- Create a Gcore CDN resource for the domain.
- Enable WAAP protection in the resource settings.
- Verify traffic behavior to ensure legitimate requests are not blocked.
Step 1. Create a CDN resource
To secure your web application and APIs with Gcore WAAP, it’s necessary to create a CDN resource associated with your website’s origin. If you also need to add an SSL certificate, check out the Add an SSL certificate to deliver content over HTTPS guide.InfoWhen configuring a resource, you need to update your domain’s DNS records so they point to our network. This is necessary to allow all traffic to pass through WAAP.
- Create a resource with Gcore Managed DNS
- Create a resource with your DNS provider
If you don’t have Gcore CDN configured, follow the instructions from this guide: Create a CDN resource for the entire site.
Step 2. Enable WAAP in CDN resource settings
Once your CDN resource is set up, you can activate WAAP protection for it. Refer to the Protect CDN resources with Gcore WAAP guide for detailed instructions.Step 3. Use WAAP in Monitoring mode
After you enable WAAP, it will be automatically set to the Monitoring mode. In this mode, all incoming requests are inspected, but no action is taken. It’s best to use Monitoring mode for several days before enabling the Protection mode to make sure that all security settings work correctly. Completing this step is important because it allows you to analyze requests and test the WAAP behavior before you fully activate it.Step 4. View your domain traffic
While keeping WAAP in Monitoring mode, you can view all logged requests and check the corresponding actions that WAAP will take once you put it in Protection mode. Go through the Events pages to detect common traffic patterns and understand if the current configuration requires any adjustments. For instance, you can find information about incoming web requests on the Events page in the Requests table:- In the Gcore Customer Portal, navigate to WAAP > Domains.
- Find the needed domain and click its name to open it. You’ll be directed to the Overview page.
- In the sidebar, click Events.
- Review the information under Requests.
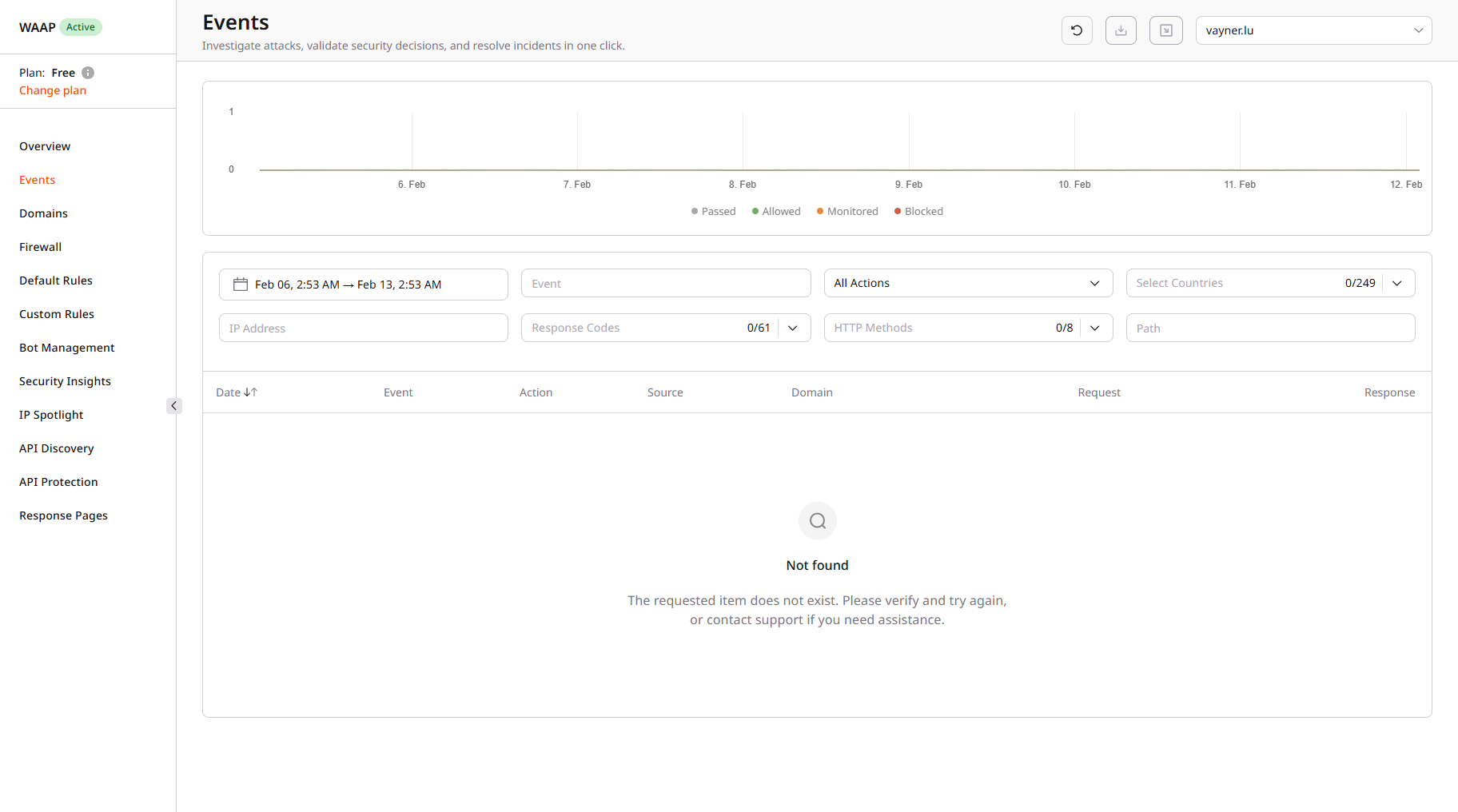
- You can also filter requests to get more granular information about your traffic:
- All Actions: Filter requests by action type (Blocked, Monitored, Allowed, Passed, Captcha, JS Challenge).
- Select Countries: Filter requests by country of origin.
- Response Codes: Filter by HTTP response codes.
- HTTP Methods: Filter by request method (GET, POST, etc.).
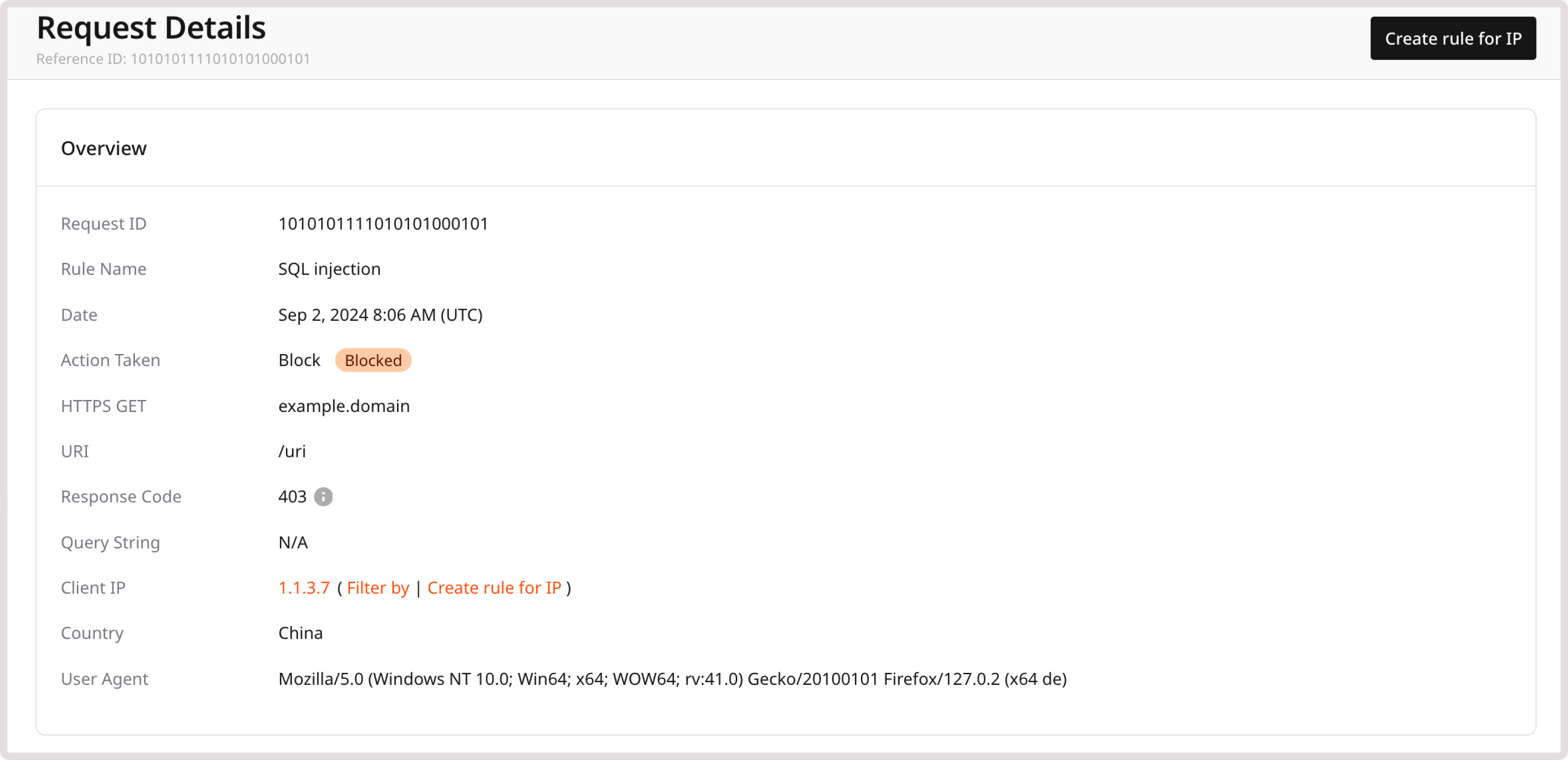
Step 5. Test your WAAP configuration
To achieve the desired WAAP behavior, we recommend that you navigate through your website as both a user and administrator. Navigating the website will generate entries in the Requests table. You can use this information to determine if you need to create Firewall rules or custom WAAP rules for some requests and let them access your website’s content. Specifically, review requests that relate to:- Your origin IP: IP address assigned to your device.
- Your office IP: IP address assigned to your device within your office’s network.
- Your workstation IP: IP address assigned to a workstation or specific computer in a network.
Step 6. Allow admins, bots, and CMS
Before WAAP is in Protection mode, you need to ensure that critical IP addresses, content management systems (CMS), and known bots are allowed to make successful requests. Check the WAAP policy groups for a full list of security policies and their detailed overview.Allow admin IP addresses
If your domain doesn’t use a CMS, we highly recommend allowlisting the site administrator’s IP address:- In the Gcore Customer Portal, navigate to WAAP > Firewall.
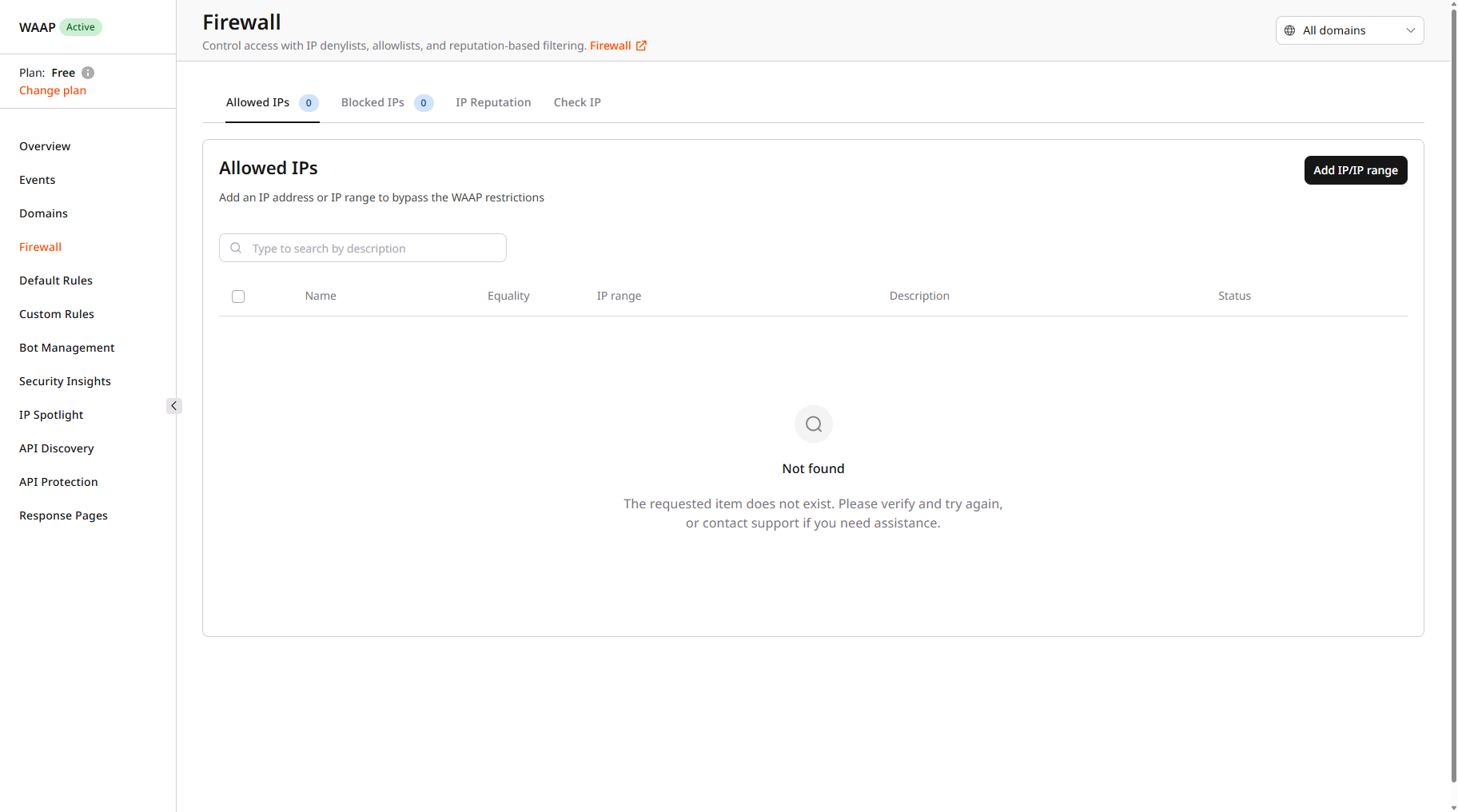
- Select the needed domain from the domain dropdown.
- In the Allowed IPs tab, click Add IP/IP range.
- Enter any admin user’s public IP address.
- Click Save.
Allow CMS
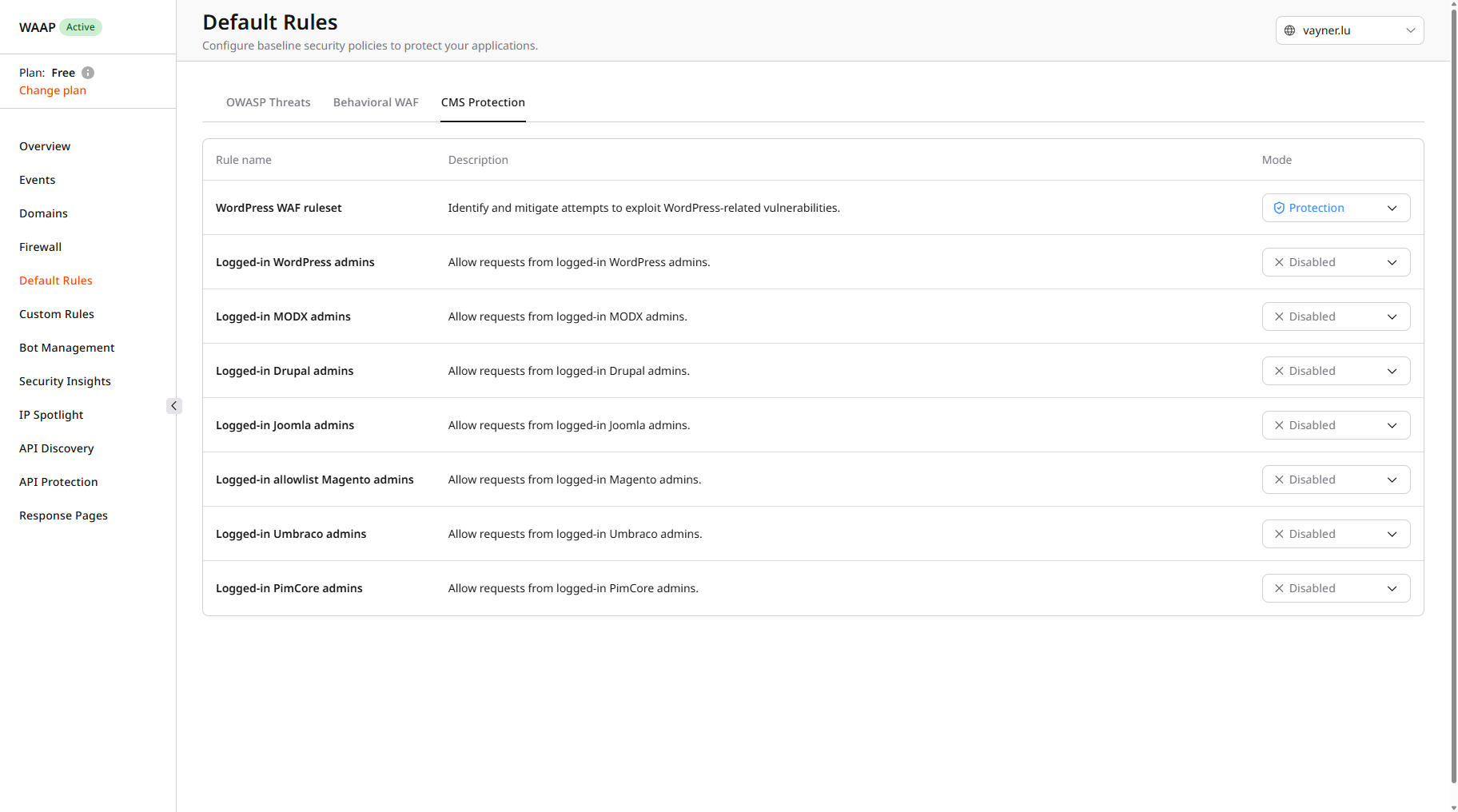
If you use content management systems, such as WordPress, allow traffic for CMS admins:- In the Gcore Customer Portal, navigate to WAAP > Default Rules.
- Select the needed domain from the domain dropdown.
- Click the CMS Protection tab.
- Find the desired content management system and change its mode to Allow by clicking on the mode dropdown next to it.
Allow Known Bots
Follow these steps to allow crawlers, scanners, monitoring bots, and similar tools to access your website:- In the Gcore Customer Portal, navigate to WAAP > Bot Management.
- Select the needed domain from the domain dropdown.
- Click the Known Bots tab and enable the desired bot by changing its mode to Allow.
Step 7. Configure your APIs
If you plan to serve JSON requests through an API on your domain, you can disable the JavaScript injection and CAPTCHA functionalities for specified API endpoints. You can manually add endpoints to API base path or configure the API Discovery feature to automatically detect and protect your APIs.Step 8. Enable Protection mode
- In the Gcore Customer Portal, navigate to WAAP > Domains.
- Find the needed domain in the list.
- In the WAAP domain mode column, click the mode dropdown and select Protection. WAAP will begin to inspect and act upon incoming requests.
Step 9. Block non-Gcore traffic
After successful DNS propagation and verifying that domain-based traffic is being handled by WAAP, ensure that all requests to your domain are routed through Gcore servers. This is necessary to prevent unauthorized traffic from bypassing WAAP and directly reaching your domain.- Add our CDN servers to the allowlist.
- Block other incoming requests that don’t match our allowlist.