Step 1. Initiate the process
Open the “Kubernetes” tab and click Create Cluster.
Step 2. Select the region
Select a region —the location of the data center where your cluster will be deployed.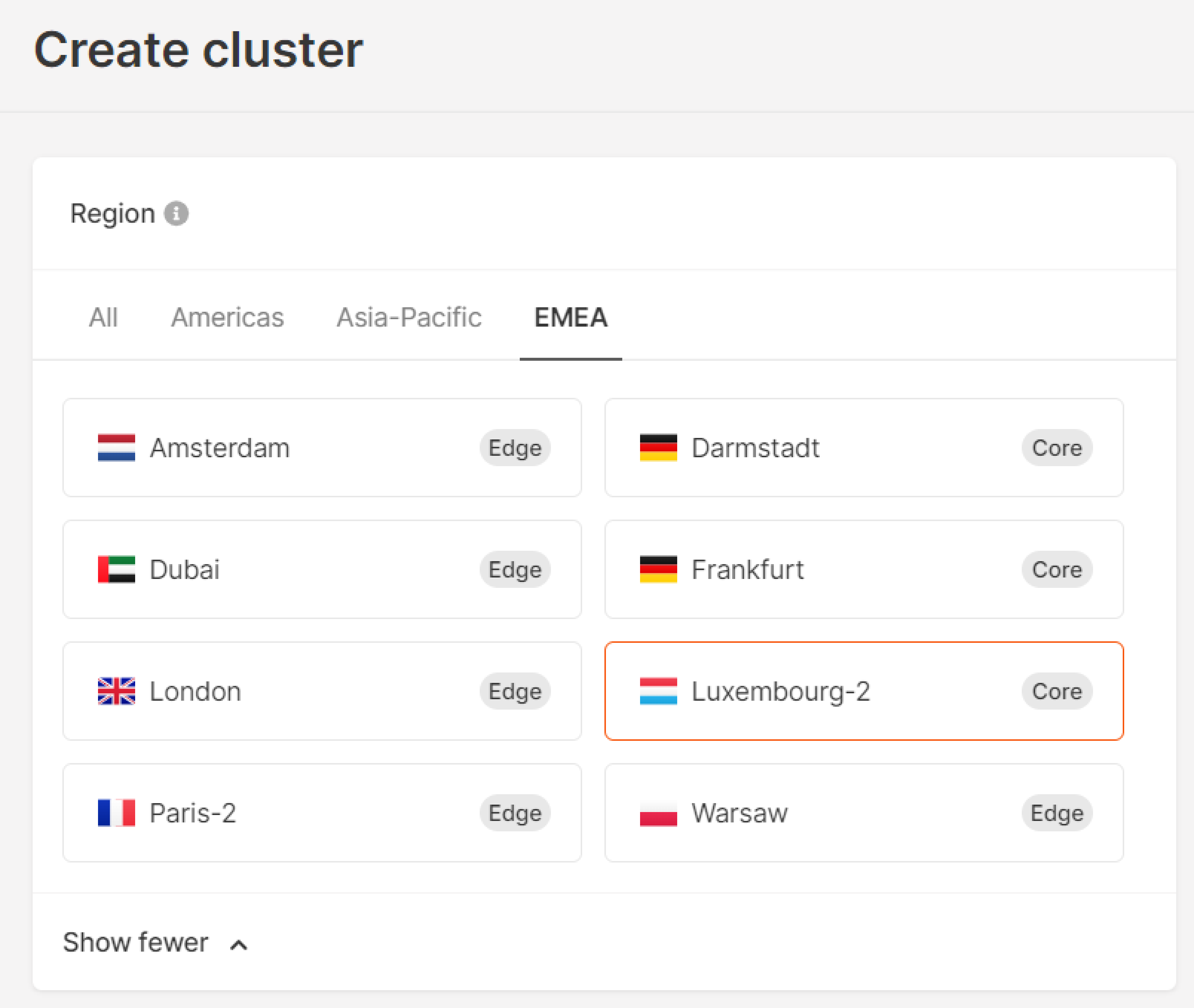
Step 3. Select the version
Select your Kubernetes cluster version from the dropdown menu.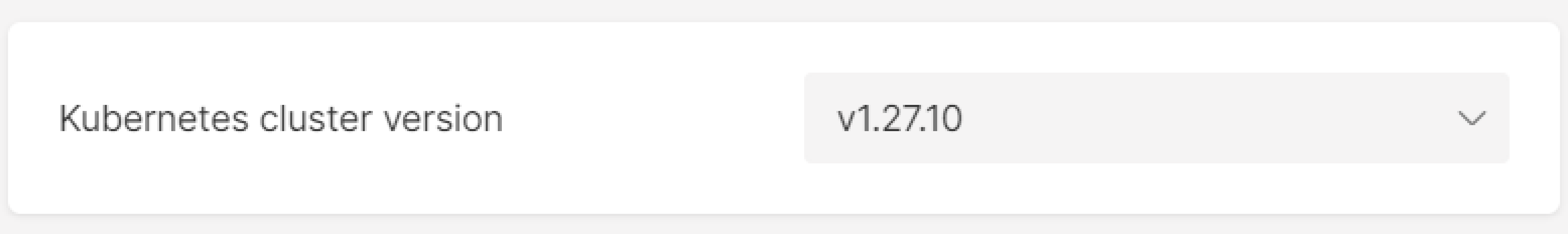
Step 4. Configure pools
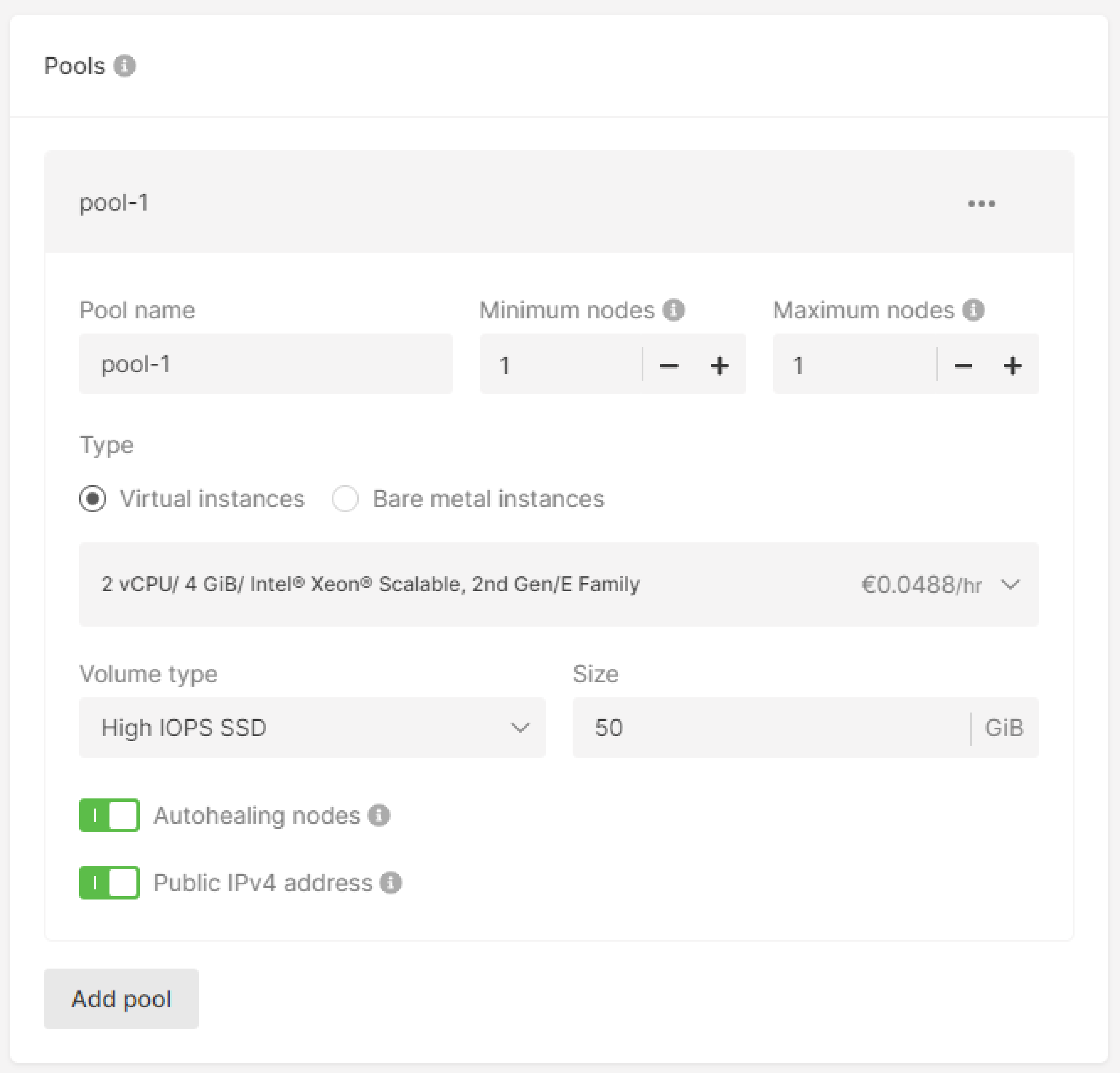
Under the Pools block, configure a pool. A pool is a set of cluster nodes with the same specifications.- Enter the Pool name.
- Set the minimum nodes and maximum nodes for autoscaling.
- Select the type of a worker node: Virtual Machine or Bare Metal.
- (Optional) Configure advanced pool settings. For an overview of advanced settings, check out the Create and configure a pool guide.
- Virtual Machine
- Bare Metal
Select the flavor, disk size in GiB, and disk type.The following Virtual Machine flavors are available:
- Standard. 2–4 times the memory of vCPUs
- vCPU. The number of vCPUs equals the amount of memory in GB
- Memory. Much higher memory than that of vCPUs-up to 8x more
- High Frequency. High CPU clock speed starting at 3.7 GHz in the basic configuration
- High IOPS SSD. A high-performance SSD block storage designed for latency-sensitive transactional workloads (60 IOPS per 1 GiB; 2.5 MB/s per 1 GiB.) The IOPS performance limit is 9,000. The bandwidth limit is 500 MB/s.
- Standard. A network SSD disk that provides stable and high random I/O performance and high data reliability (6 IOPS per 1 GiB; 0.4 MB/s per 1 GiB.) The IOPS performance limit is 4,500. The bandwidth limit is 300 MB/s.
- Cold (deprecated). A network HDD disk suitable for less frequently accessed workloads. The maximum number of IOPS is 1,000. The bandwidth limit is 100 MB/s. Please note that this option is unavailable in Manassas.
- Ultra (deprecated). The recommended network block storage option for non-critical data and workloads that are accessed less frequently. The maximum number of IOPS is 1,000. The bandwidth limit is 100 MB/s.
- SSD Low Latency. An SSD block storage designed for applications that require low-latency storage and real-time data processing. The IOPS performance limit is 50,00, with an average latency of 300 µs.
- Ensure the Autohealing nodes toggle is on to enable automatic recovery of failed nodes. When toggled on, this feature monitors node statuses. Upon detecting a non-working node, the autohealer initiates its replacement. If one of the machines fails, the application will not stand idle: The node(s) will be replaced on a working machine, and the app will keep working.
- (Optional) Enable the Public IPv4 address option to assign public IPv4 addresses to cluster nodes.
InfoIf you want to enable an IPv6 dual-stack for your cluster, at least one of the pools must have a public IPv4 address.
- Add as many pools as you need using the Add pool button.
Step 5. Select the CNI provider
Choose either the Cilium or Calico network stack. These provide networking and network security solutions for containers.- Cilium uses eBPF to inject functionality into the kernel and provides a broader range of additional features (load balancing, advanced security, failure detection, etc.) than Calico. You can add additional functions as required by checking the relevant box for DSR, tunneling, Load Balancer acceleration, and encryption.
- Calico uses a more conservative stack based on iptables.
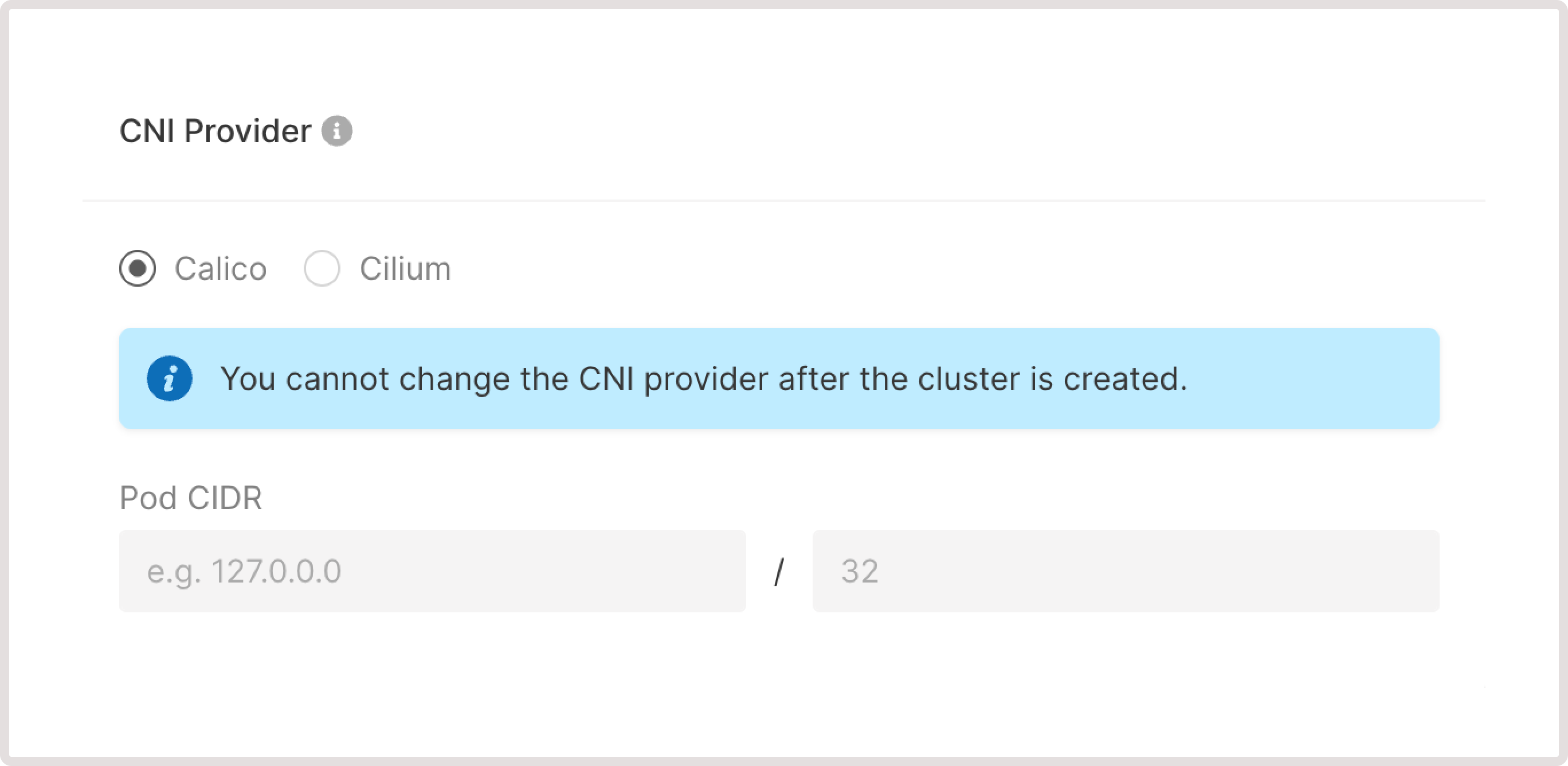
- For pods: 172.16.0.0/18
- For services: 172.24.0.0/18
- For pods: 172.16.0.0/17
- For services: 172.24.0.0/17

Step 6. Configure network settings
- Configure a network
- Configure a subnetwork
Add one or multiple network interfaces to your cluster.If you have previously created networks, select the correct network from the dropdown.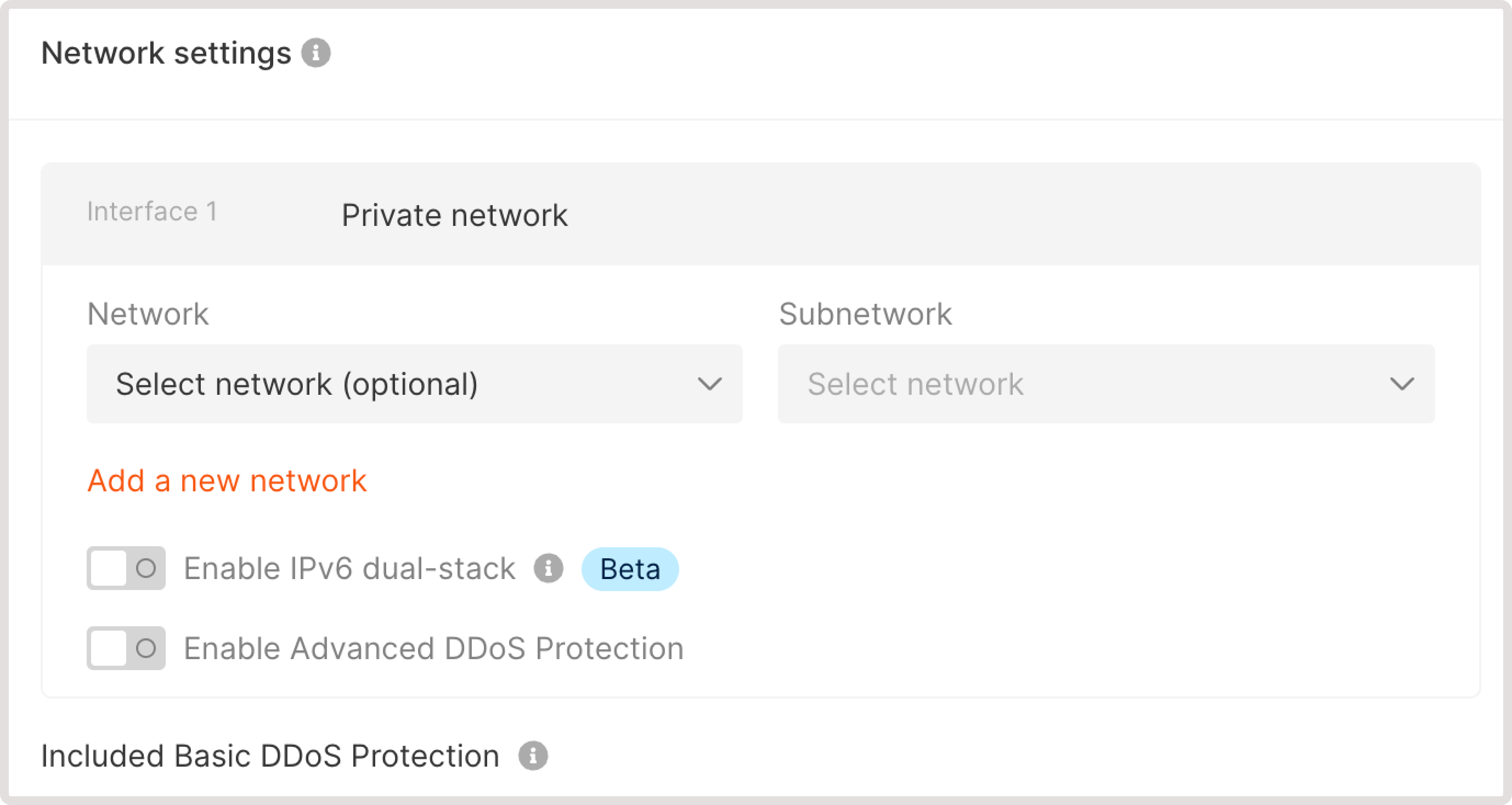


Advanced DDoS Protection
Advanced DDoS Protection
You can enable Advanced DDoS Protection for your private network. To do so, activate the Enable Advanced DDoS Protection toggle, open the drop-down menu, and select the desired template from the list. We currently support the following templates: CS:GO, Rust, ARK, Basic L3/L4, or TCP protection.The settings offered depend on the selected template. For example, for the Basic L3/L4 specify the uppermost threshold of attack in Gbps that our DDoS Protection can mitigate in the “Mitigation capacity” field.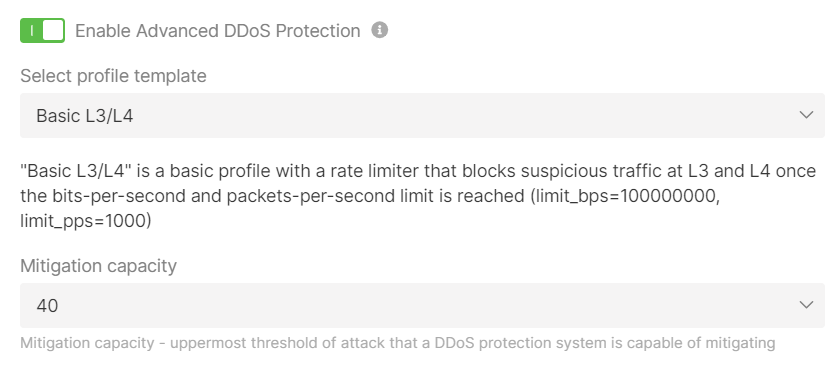

Step 7. Add an SSH key
Configure an SSH key to enable a remote SSH connection to all nodes. Select an existing key or create a new one. For details, consult our article on how to connect to your VM via SSH.
Step 8. Specify a cluster name
Name the cluster in the field as shown below.
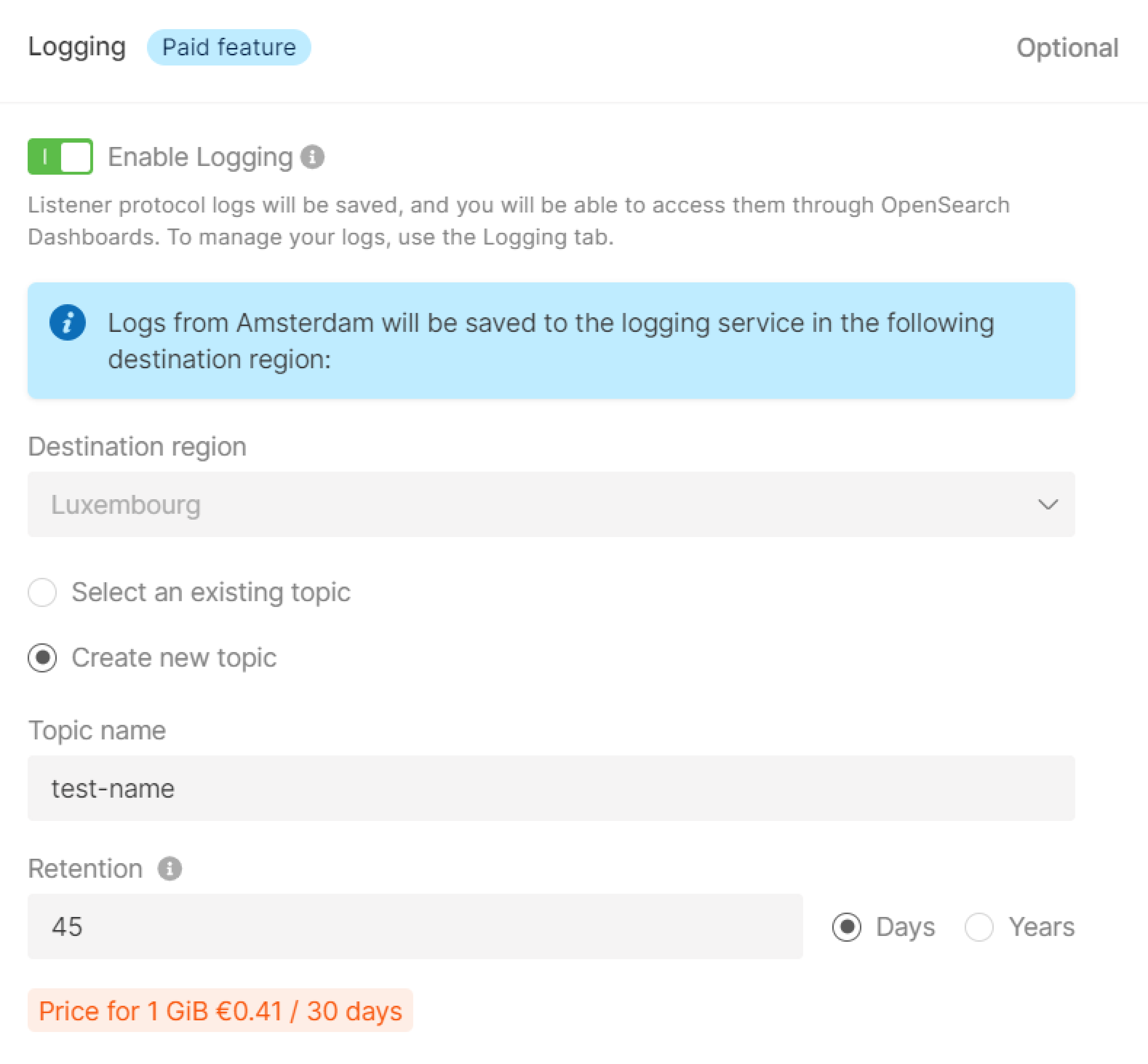
Step 9. (Optional) Configure logging
Managed Logging is a paid feature that allows you to collect and store Kubernetes logs. For more details on Managed Logging, read our dedicated guide. To configure Managed Logging in the Gcore Customer Portal, choose one of two options:- Select an existing topic. If you already use Managed Logging, select this option.
- Create new topic. If you haven’t used Managed Logging before, choose this option and specify the required information.