

Today, we’re publishing the final article with the results of the research “World Video Games Industry 2020–2023: Trends, Technologies, Challenges” conducted by Gcore and the Censuswide British research agency. Representatives of 50 large, medium, and small video game developers from the USA, Great Britain, and EU took part in the survey.
The first two articles were dedicated to the existing and future technologies that are in demand among video game developers, and to the gaming industry’s plans and drivers after the pandemic.
In the third article of this series, we’ll talk about how DDoS attacks affect the game development industry, the most dangerous types of these cybercrimes, and the best methods of countering them.
How do DDoS attacks affect game industry businesses?
Among the key factors that could adversely affect business prospects over the next 3 years, 66 % of respondents indicated cyberattacks, including DDoS attacks, and changing user preferences. Also, the increase in the number of competing products and companies may become a barrier to revenue growth, which will lead to a market glut (64 %).

According to many respondents, the trend of further migration of leisure and entertainment online will continue, and the pandemic has acted as a catalyst for this process. In connection with this, 78 % of respondents said they plan to enter new markets (countries or regions).
At the same time, new markets mean new challenges. Among the main issues that had to be solved while developing business in foreign regions, representatives of game companies noted the growth of DDoS attacks on IT infrastructure (46 % of respondents) and issues with Internet connectivity and bandwidth in the local market (38 %).

“Our experience confirms these studies. Gcore regularly provides cybersecurity services for game companies that enter new markets. One example is RedFox Games, an American video game developer and publisher that gave us such hits as Black Desert, RF Online, and Rumble Fighter. In North America, where the company’s project audience is more than 5 million players, RedFox Games is quite successful, but even experienced teams can find it difficult to introduce their projects to emerging markets. That’s why, when RedFox Games had decided to launch Black Desert in Latin America, they contacted us. Before RedFox Games went to Latin America, there were already Black Desert pirate servers. While the project was in Closed Beta testing, large-scale DDoS attacks hit the network with peak loads up to 300 Gbps. These attacks lasted for a week. The pirates had a profitable business, and with the help of DDoS attacks, they tried to show their users that a US publisher wouldn’t be able to provide a quality service. Thanks to high-end, Kinetic-based equipment and using local cleaning centers, Gcore easily repelled all attacks.”
Vice President of Products at Gcore
Sam Davis
34 % of study participants face DDoS attacks every two months, while another 52 % of game companies fight them at least once per quarter or half-year.

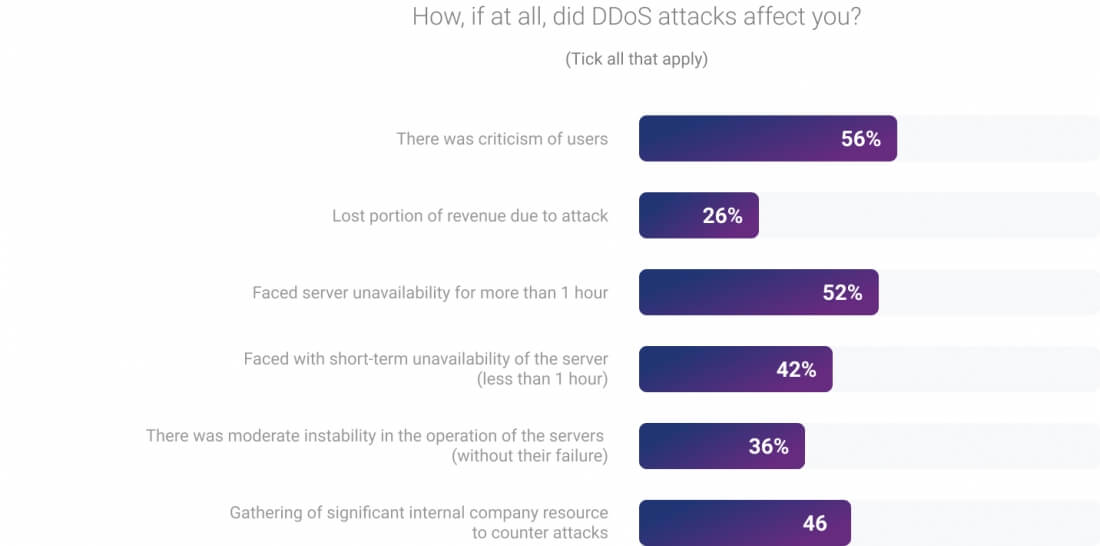
The main consequences of DDoS attacks for survey participants were criticism and a decrease in user loyalty (56 % of respondents), unavailability of their games for more than one hour (52 %), and allocation of significant internal company resources to counter attacks (46 %). Also, 26 % of respondents noted direct financial losses as a consequence of DDoS attacks.
“Not all companies are ready to admit that they lose money because of cyberattacks. We know though that for larger publishers with an audience of, let’s say, 3–5 million players, each successful DDoS attack lasting less than an hour results in about €15,000–25,000 of lost profit.”
Vice President of Products at Gcore
Sam Davis
The most effective types of DDoS attacks
Cyberattacks evolve regularly, but attackers are particularly interested in certain methods because of their high efficiency. The most serious incidents, both now and in the near future, are associated with several types of DDoS attacks, such as Generated UDP Flood, DNS Reflected Amplification, and Burst Attack (Hit-and-run).
Generated UDP Flood
Generated UDP Flood combines the generation of excess traffic and elements of protocol-layer attacks.
The attack sends UDP packets from fake IP addresses to a targeted IP address and server port. With a correctly-selected packet parameter and intensity of sending, it’s possible to simulate legitimate traffic. Identifying junk requests then becomes extremely difficult.
Such an attack was carried out against the server of the Albion Online game developed by Sandbox. As a solution to eliminate the threat, a Gcore software package was selected and it successfully repelled the attack.
This solution combines several methods:
- Rate Limiting—limitation on traffic
- Regexp Filtering—filtering packets that coincide with regexp in payload
- Whitelisting—adding authorized player IP addresses to a whitelist
- Blacklisting—adding unauthorized player IP addresses to a blacklist
- IP Geolocation Filter—blocking IP addresses based on geolocation
- Challenge Response (CR)—a unique protocol that is integrated on the client’s side and that allows IP address validation
DNS Reflected Amplification

The essence of this attack is a combination of two malicious factors. First, the attacker simulates a request from the targeted server by putting its IP address into the request, ultimately using a public DNS server as a “reflector.” The DNS server receives the request indicating the targeted server and returns a response to it, thus “reflecting” the request.
Moreover, you can request not only the IP address of the domain, but also much more data, and therefore the response of the DNS server will become much more voluminous. Finally, traffic can be maximized by querying through a botnet. Thus, it is highly likely that the bandwidth of the targeted server will be overloaded.
The most famous use of DNS Reflected Amplification was the attack on GitHub in February 2018. The traffic flow reached 1.35 Tbps, and the gain ratio (amplification) reached 51,000.
Burst Attack (Hit-and-Run)
Hit-and-run attacks work in a special way that differs from most other attacks. These are short bursts of traffic with a volume of hundreds of Gigabits per second, sometimes lasting 20–60 minutes or even less than a minute. They are repeated many times over a long period—sometimes days or even weeks—at intervals averaging 1–2 days.
Such attacks gained popularity because they’re cheap. They are effective against protection solutions that are activated manually. The danger of hit-and-run is that constant protection requires continuous monitoring and availability of response systems.
The main targets of hit-and-run attacks are online game servers and service providers.
How to protect yourself from DDoS attacks: 3 steps to system security
Cybersecurity is a narrow competency that can hardly be covered as easily as HR or accounting, no matter how advanced the company is. It’s important to ensure that your service and infrastructure providers are deeply immersed in cybersecurity issues and have established themselves as true professionals.
Reliable protection is ensured by taking these 3 steps:
- Using a proven solution for continuous DDoS protection
- Creating a DDoS Response Plan
- Conducting regular system health checks and eliminating application vulnerabilities
“For protection against DDoS attacks, Gcore offers a smart, constant, all-in-one solution for highly effective mitigation of modern and future attacks of any complexity and volume for servers, websites, and applications without affecting business processes and infrastructure costs. The Gcore solution is based on unique smart traffic filtering technology that works in real time. This technology combines the analysis of statistical, signature, technical, and behavioral factors. When DDoS attacks occur, the Gcore service doesn’t block IP addresses. Only specific malicious sessions are cut off.”
Vice President of Products at Gcore
Sam Davis
To read the full research results for free, please provide your name and email address.







