Overview
Gcore allows private buckets in S3-compatible storage services, including Amazon and Gcore, as a CDN resource origin. However, to allow CDN servers to access the content stored in these private buckets, you must provide authentication data, including Access Key ID, Secret Access Key, Hostname, and Region. Without this information, the servers cannot access the content.Authentication data
You can find the necessary authentication data in your personal S3 storage account.- Amazon AWS
- Gcore
To locate all the essential keys, refer to the Managing access keys guide.
Configure a private bucket as an origin
- Customer Portal
- API
There are two options for configuring a private bucket as an origin:
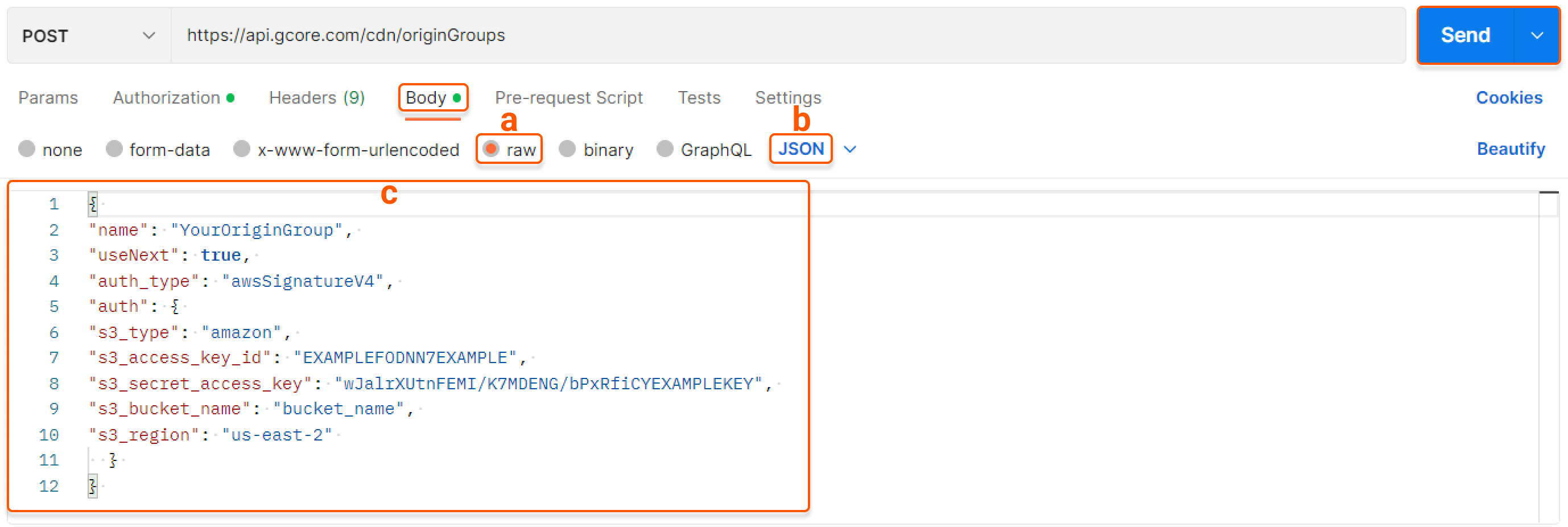
- Create an origin group during the CDN resource creation process;
- Add a group in the “Origins groups” tab and specify this group in the CDN resource setting.

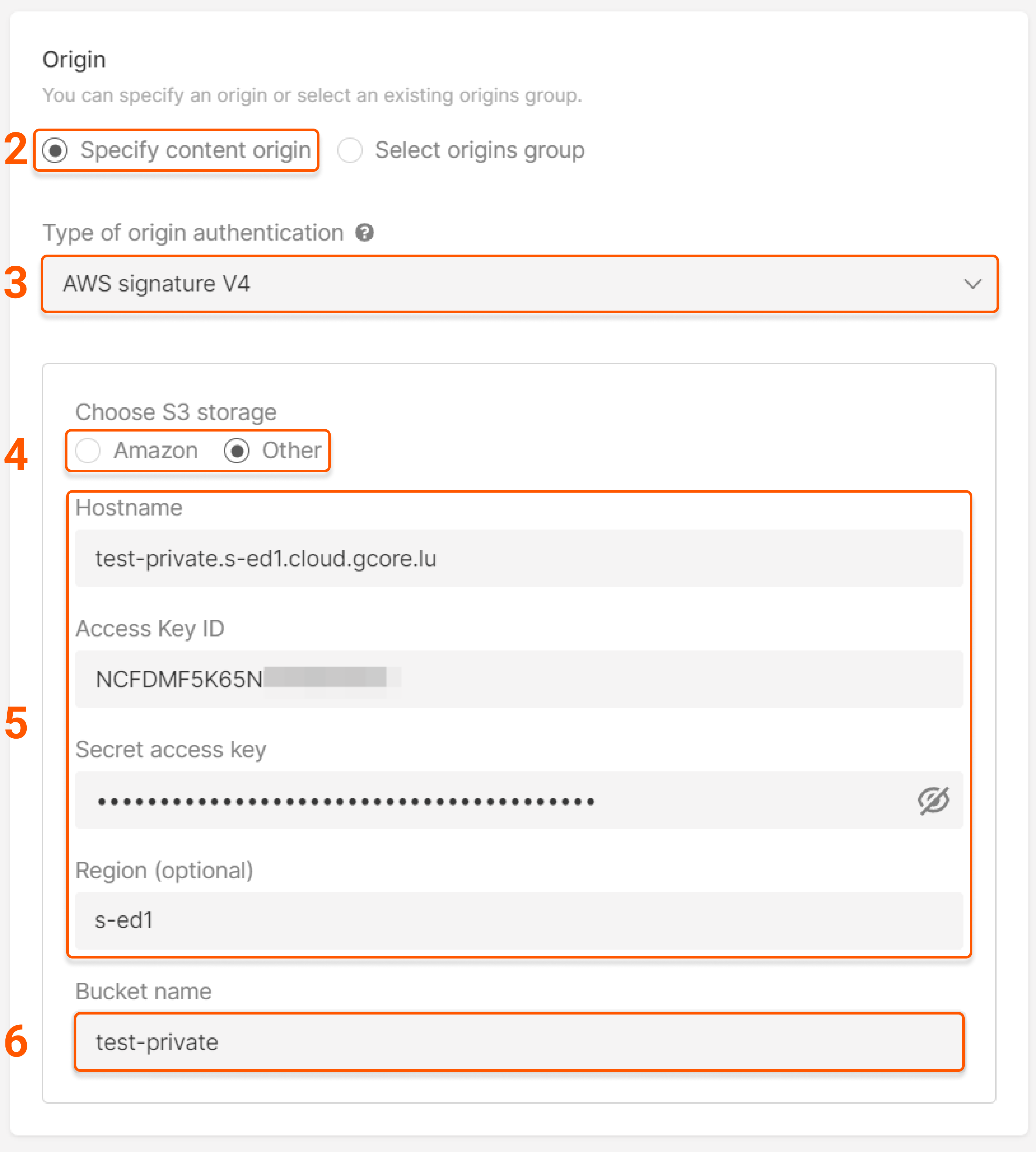
- for Amazon : Access Key ID, Secret access key, and AWS region
- for Other : Hostname (there’s a bucket at the beginning), Access Key ID, Secret access key, and Region
test-private in Gcore Object Storage with the endpoint (service URL) s-ed1.cloud.gcore.lu. Configure an origin group as follows:
- For Gcore Object Storage:
{bucket-name}.s-ed1.cloud.gcore.lu - For most other storages (including Amazon):
{bucket-name}.s3.{region-code}.{storage-hostname}

Troubleshooting Amazon S3 (403 Forbidden for HEAD requests)
When using private buckets in Amazon S3 storage as an origin, you might encounter a 403 Forbidden error for HEAD requests intended to retrieve metadata. However, a GET request may operate without any errors and return a 200 OK status. The disparity in the results of these requests can be attributed to several causes:- Restricted object-level permissions: If the buckets or IAM policy permits public read access but the object’s Access Control List (ACL) denies access to your user or role, AWS S3 will return a 403 status for HEAD requests.
- Different policies in effect: If the user making the HEAD request doesn’t have the necessary permissions to read the object’s metadata, AWS S3 will return a 403 status for HEAD requests.
- Incorrect parameters in presigned URLs: If a presigned URL for a HEAD request was generated with incorrect parameters, AWS will return a 403 error. The parameters for URL generation (access key, secret access key, bucket name, object key, etc.) must be consistent for both HEAD and GET requests.
- Different owners for bucket and object: If the bucket and object belong to different AWS accounts and the object owner hasn’t granted the necessary permissions to the bucket owner, AWS will return a 403 error for a HEAD request and a 200 status for a GET request.