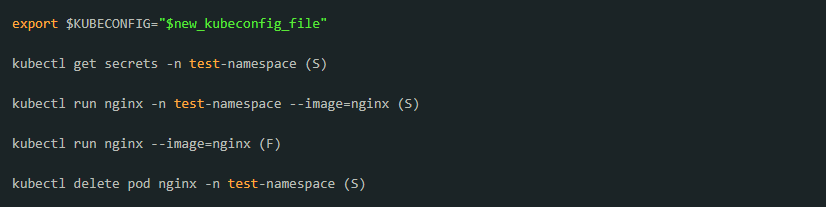
1. Create a namespace using kubectl. Enter the following command:_test-serviceaccount-token_-{% random characters here %} (of type kubernetes.io/service-account-token).